Introduction
RSABias is a web presentation of research focused on bias in RSA keys. It contains examples of practical bias usage for estimating an origin of RSA keys in large IPv4 certificates scans and classification of few keys from user.
Try our online classification tool with your own public RSA keys and look, what are possible source, that could generate the keys.
If you would like to know more, go to the Q&A section or visit web pages of original research:
Continuous monitoring
We continuously monitor the popularity of cryptographic libraries from large scans done by Rapid7 and from Certificate Transparency Rocketeer log.
Online classification
Morphology of your RSA public keys
Morphology of your RSA public keys
RSA public keys
Most probable source/s
Results accuracy
Negative results
Morphology of your RSA public keys
We think that your separate key(s) were generated by (sorted from the most probable)
| Group name | Sources |
|---|
Q&A section
Q: So what did you do?
A: Figured out that RSA public key is leaking info about a library which created it. So we can tell which library you used for your key - based on public key only.
Q: Is single key enough to identify source library?
A: Sometimes yes, but mostly no. If you have 5 keys from the same source, it will be quite accurate. Just press Classify button above.
Q: Can I mutually distinguish all libraries?
A: Not always. Source libraries introducing exactly same bias to the value of generated public moduli will be undistinguishable.
Q: Can I identify also the version of used library?
A: Sometimes. The new version of a library that did not change source code of key generation method will not be distinguishable from the older one. E.g., OpenSSL 1.0.2f is not distinguishable from OpenSSL 1.0.2g, but OpenSSL 1.0.2g is distinguishable from OpenSSL 2.0.12 FIPS.
Q: Have you tested all libraries of the world?
A: No. We test a lot of them, but not all. We also did not test all possible version of given library. We are also missing hardware sources like SSL accelerators (contact us please, if you have one and like to contribute).
Q: How quickly will be the information leakage vulnerability you found fixed?
A: Probably not soon. The fix would require changing code of key generation method for the most libraries. And developers don't like to mess with that part of crypto too often. Even if fixed in the new version, lot of old legacy libraries will use for a long time.
Q: So how can I protect my key(s)?
A: If you need just one key, it is easy - just generate 5 keys instead of one, let all to be classified by our tool and then keep the one which is classified with the least accuracy. If you need more keys to keep, it is slightly more tricky, but still can be done (with more keys generated and discarded).
Q: Are data you gathered and used publicly available?
A: Definitely! Download everything in datasets section and try own analysis. Please don't forget to cite us.
Q: I want to know more details!
A: Great, then read original paper and technical report for even more details.
Known sources of RSA keys
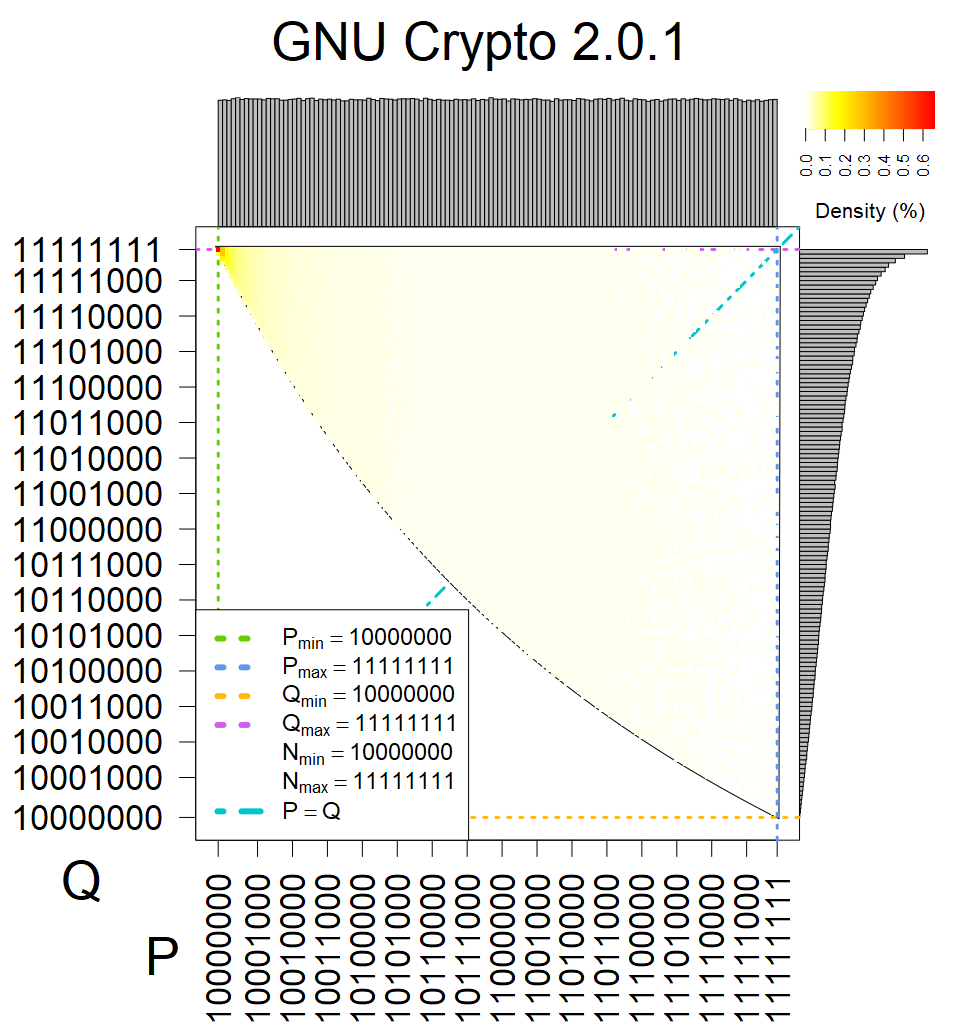
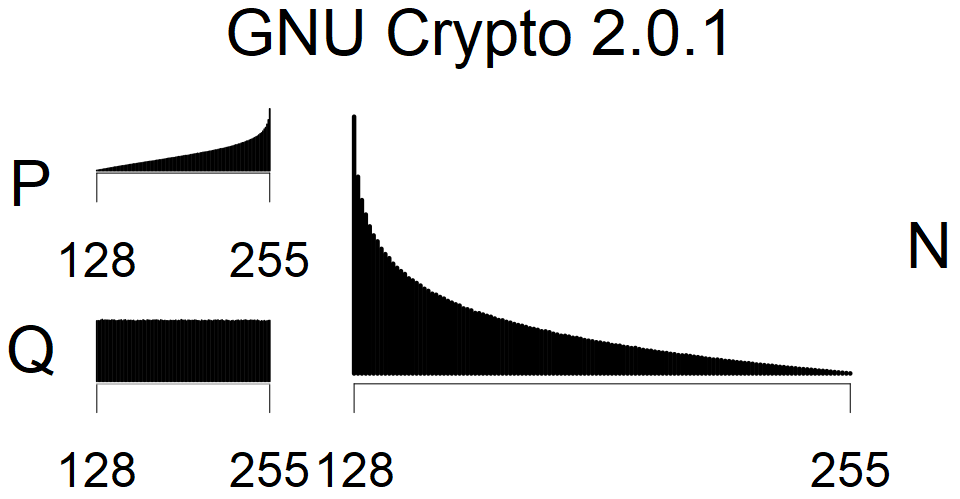
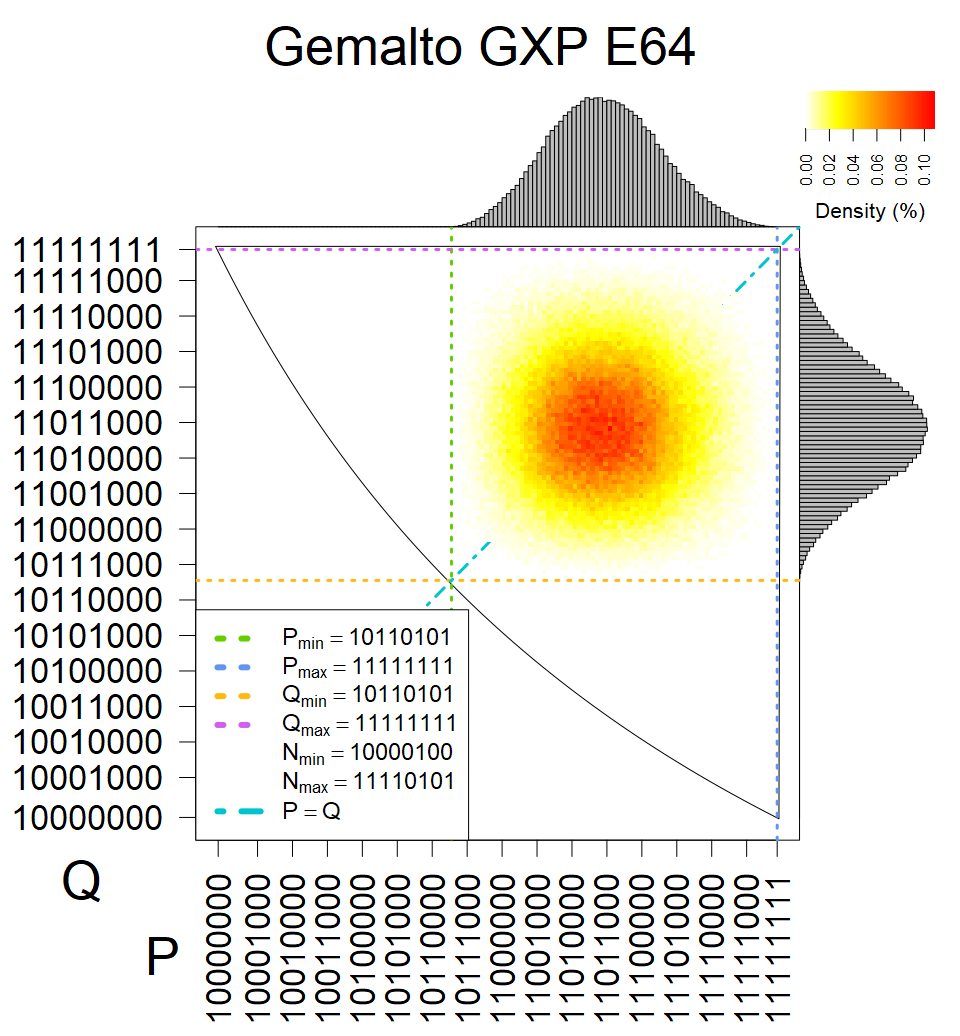
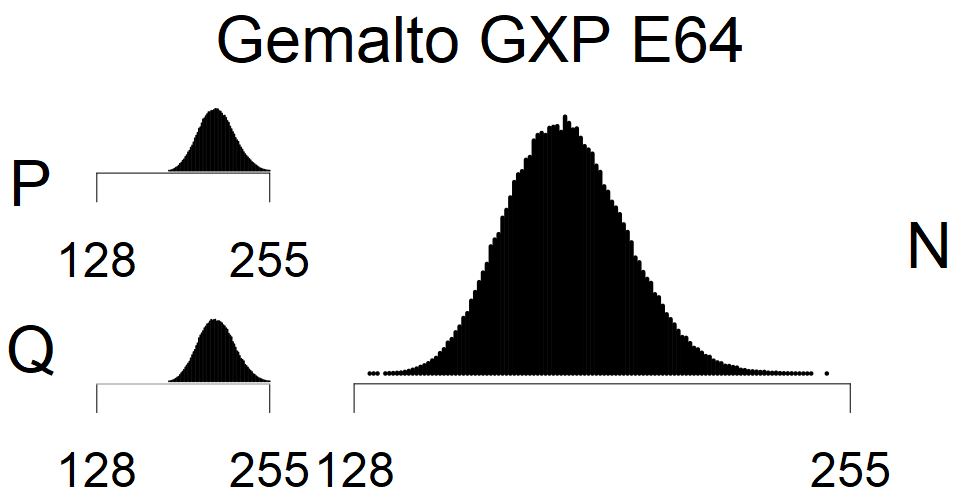
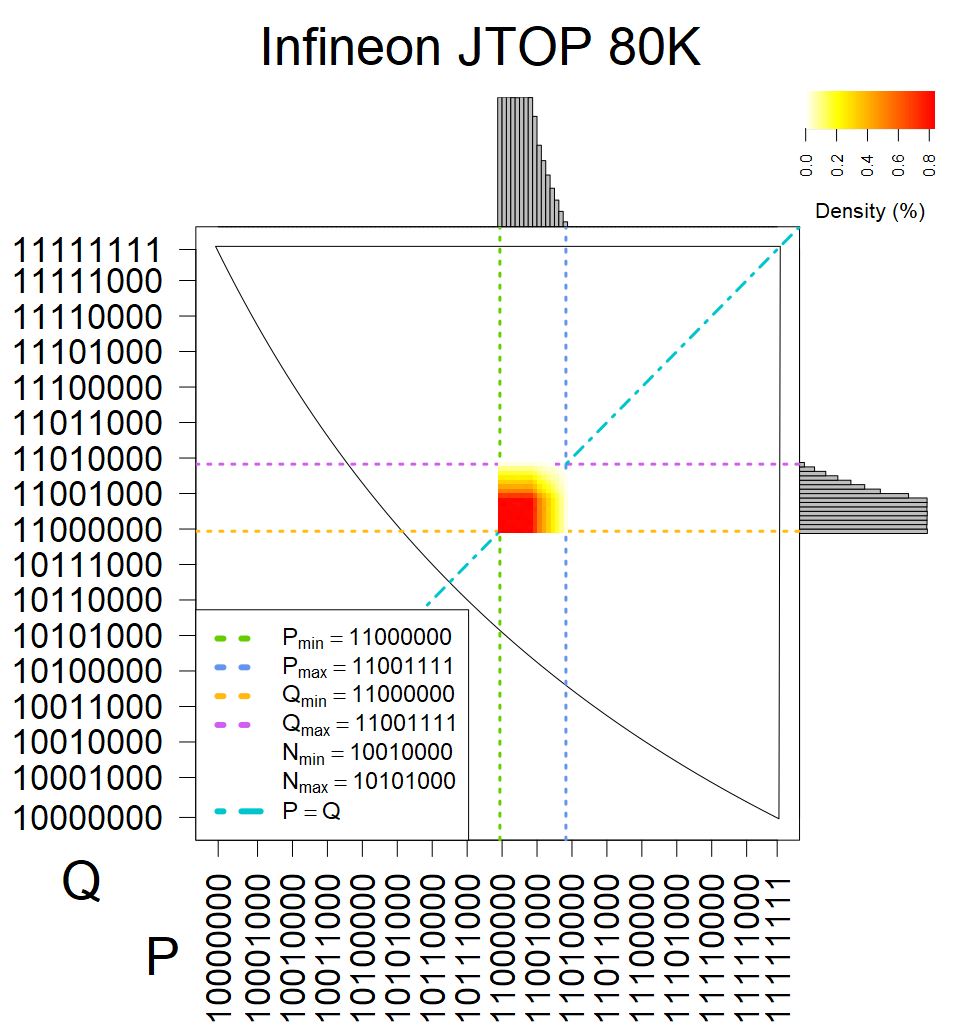
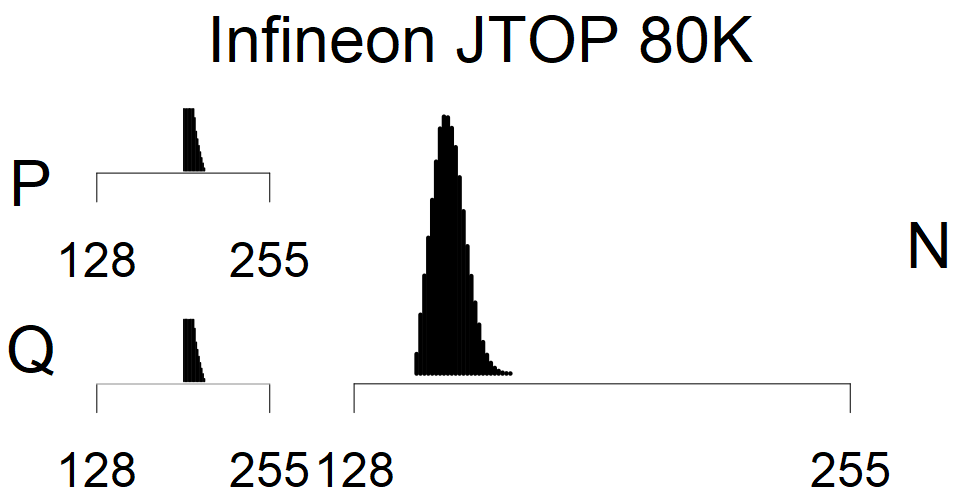
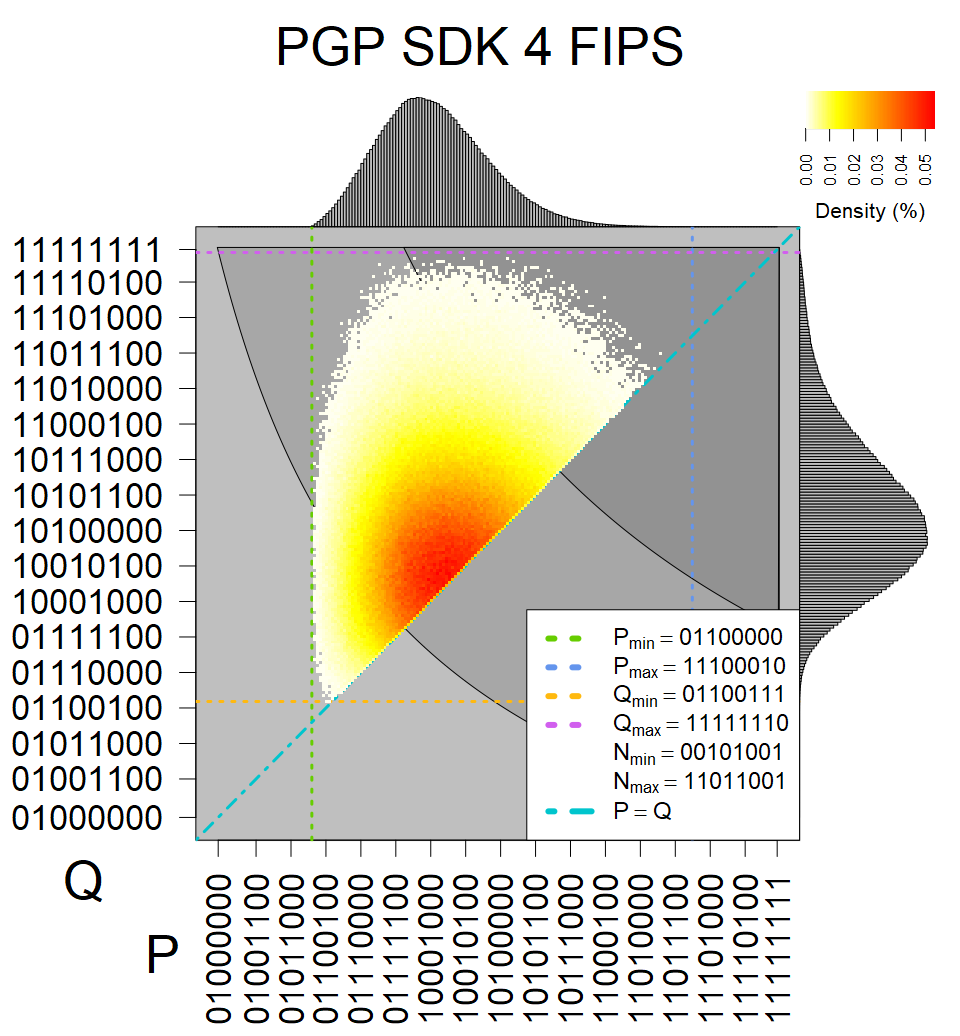
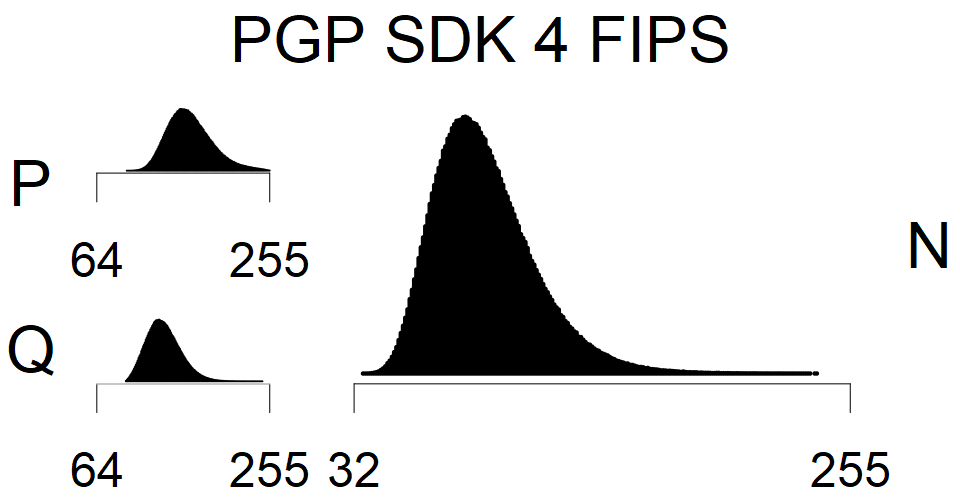
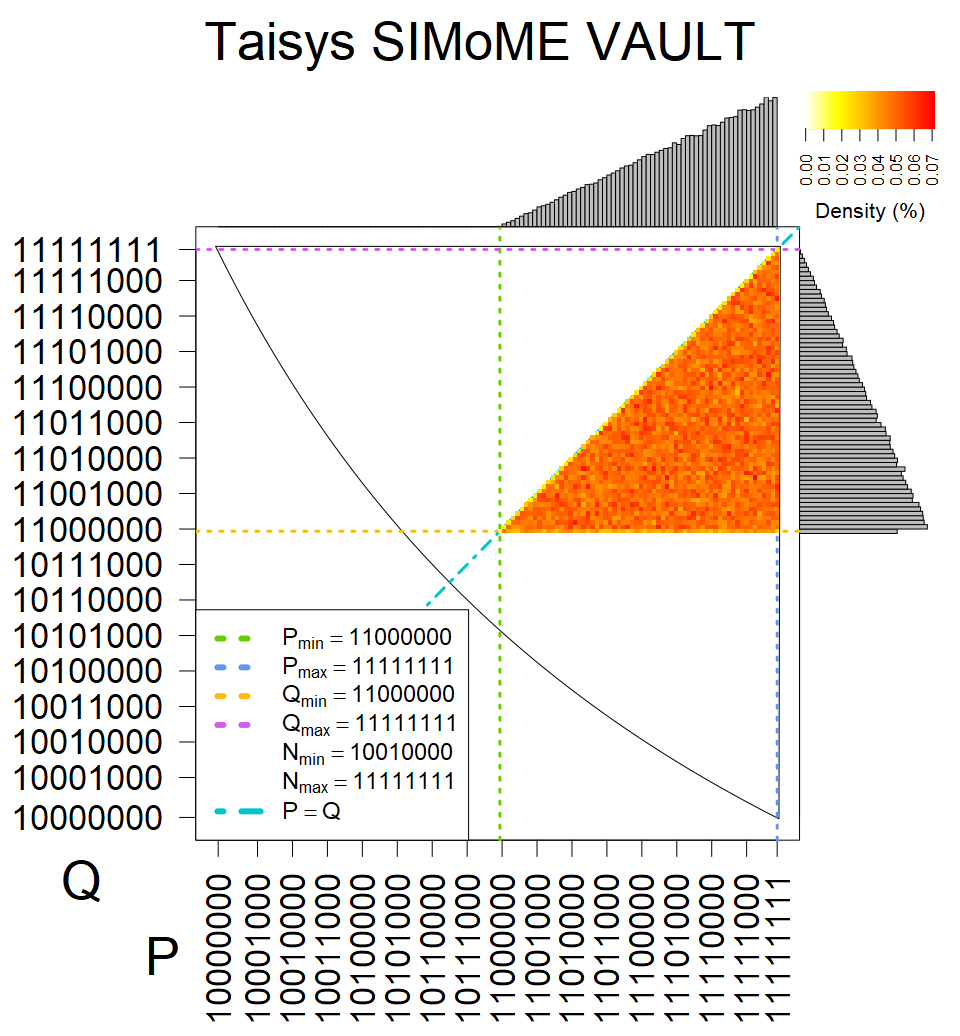
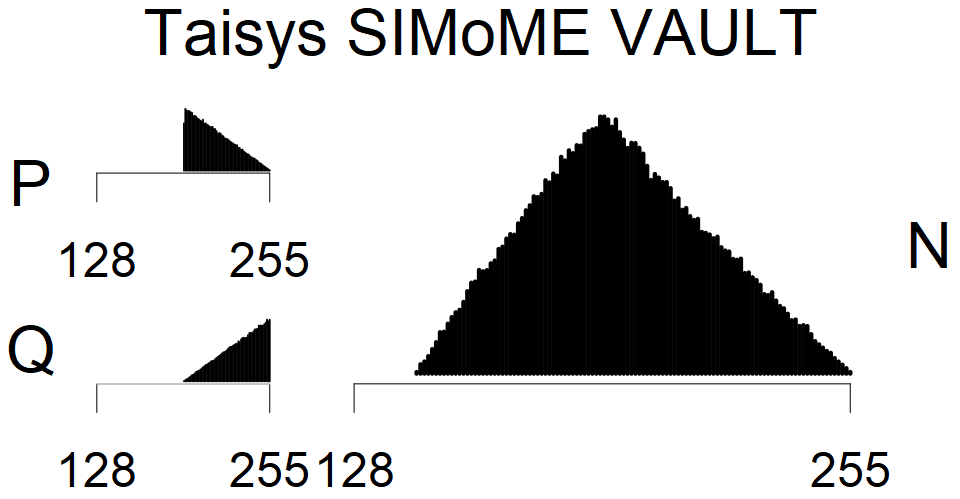
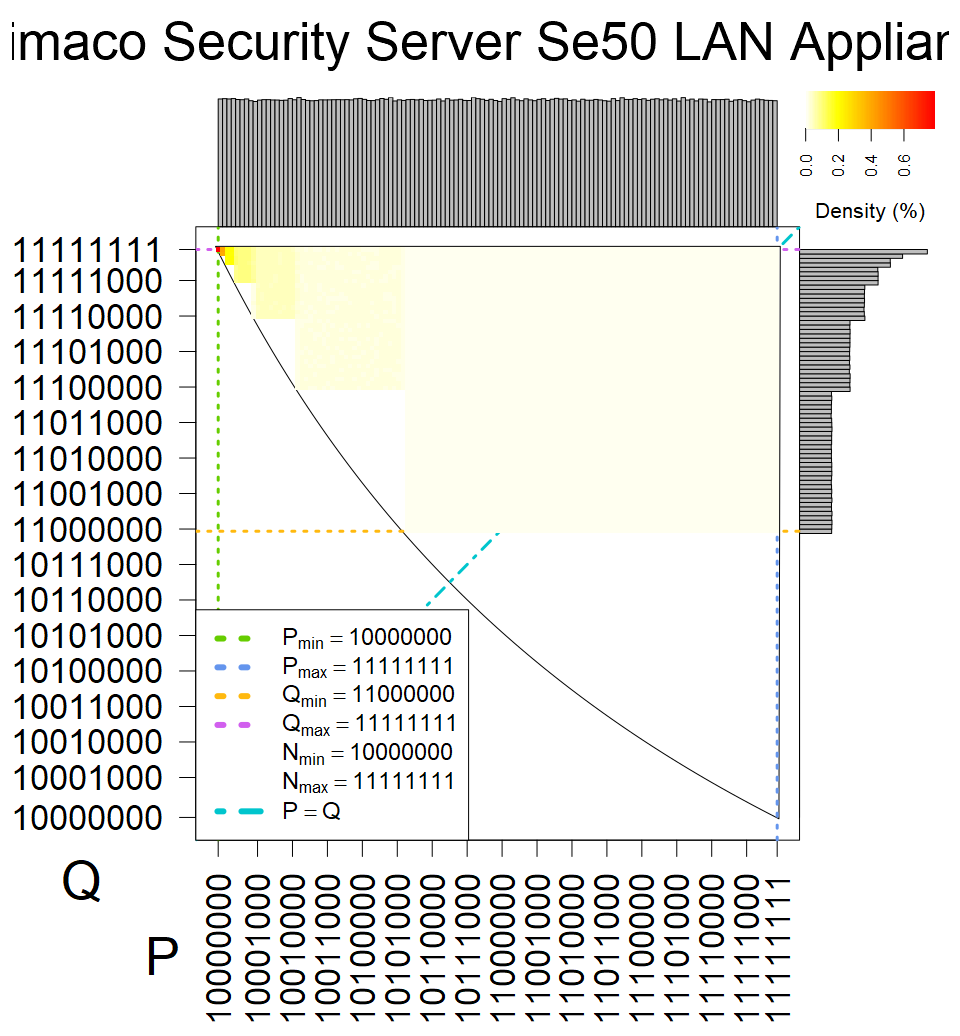
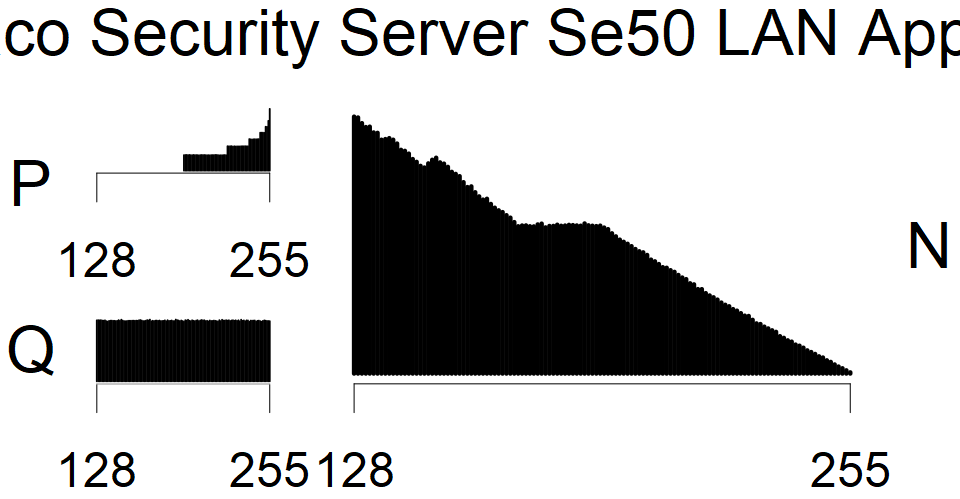
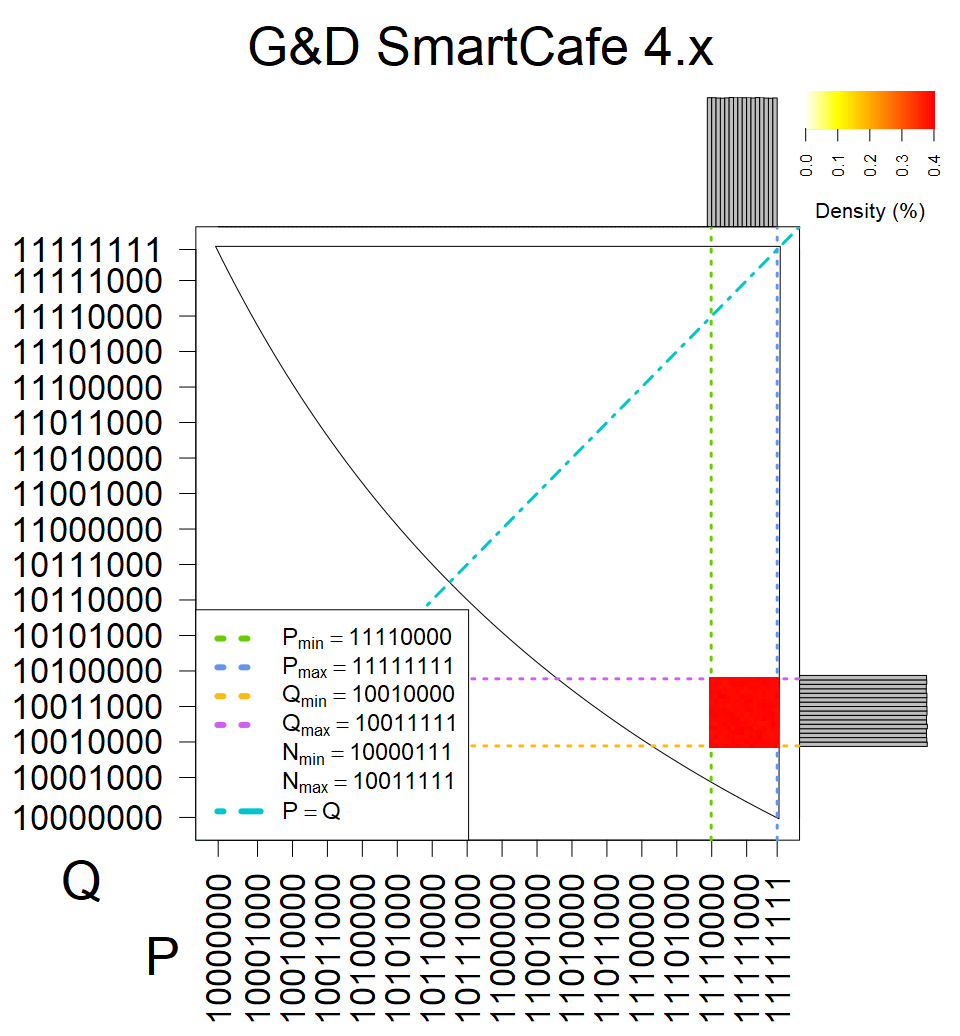
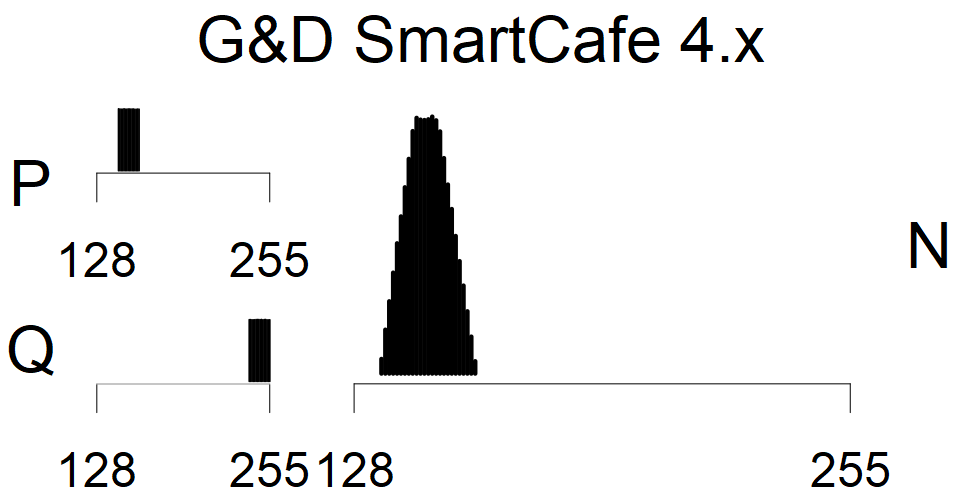
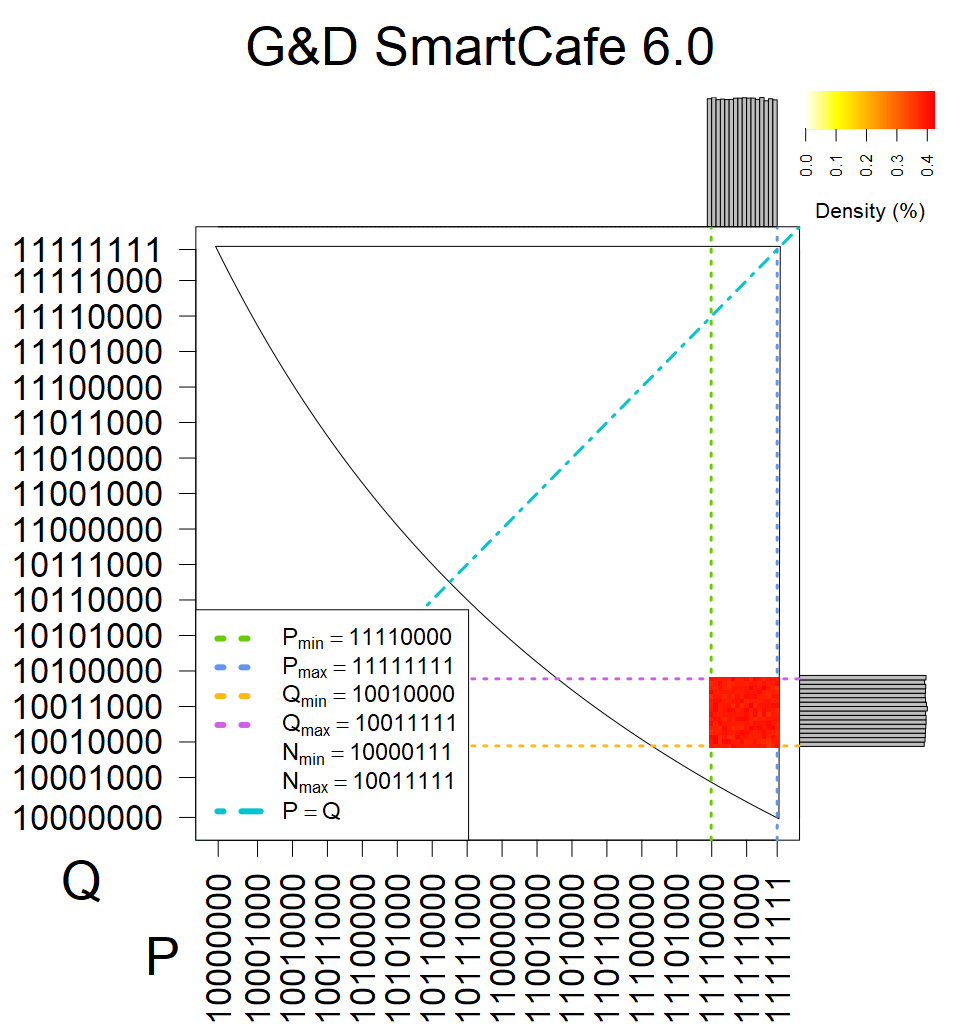
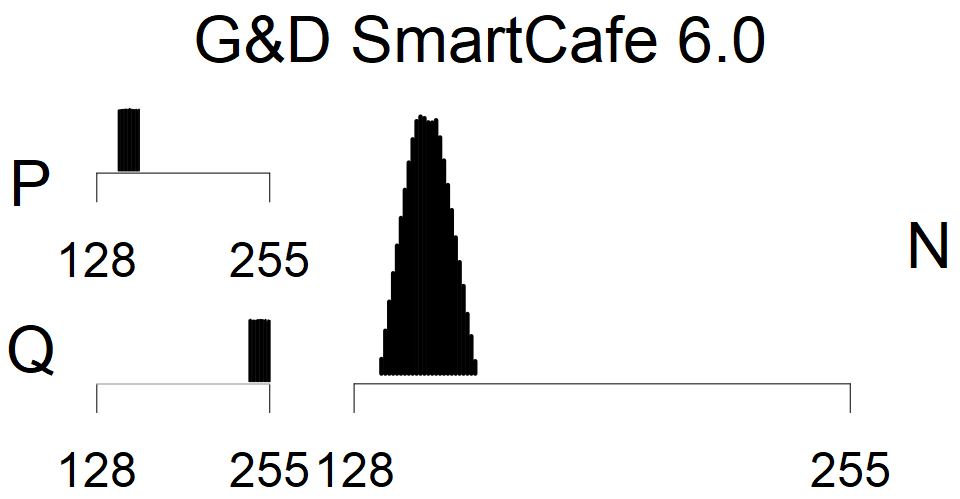
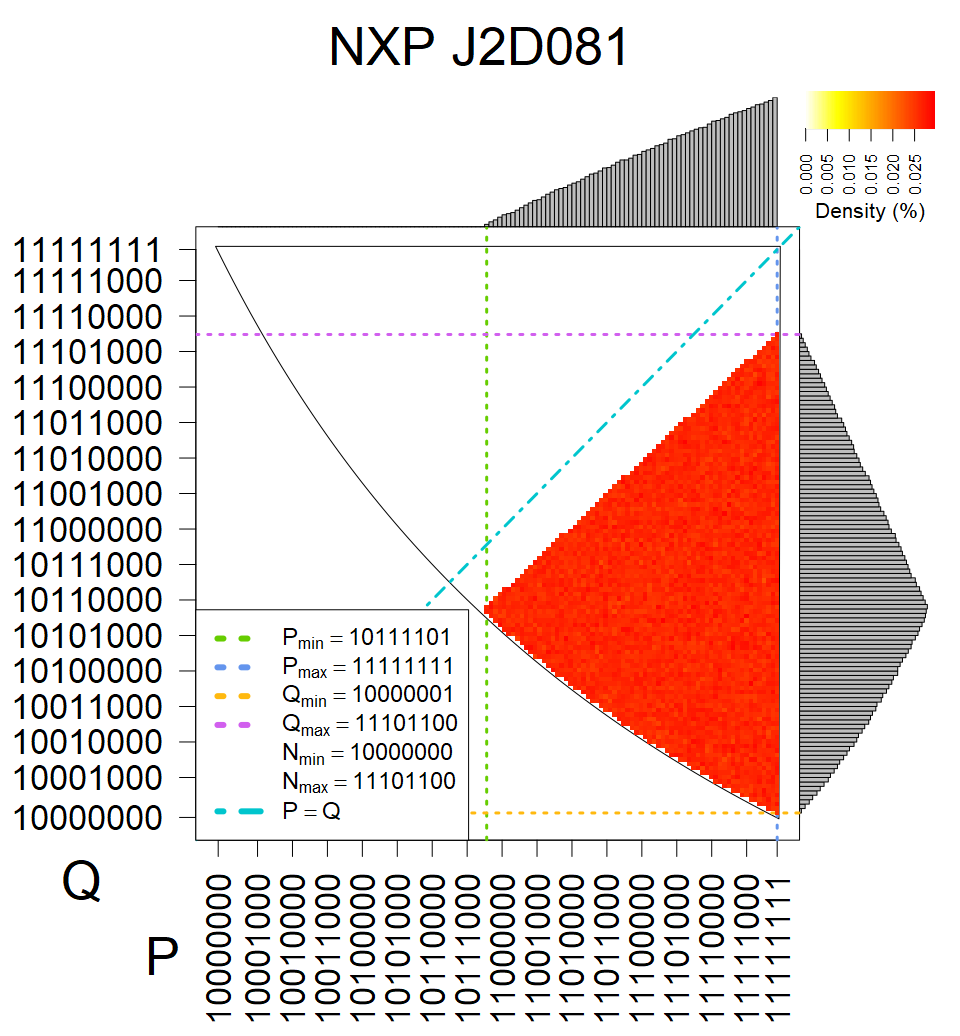
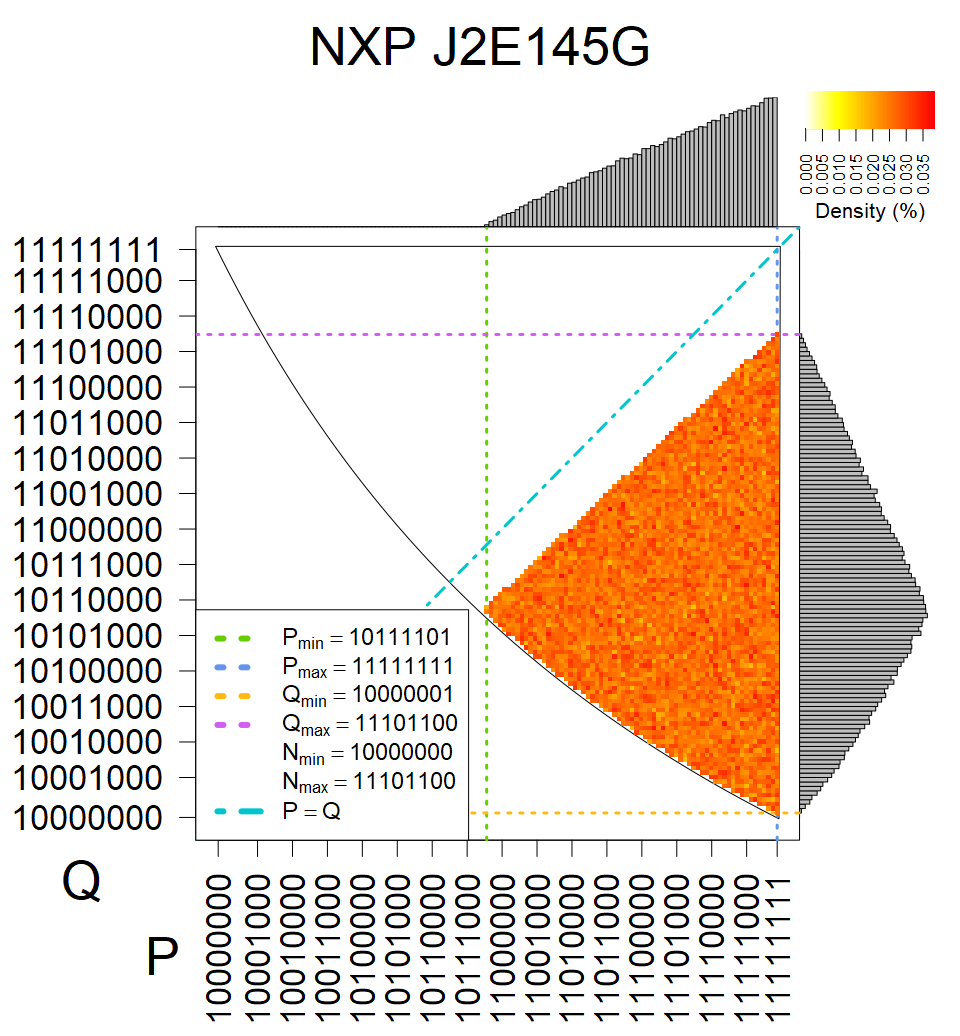
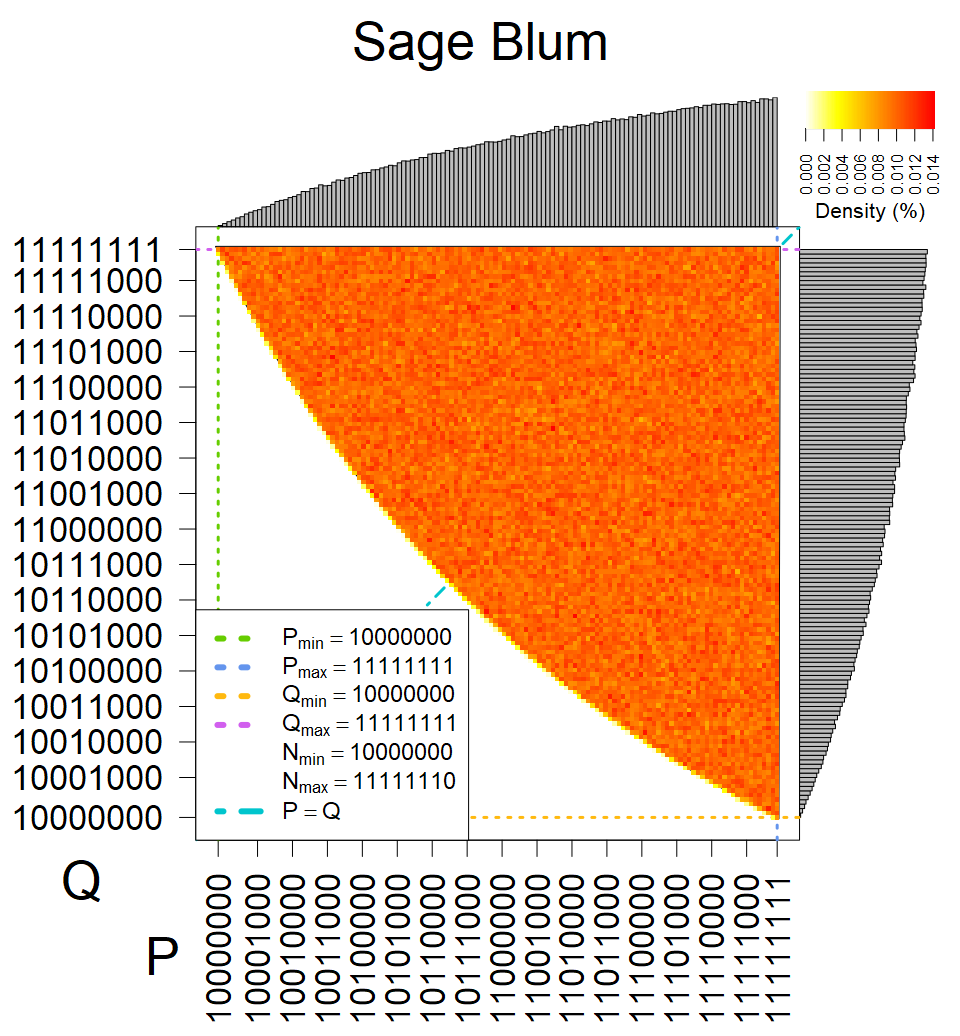
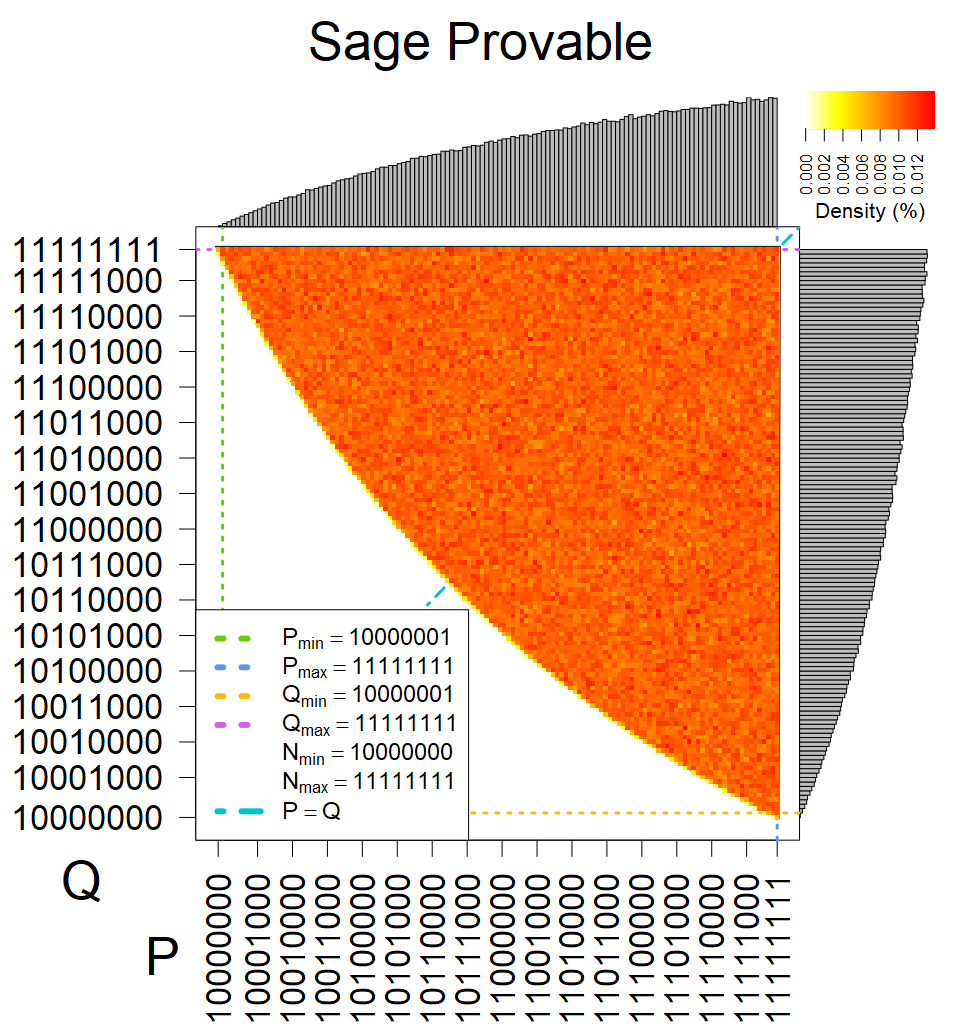
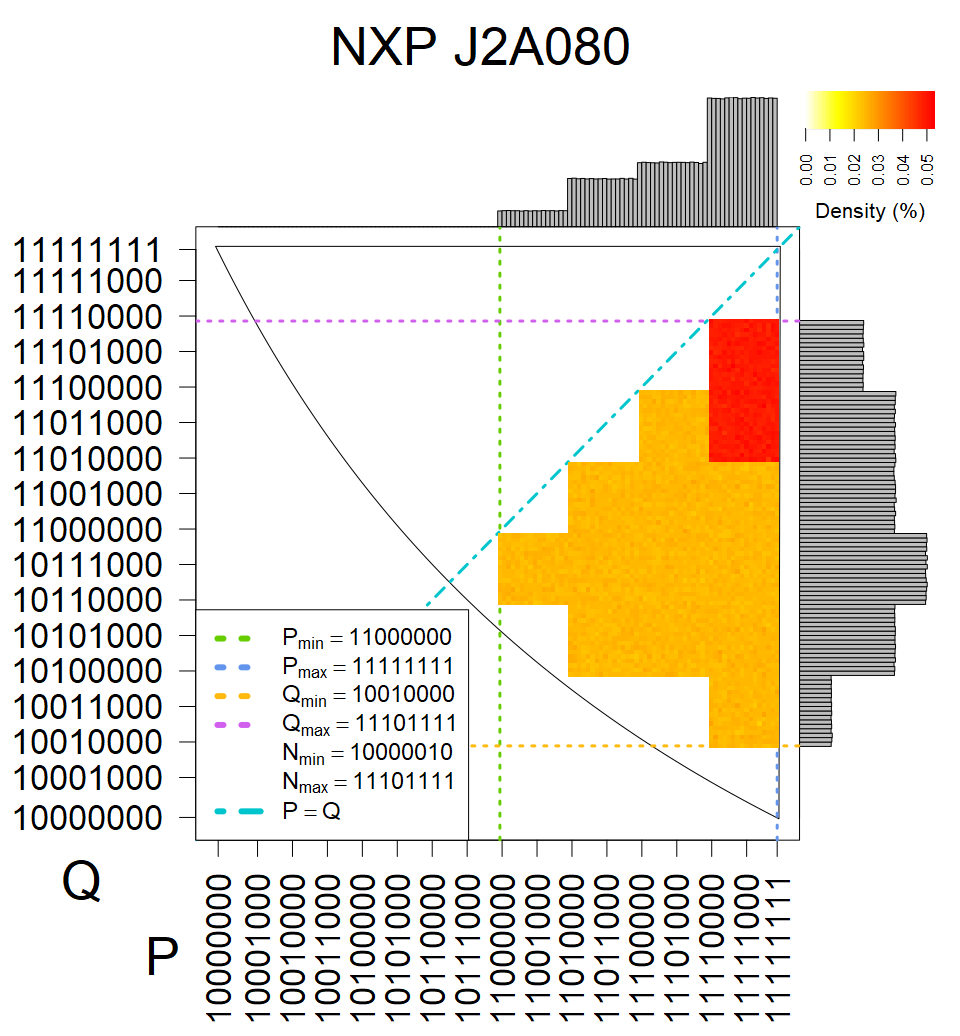
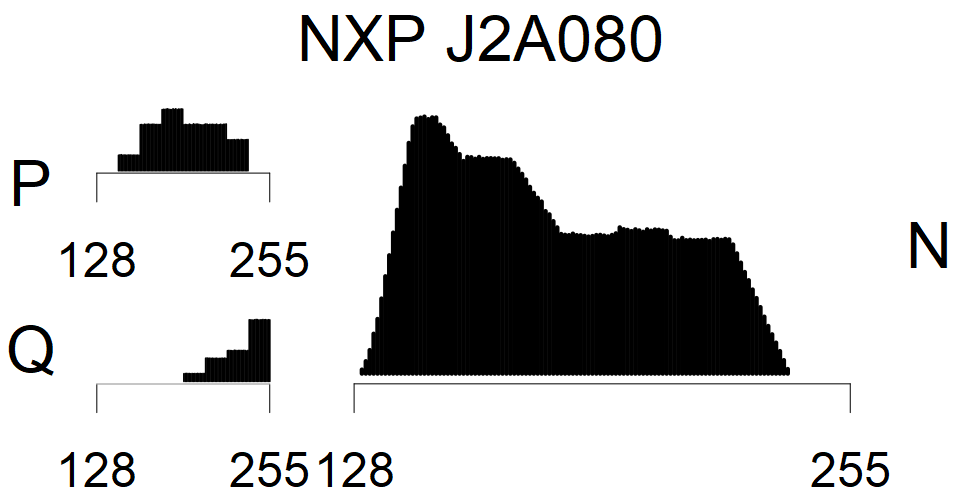
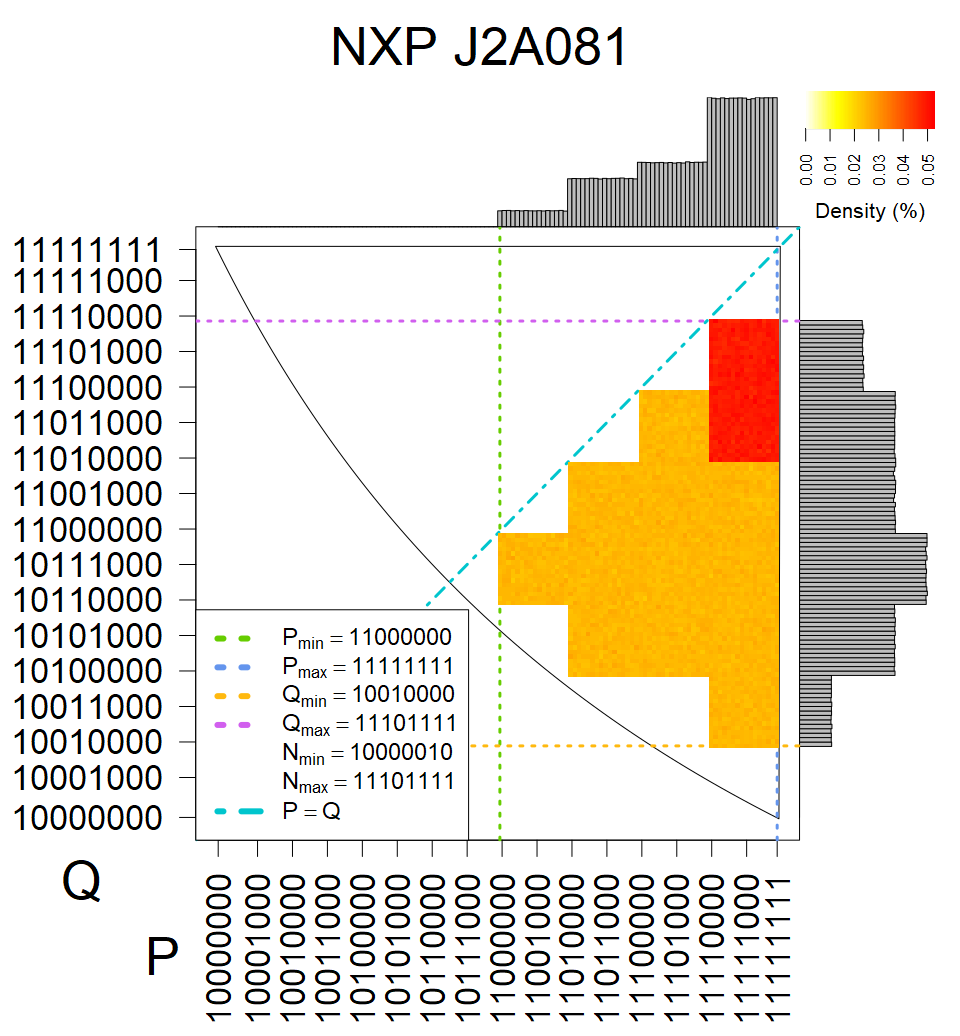
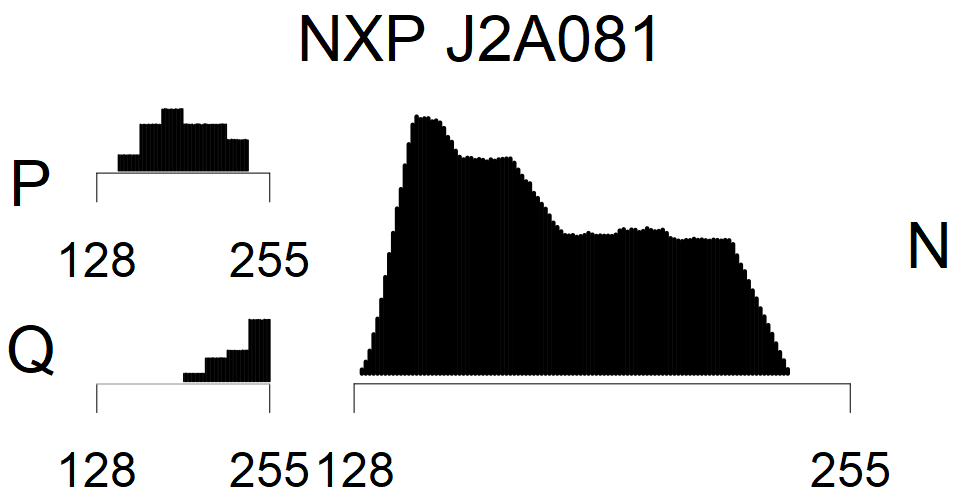
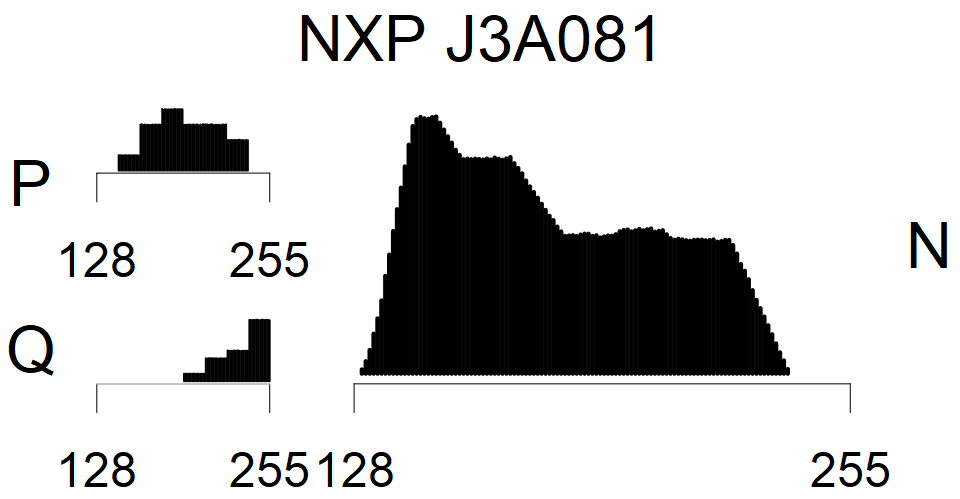
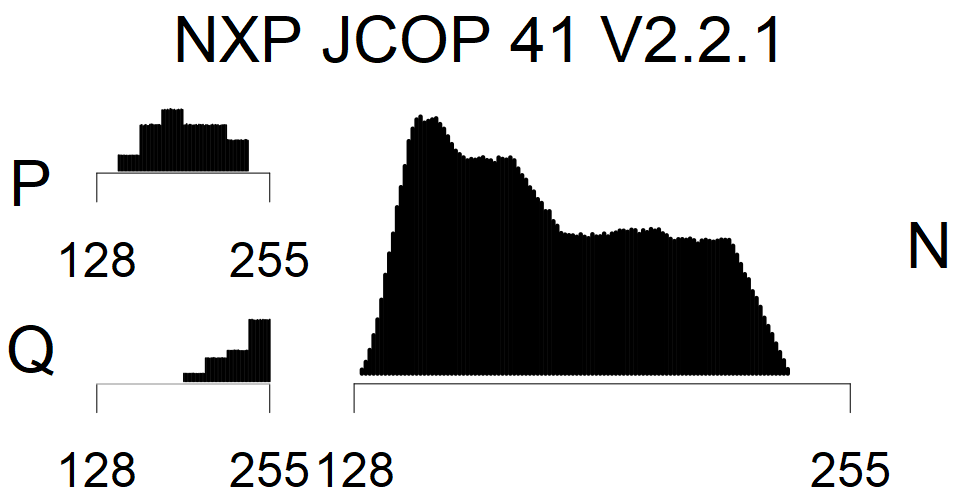
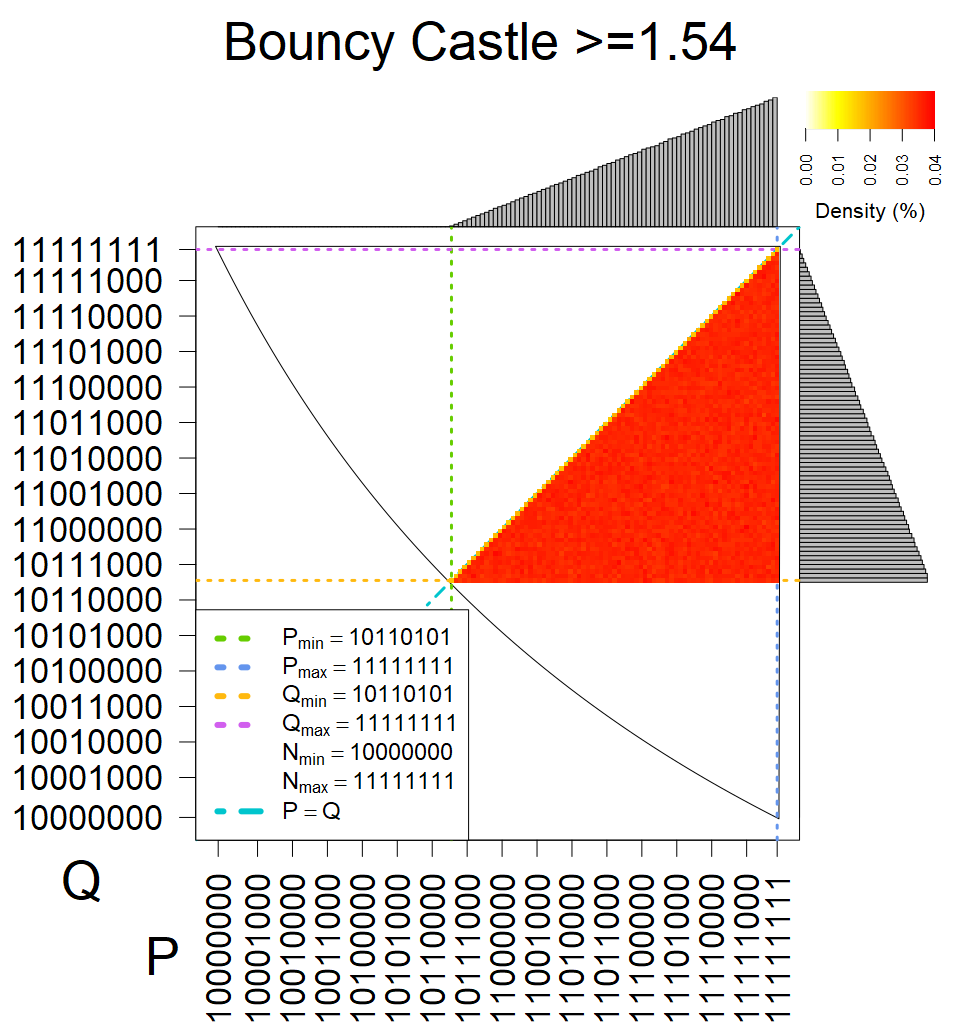
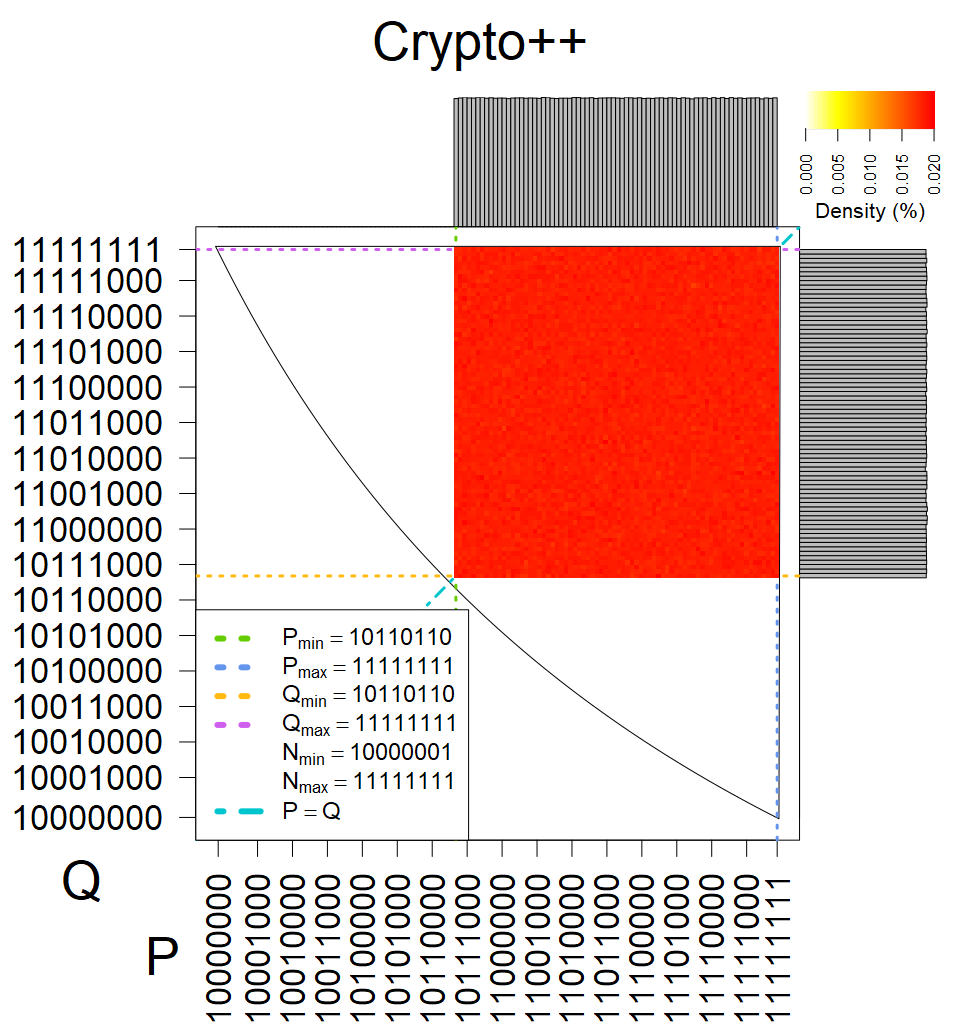
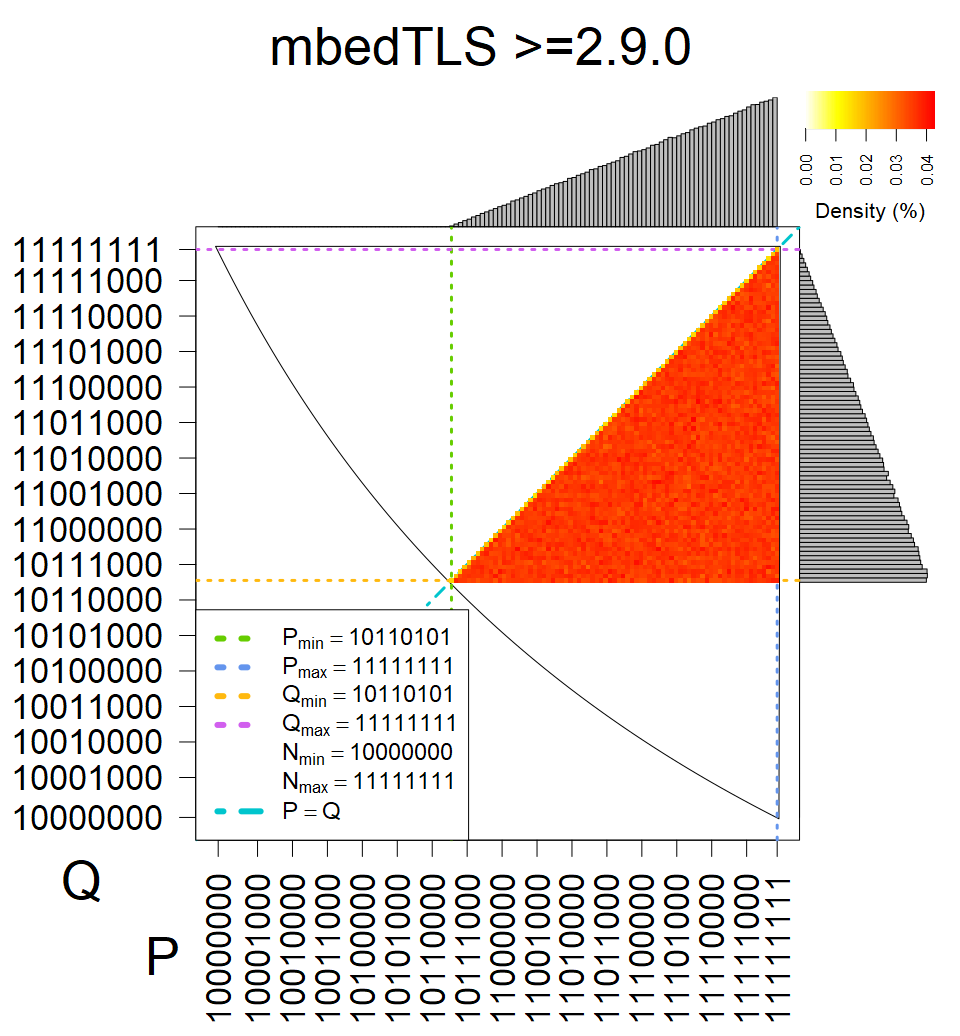
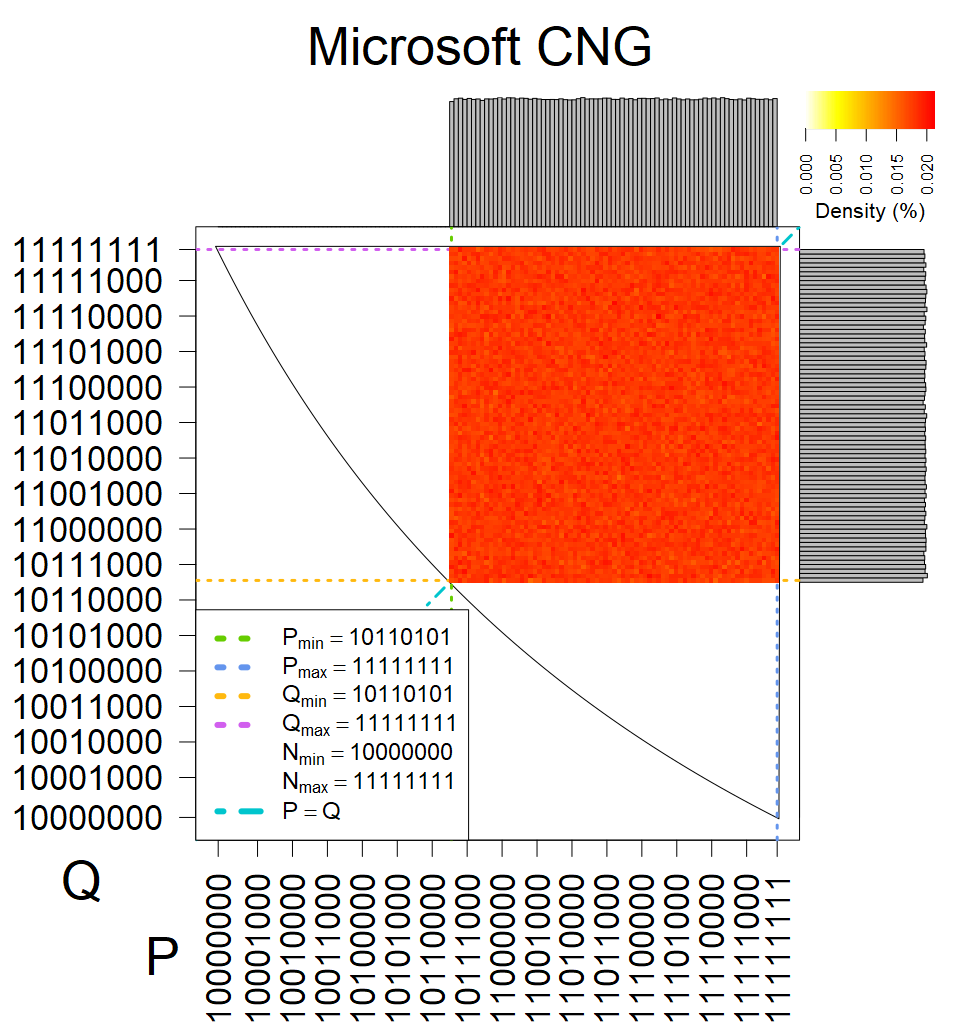
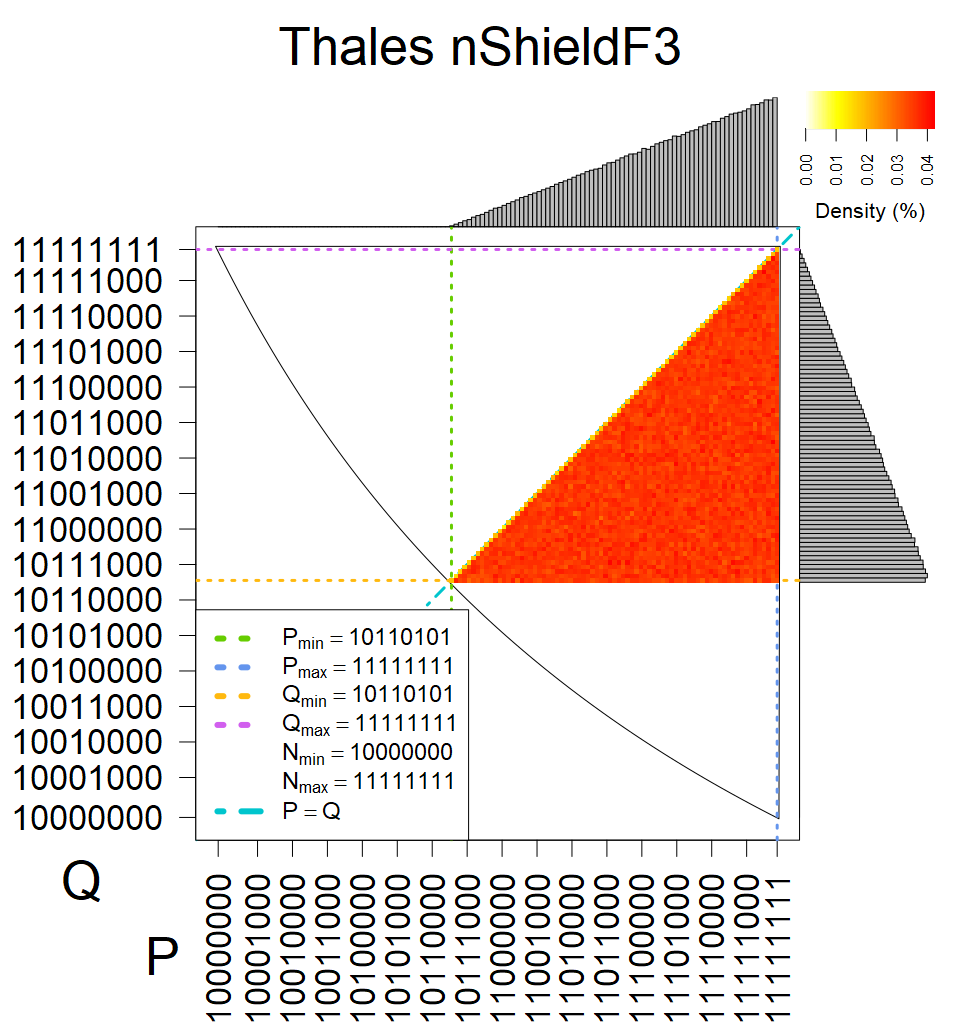
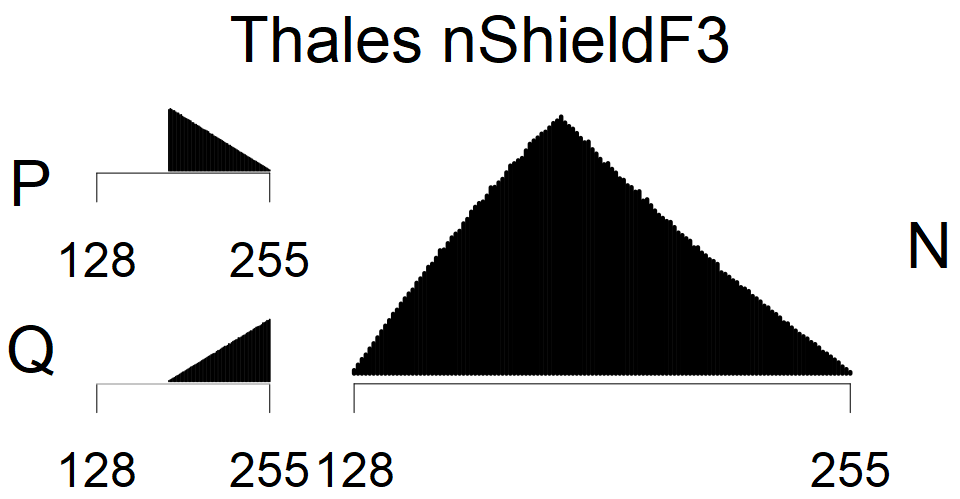
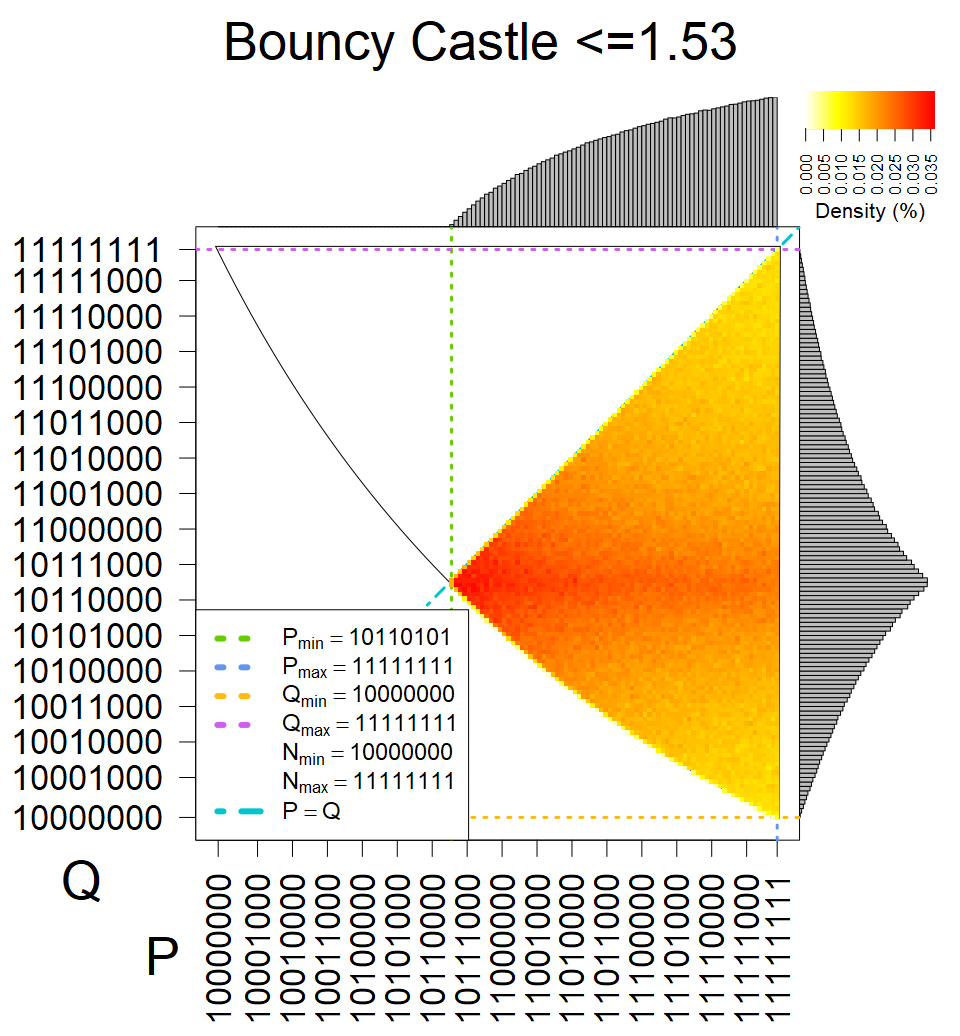
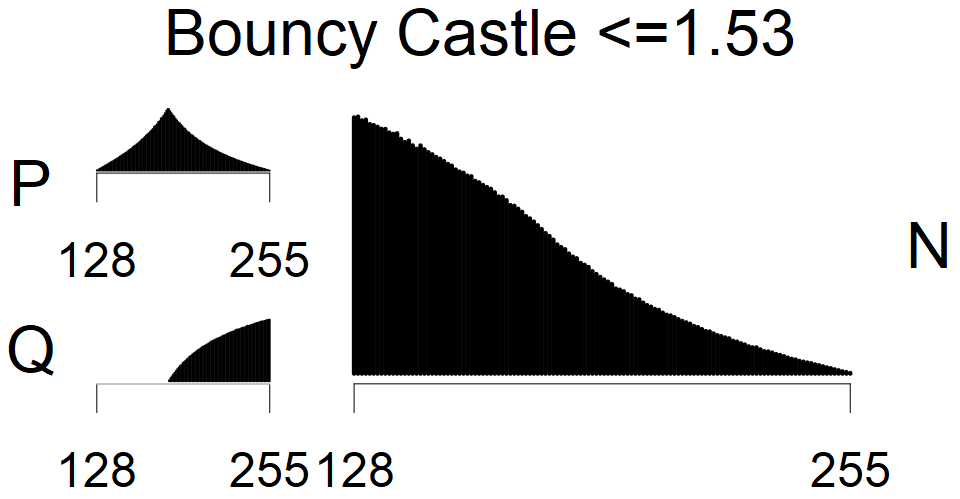
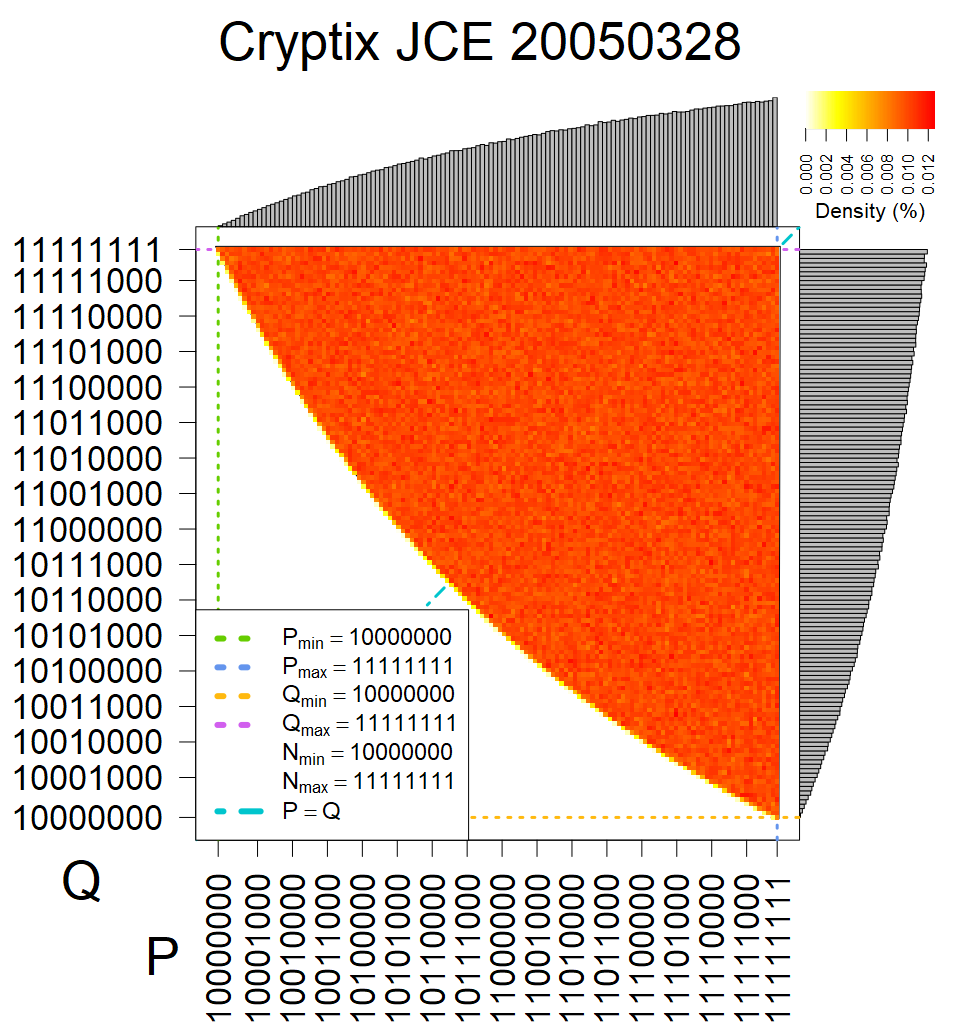
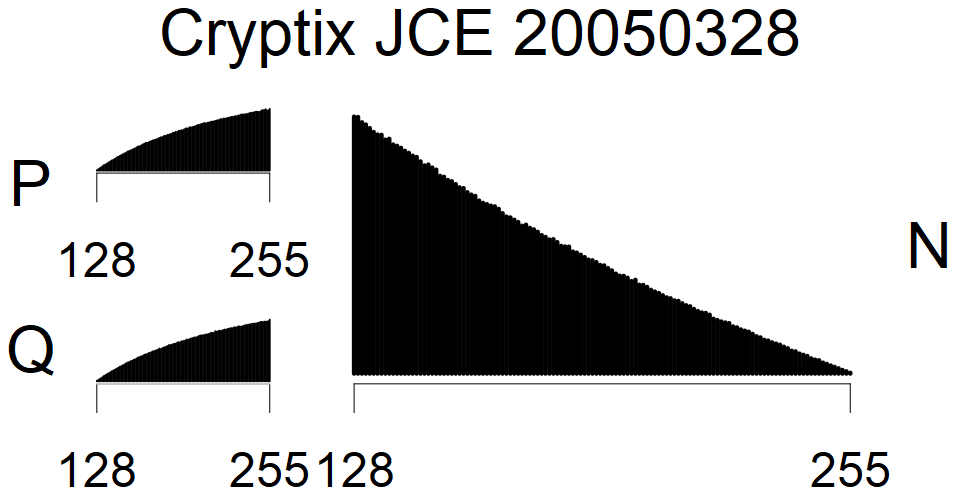
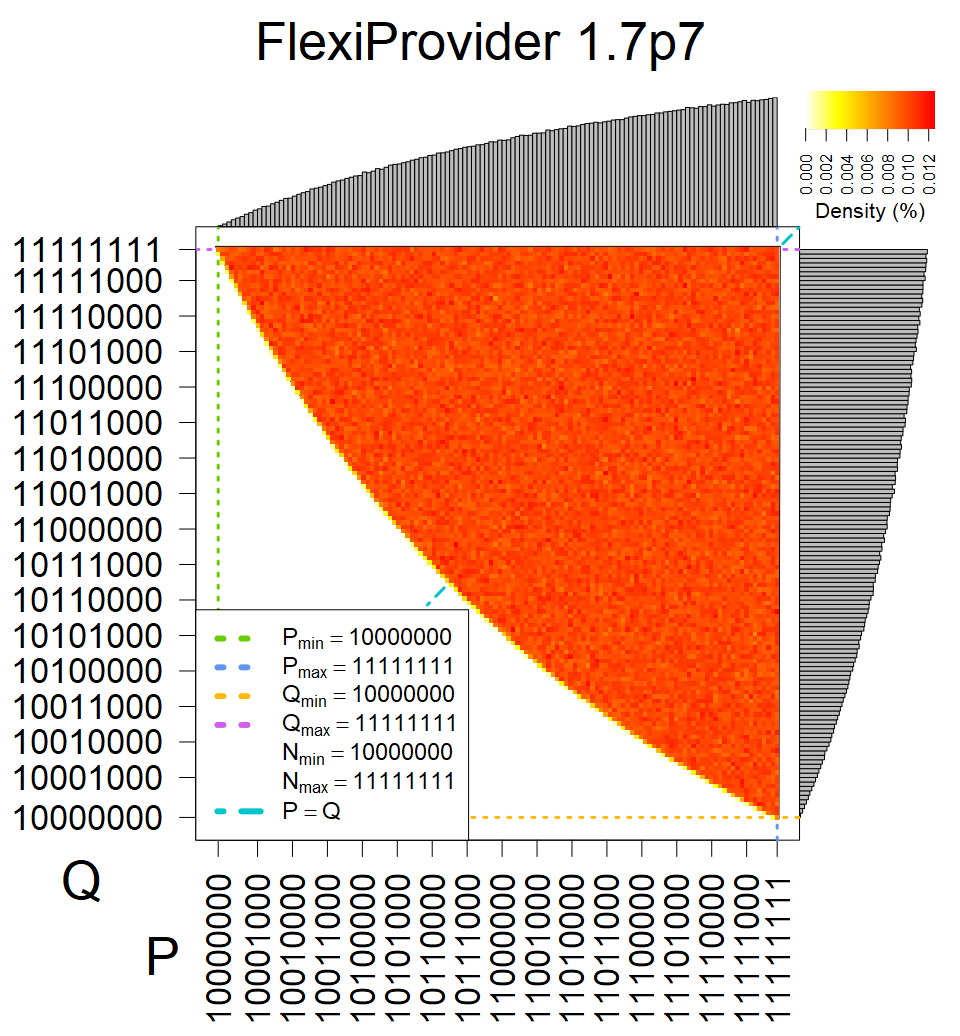
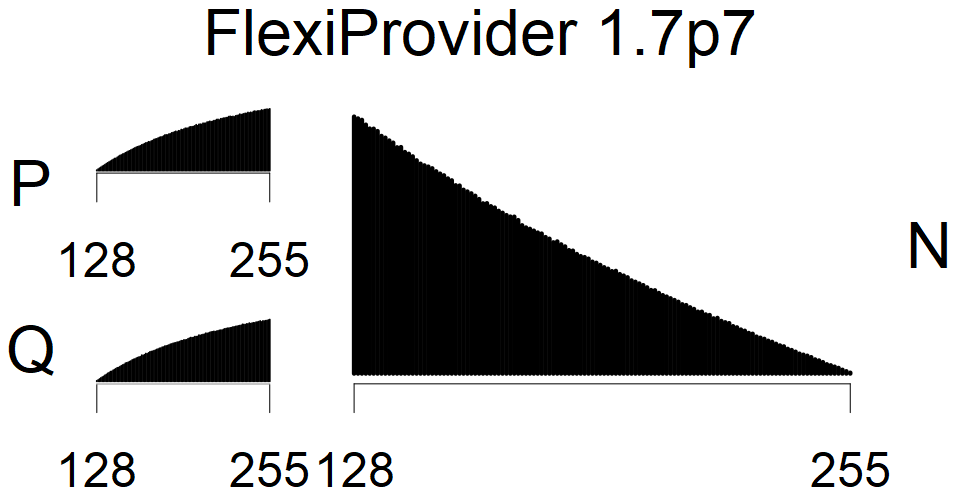
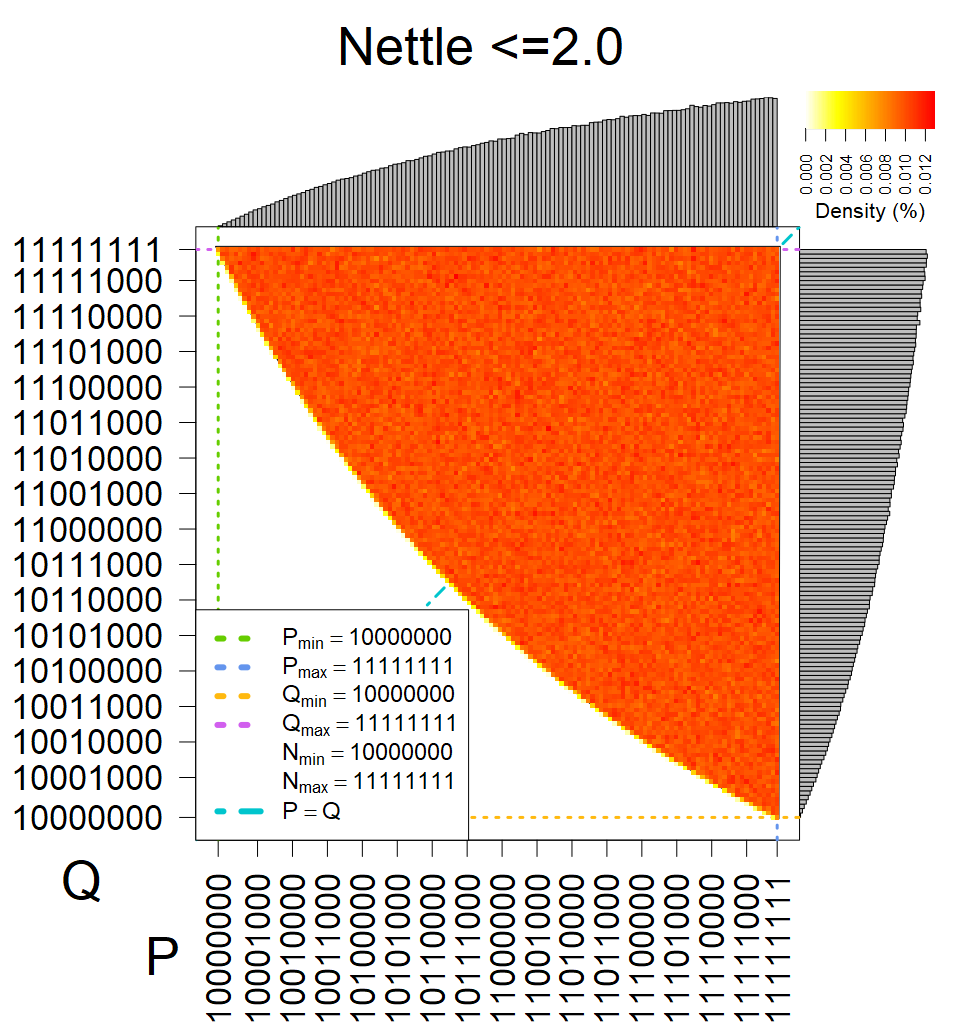
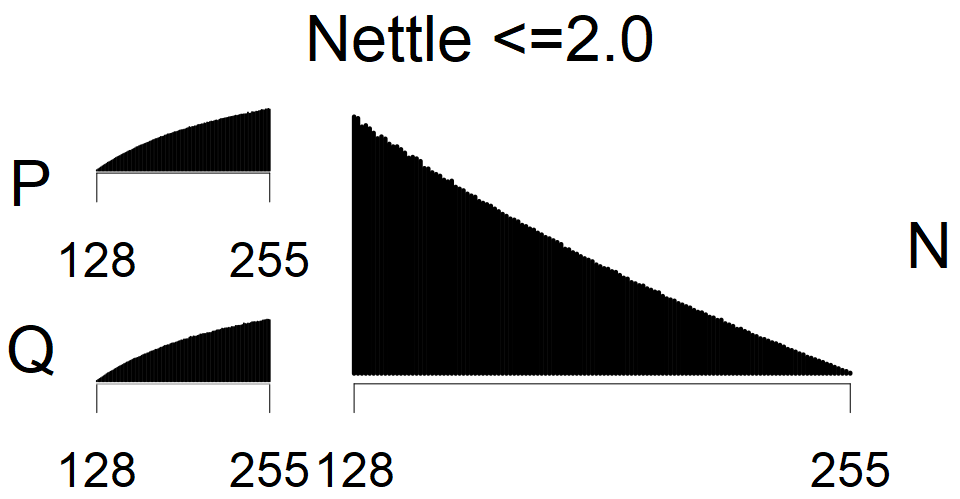
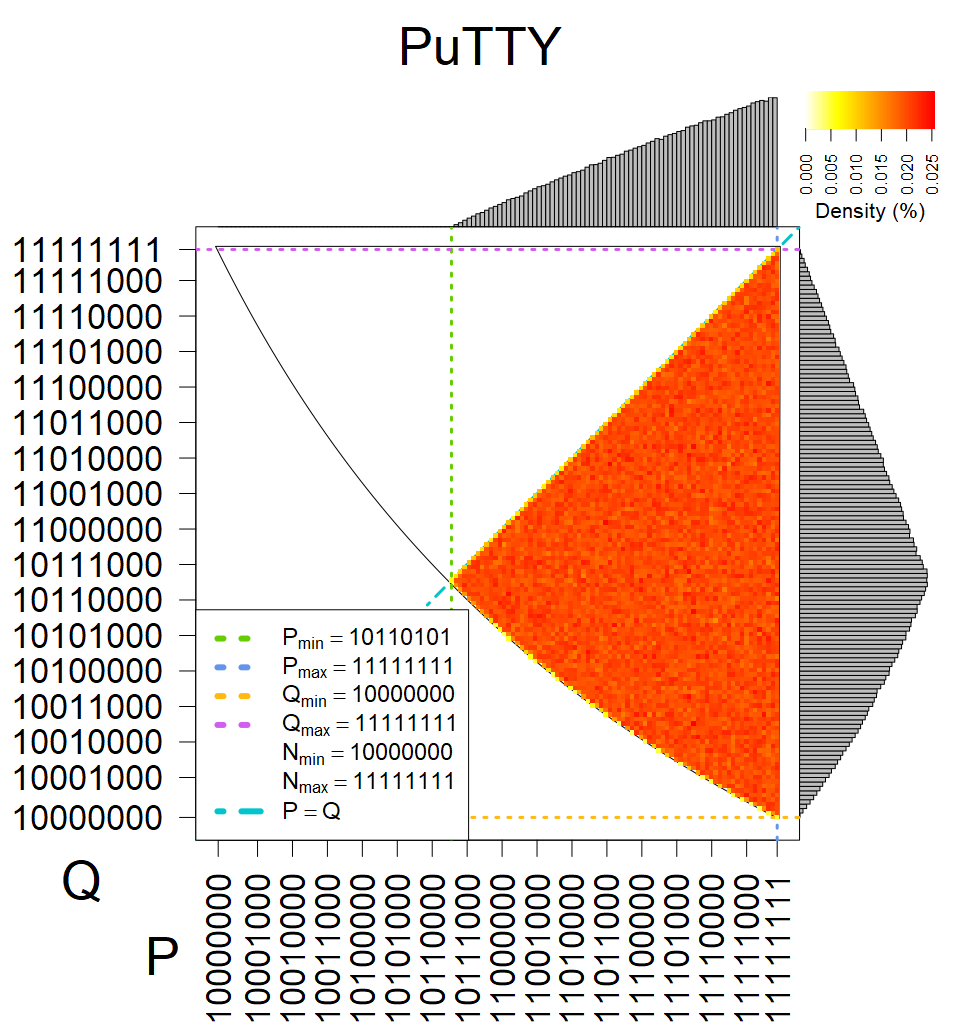
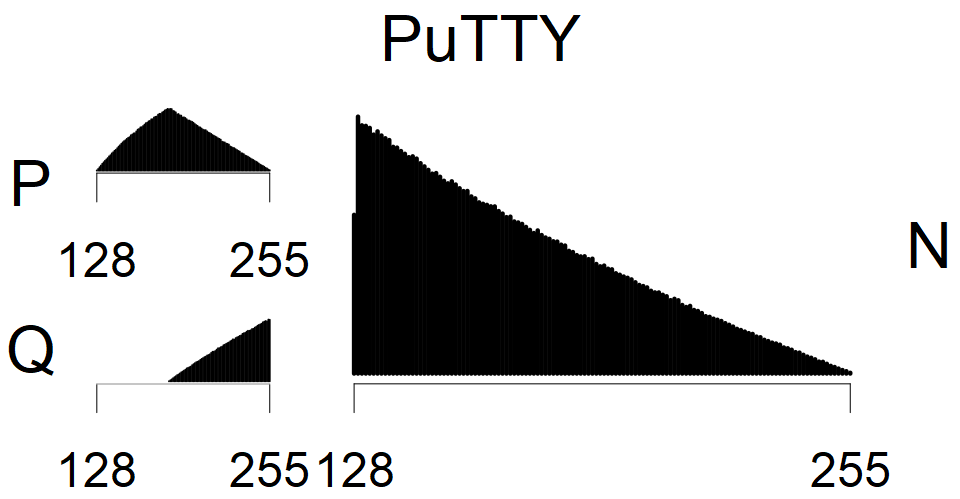
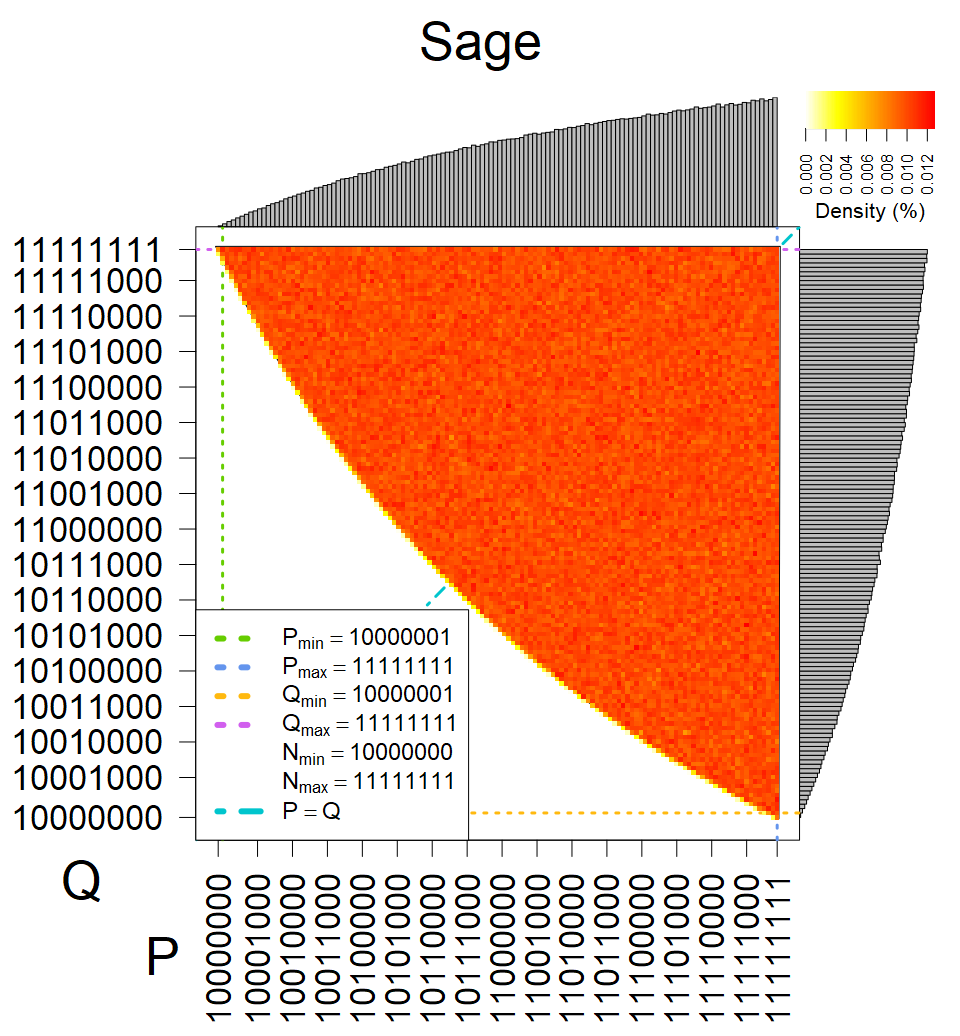
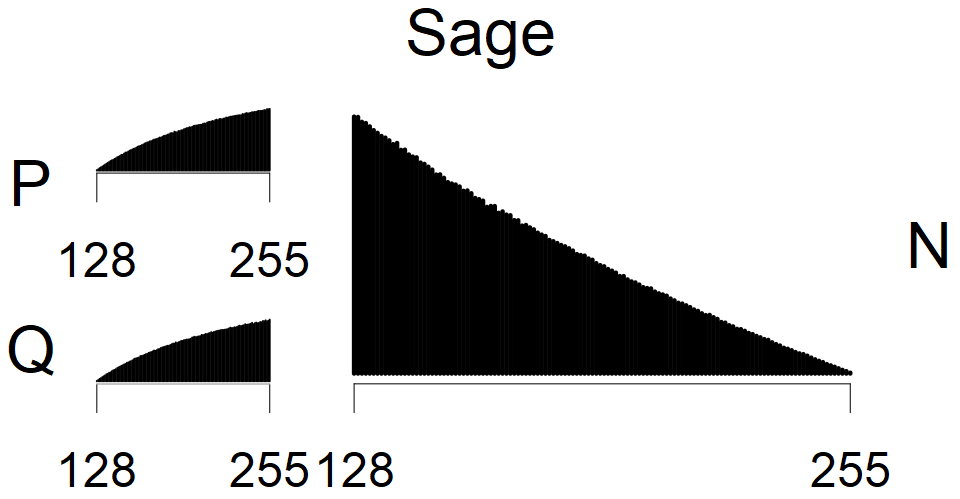
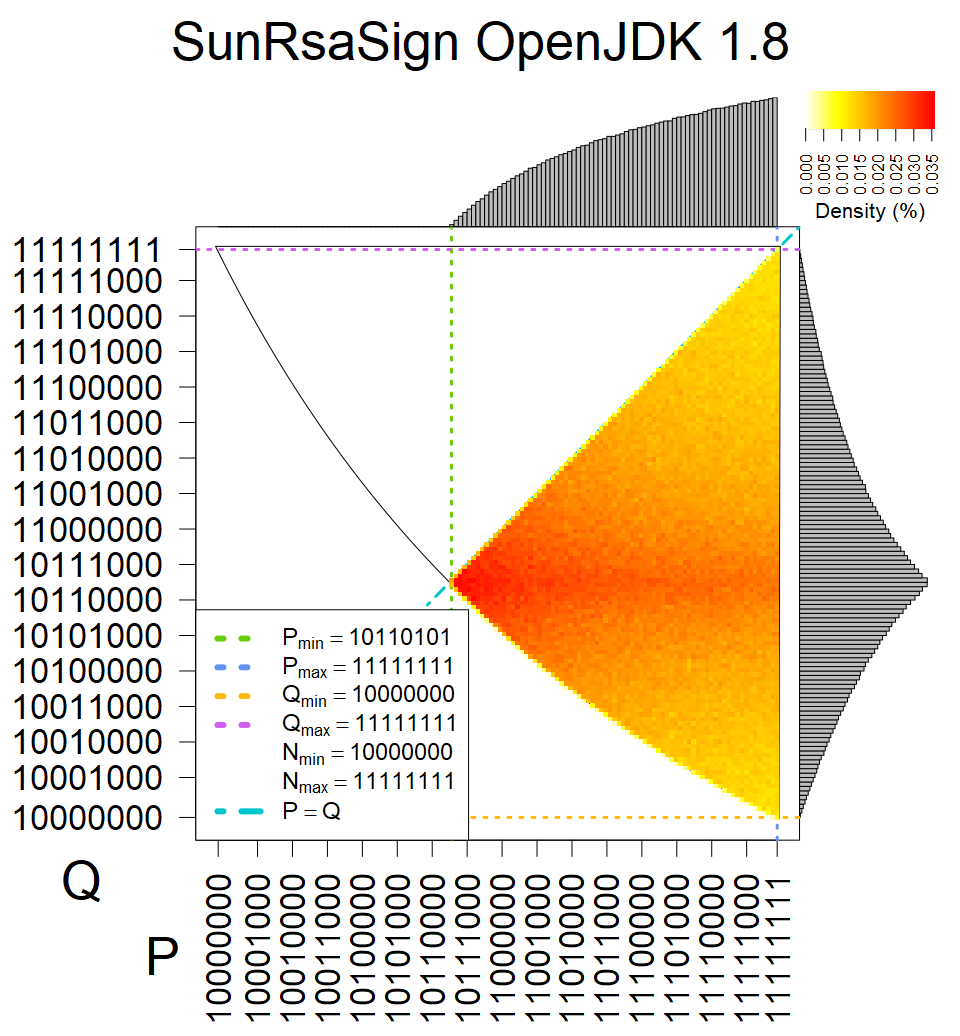
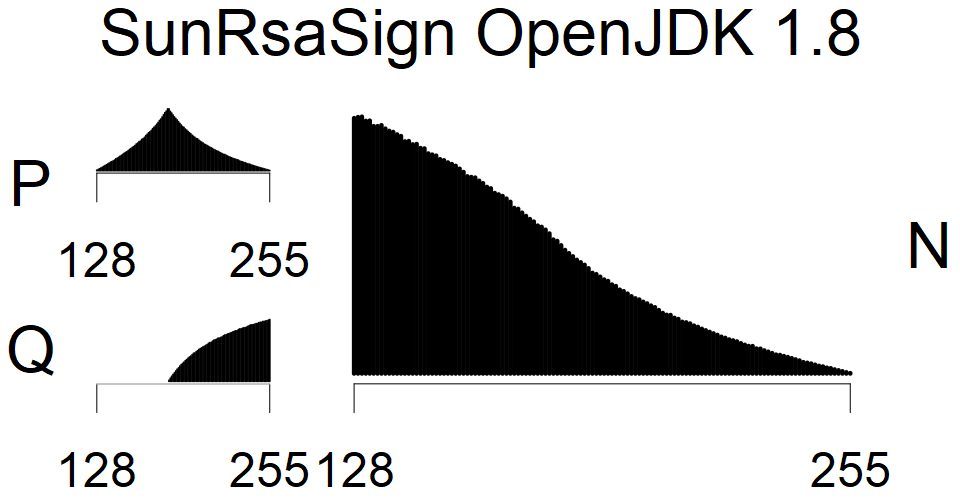
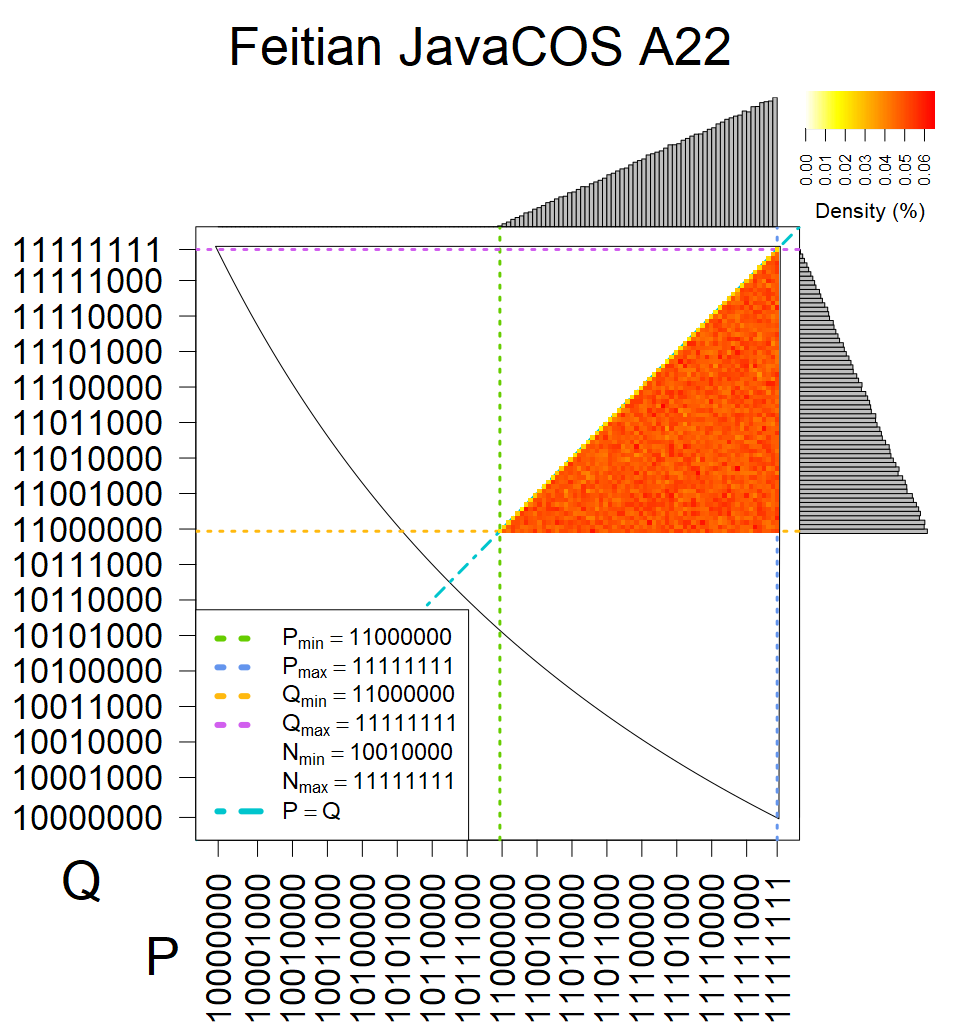
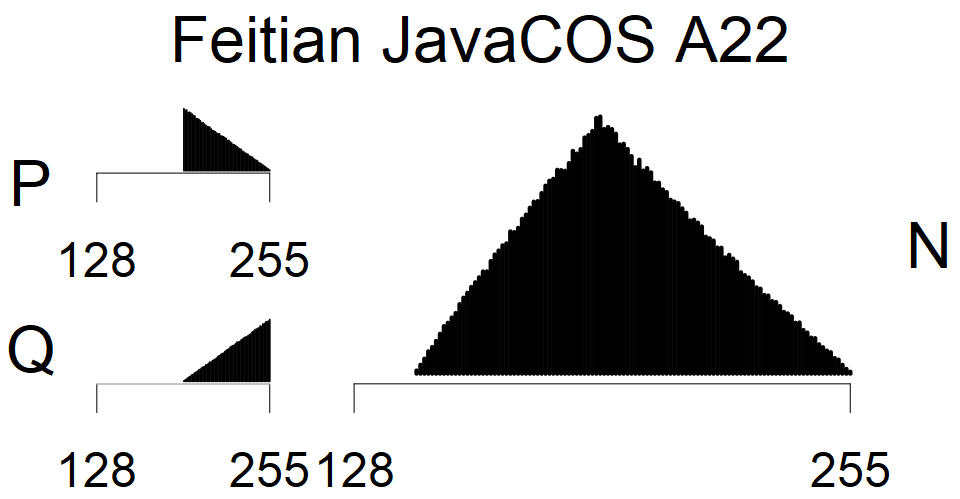
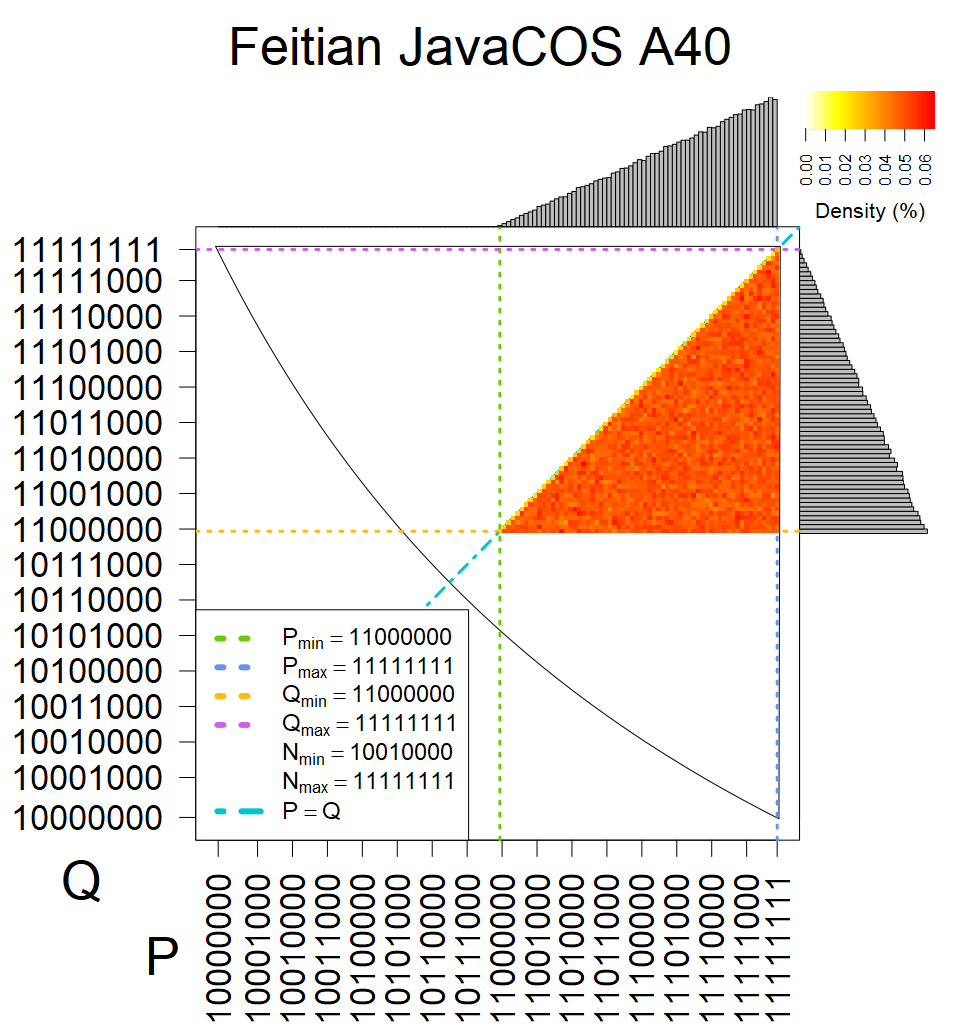
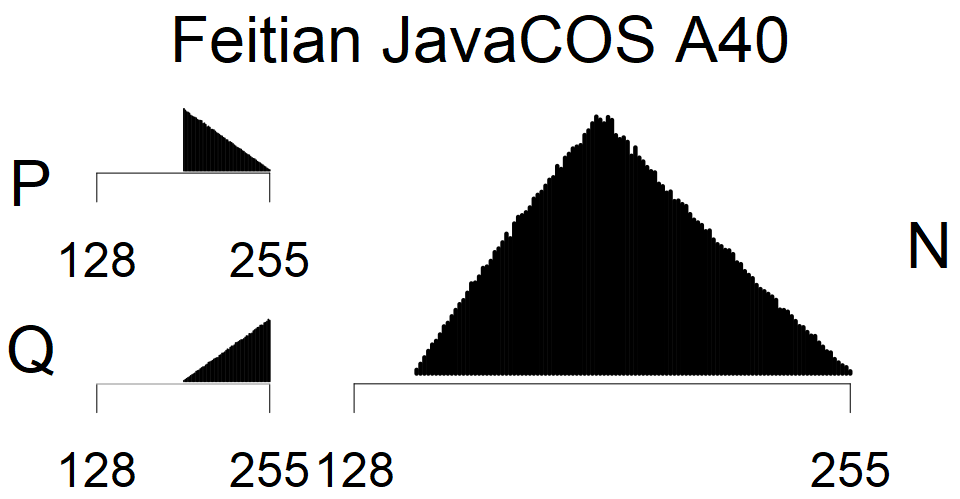
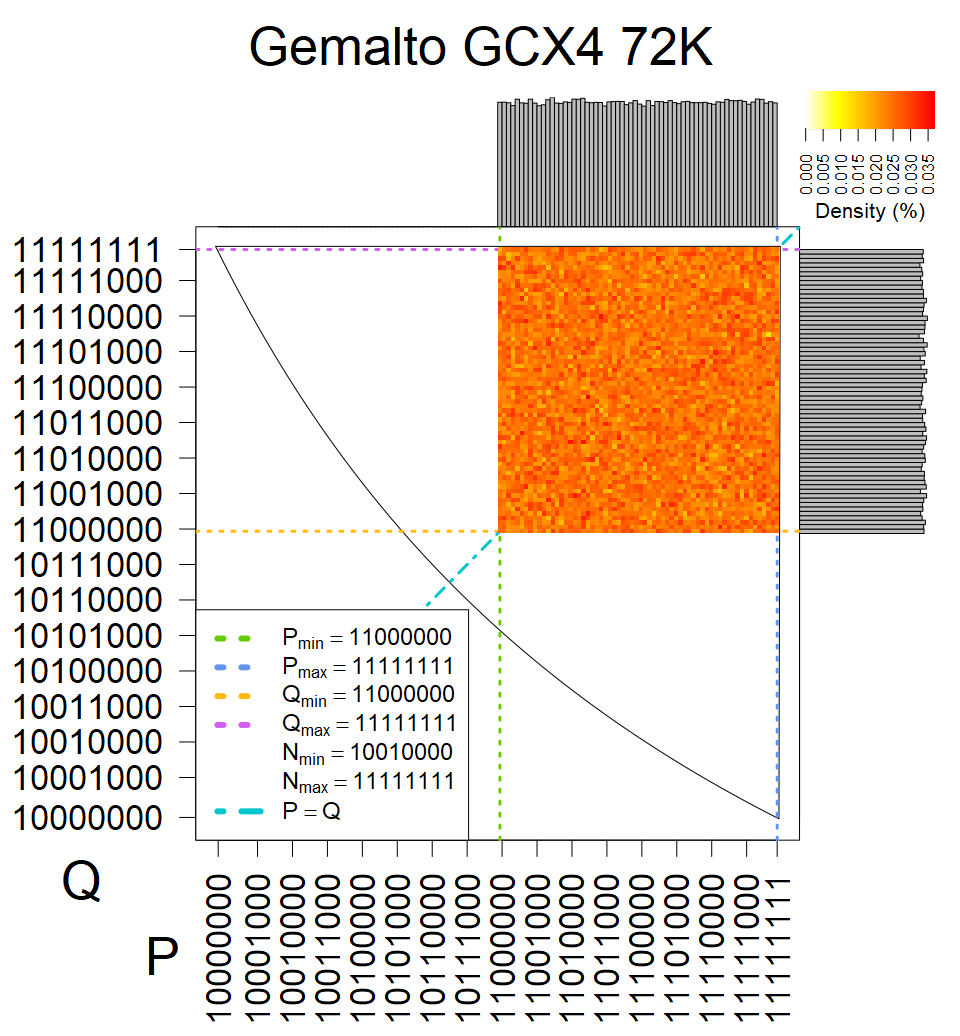
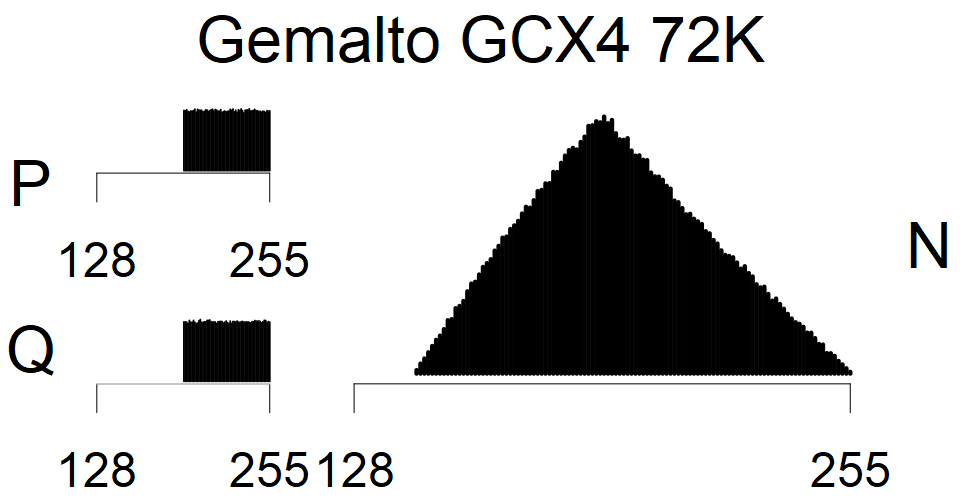
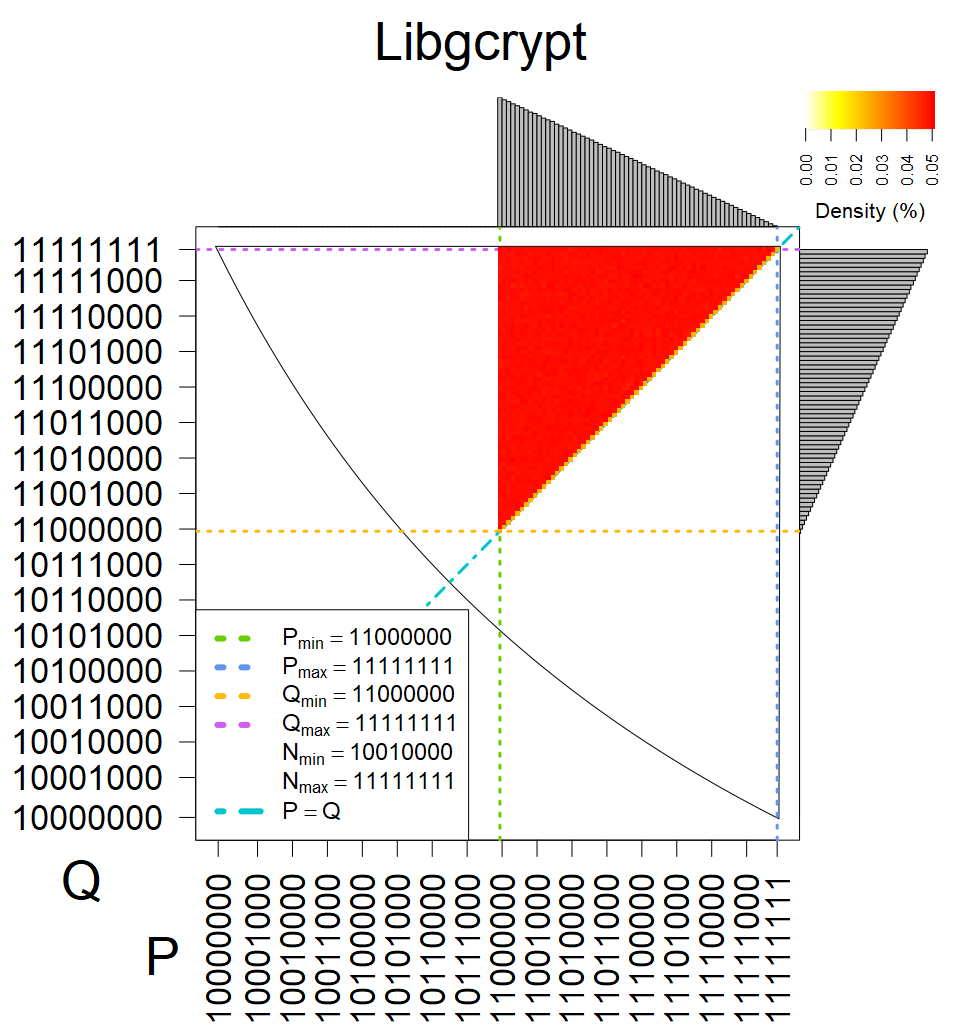
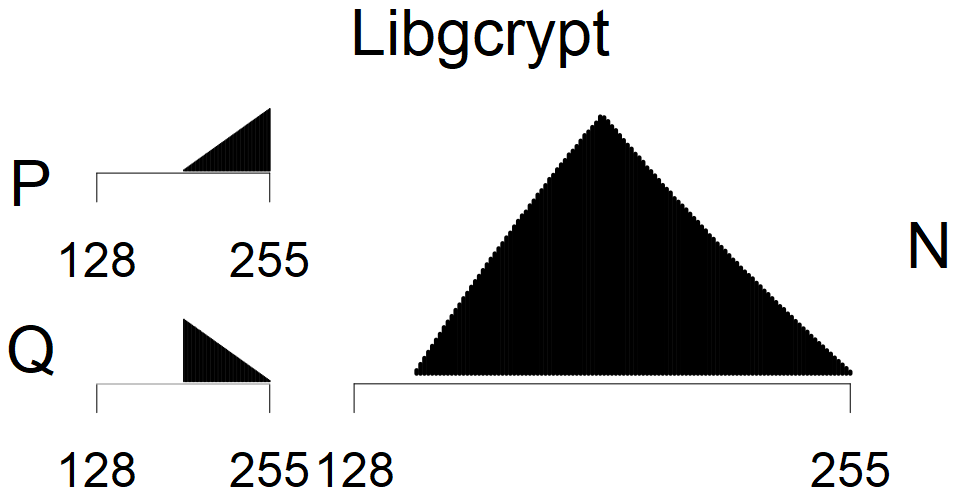
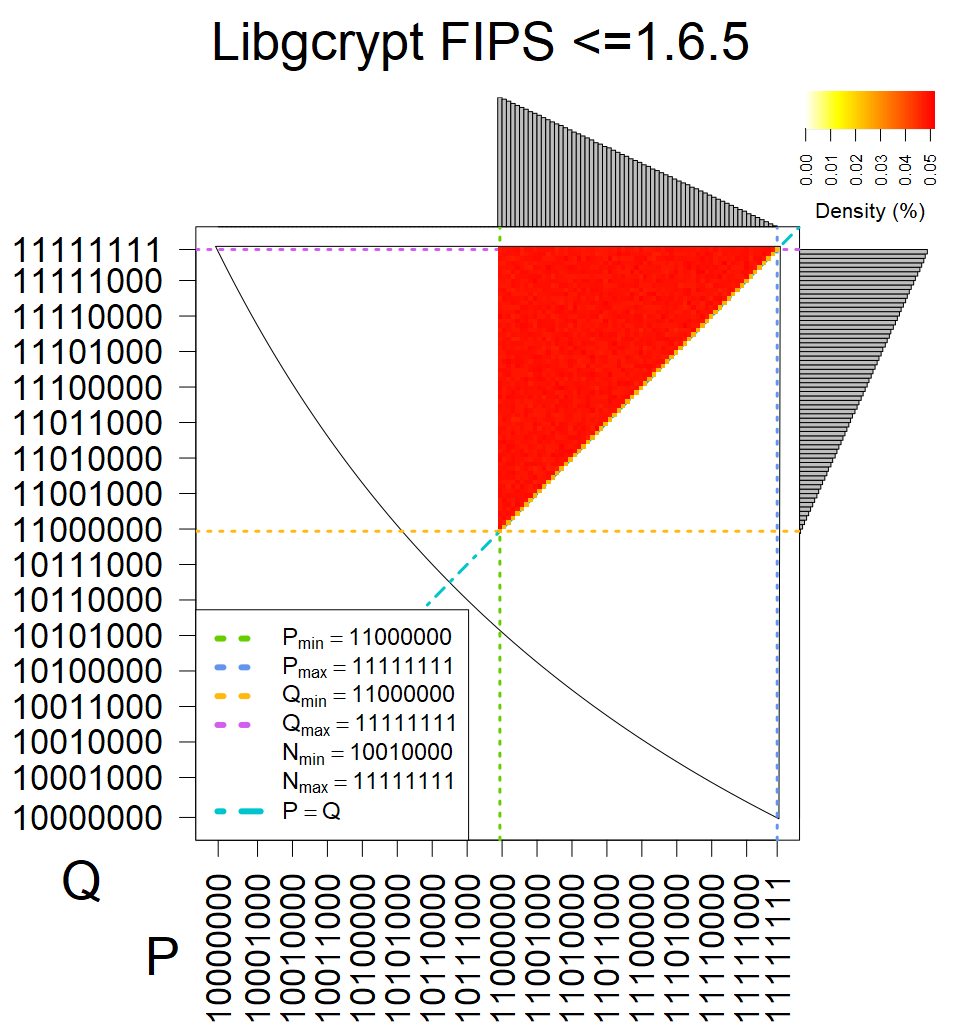
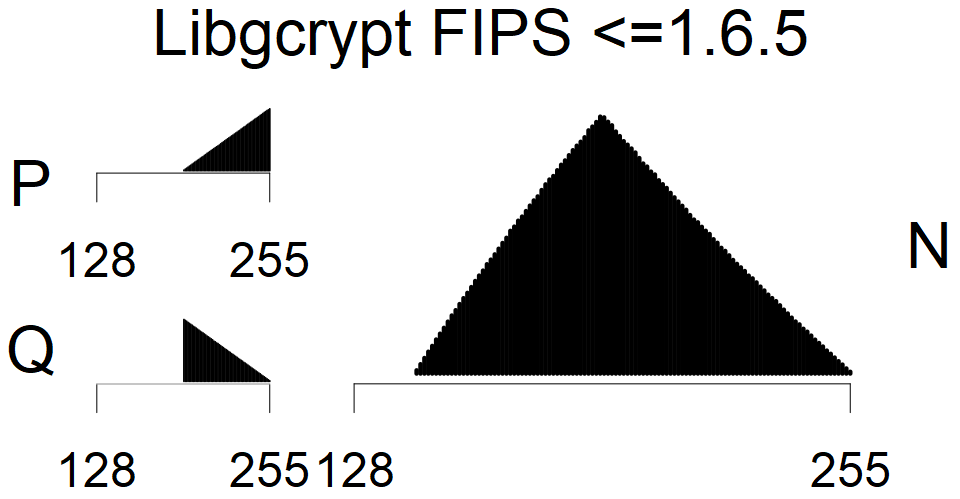
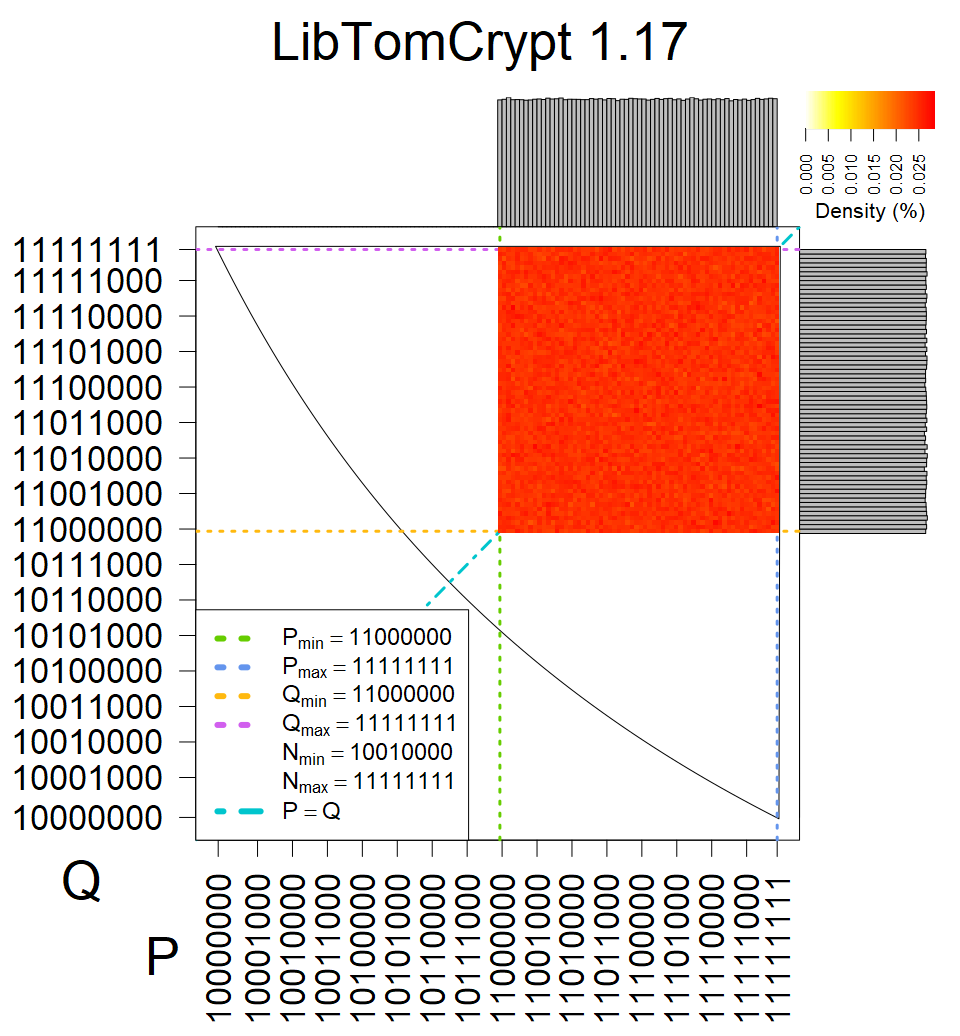
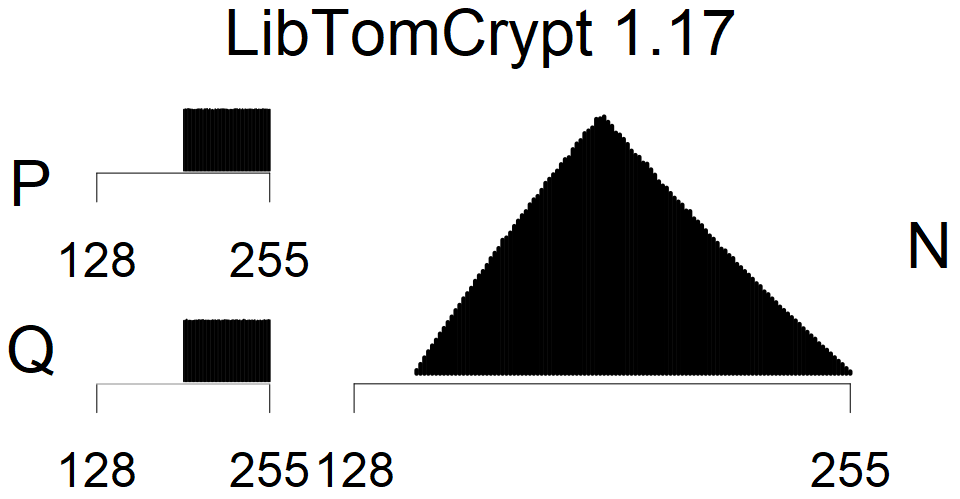
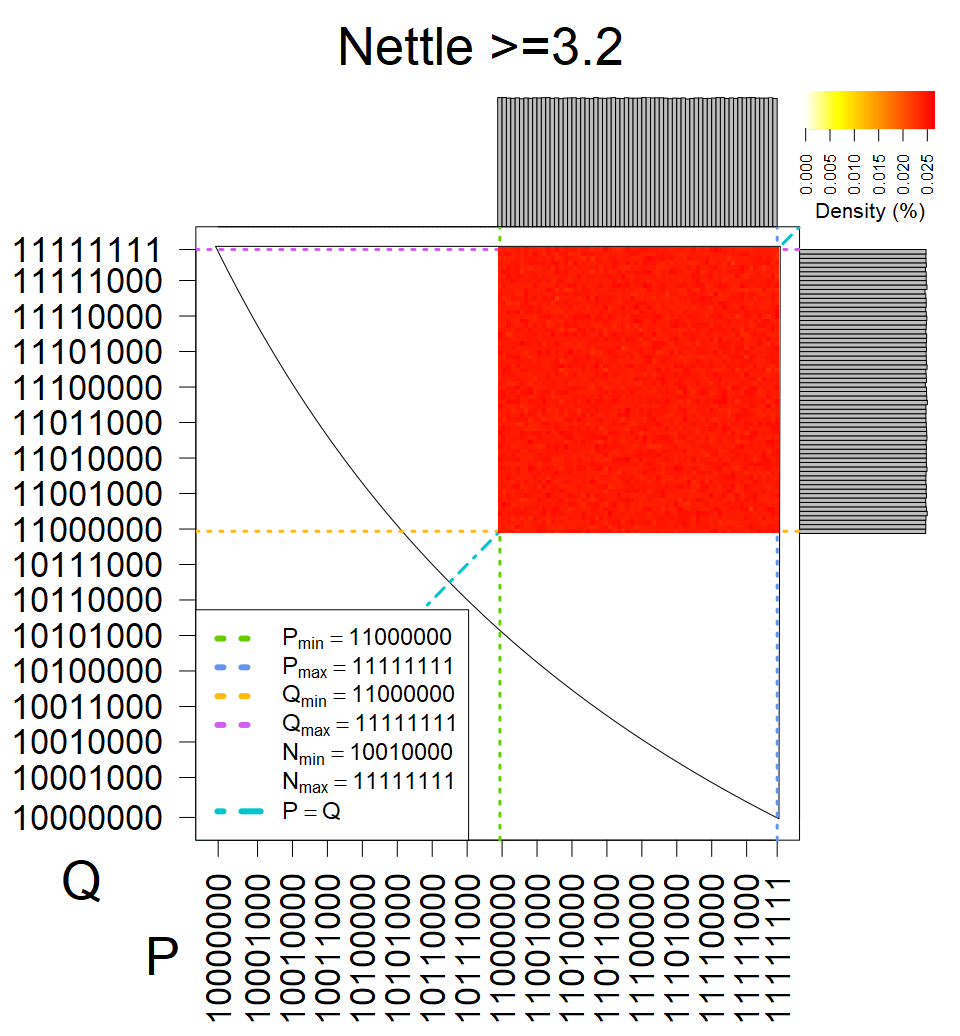
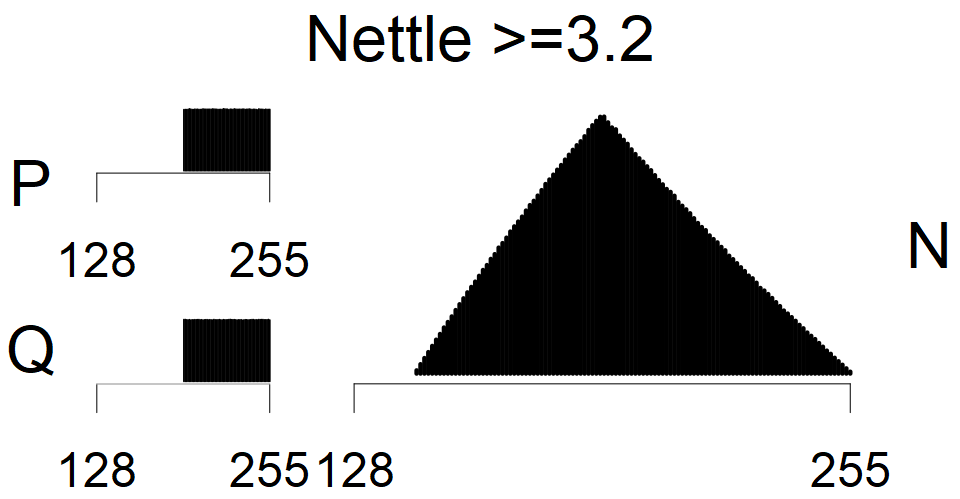
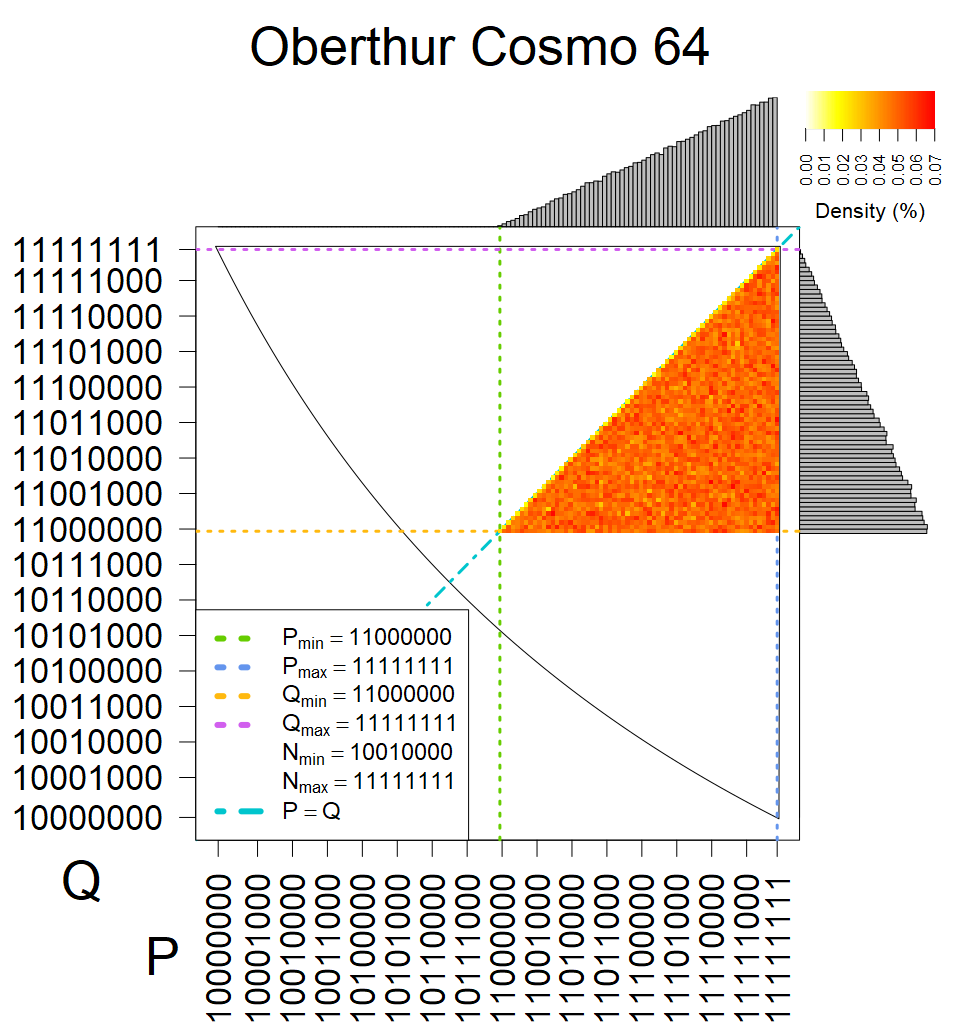
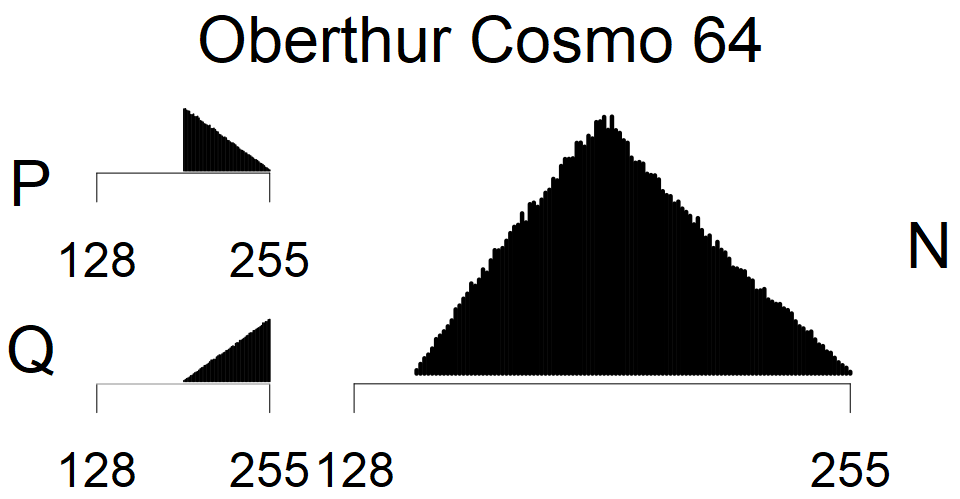
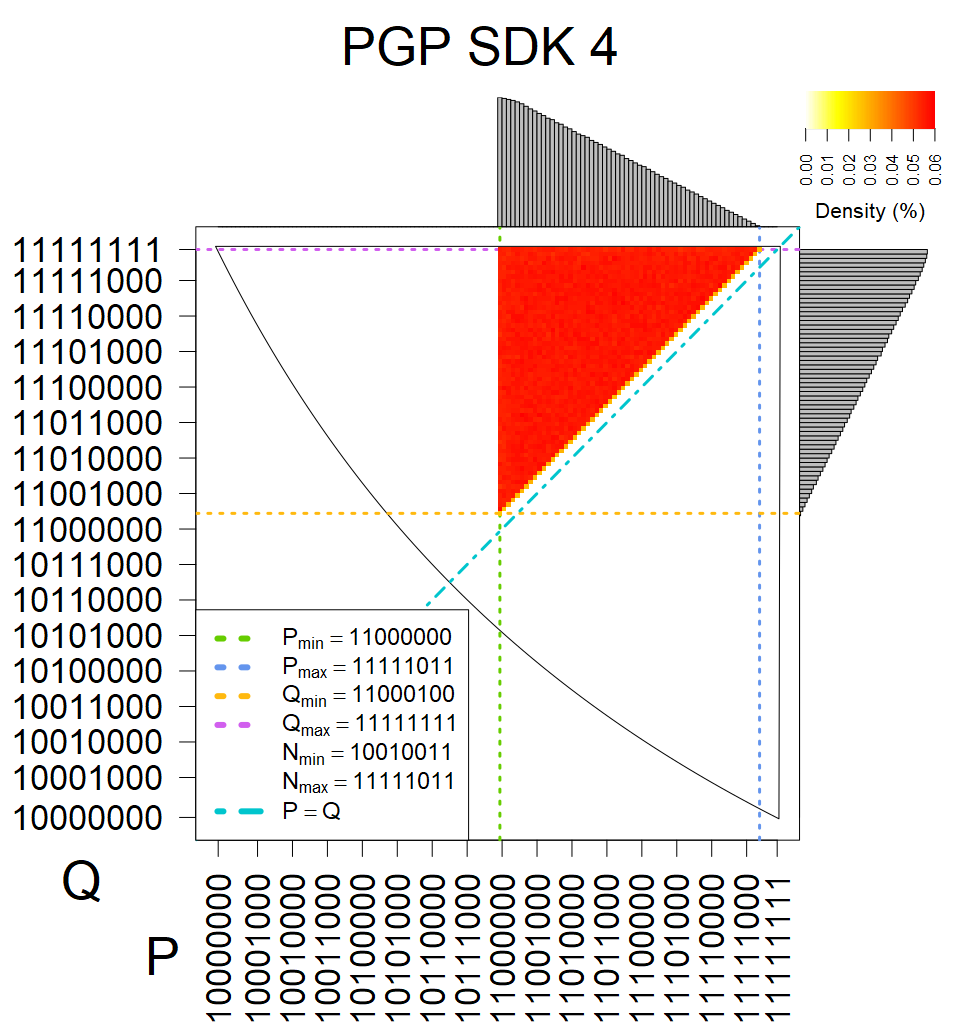
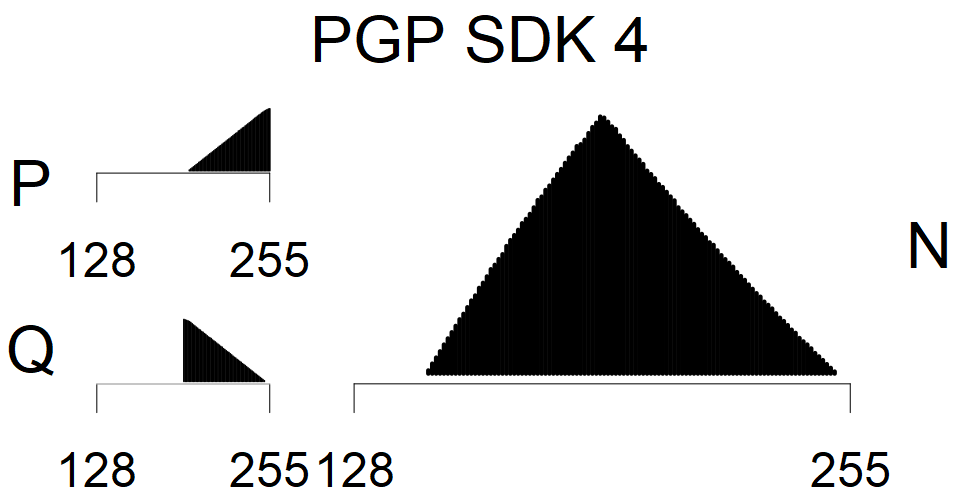
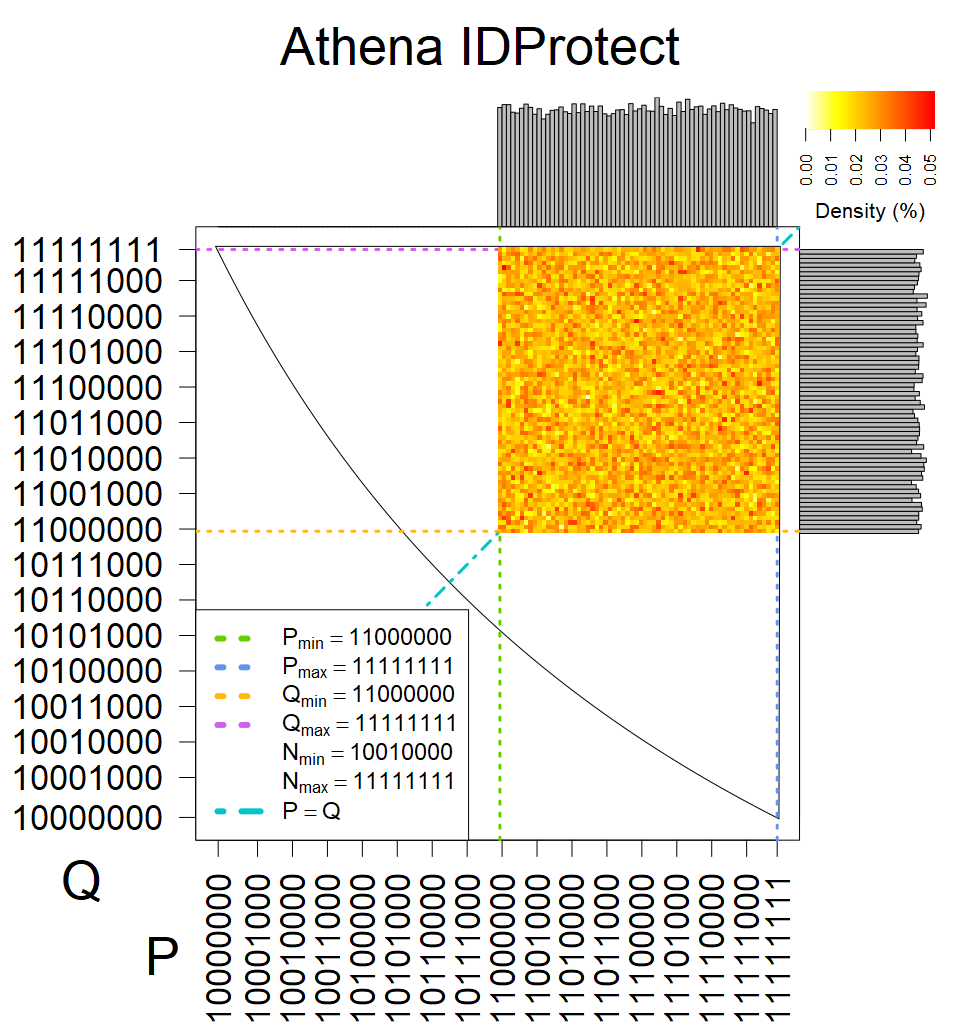
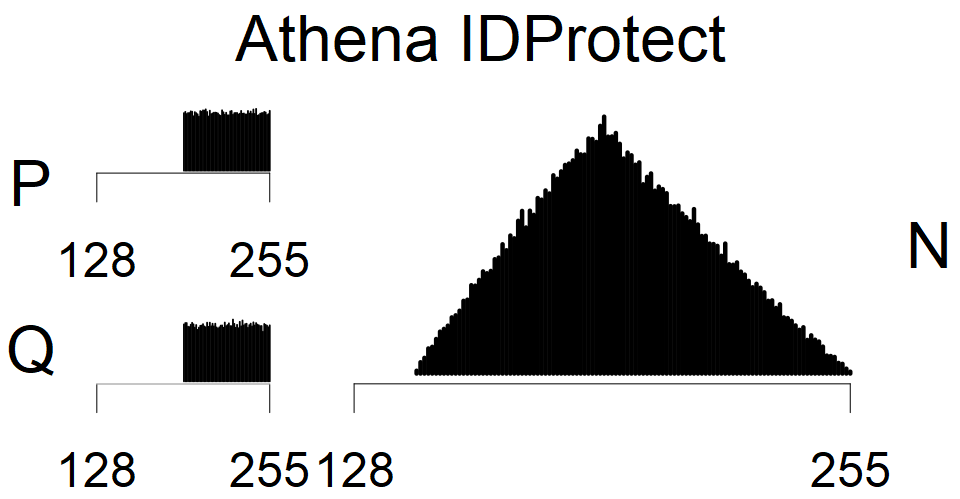
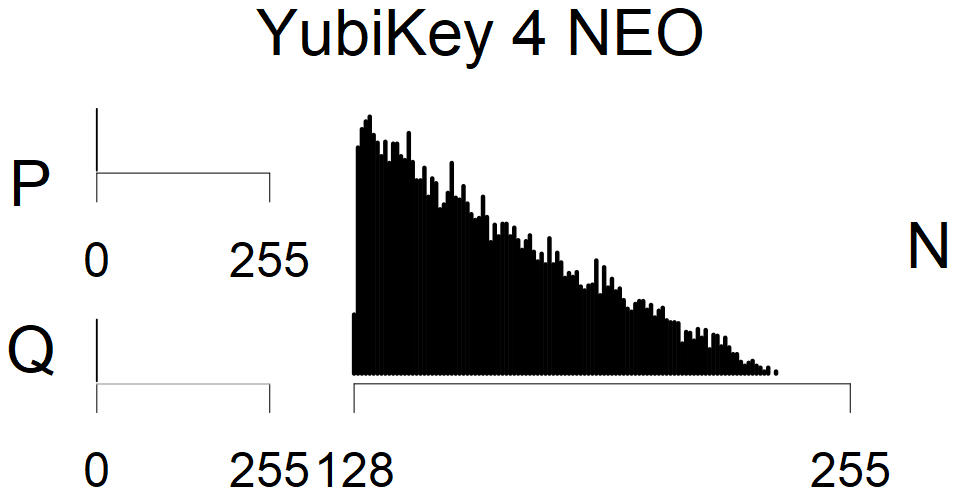
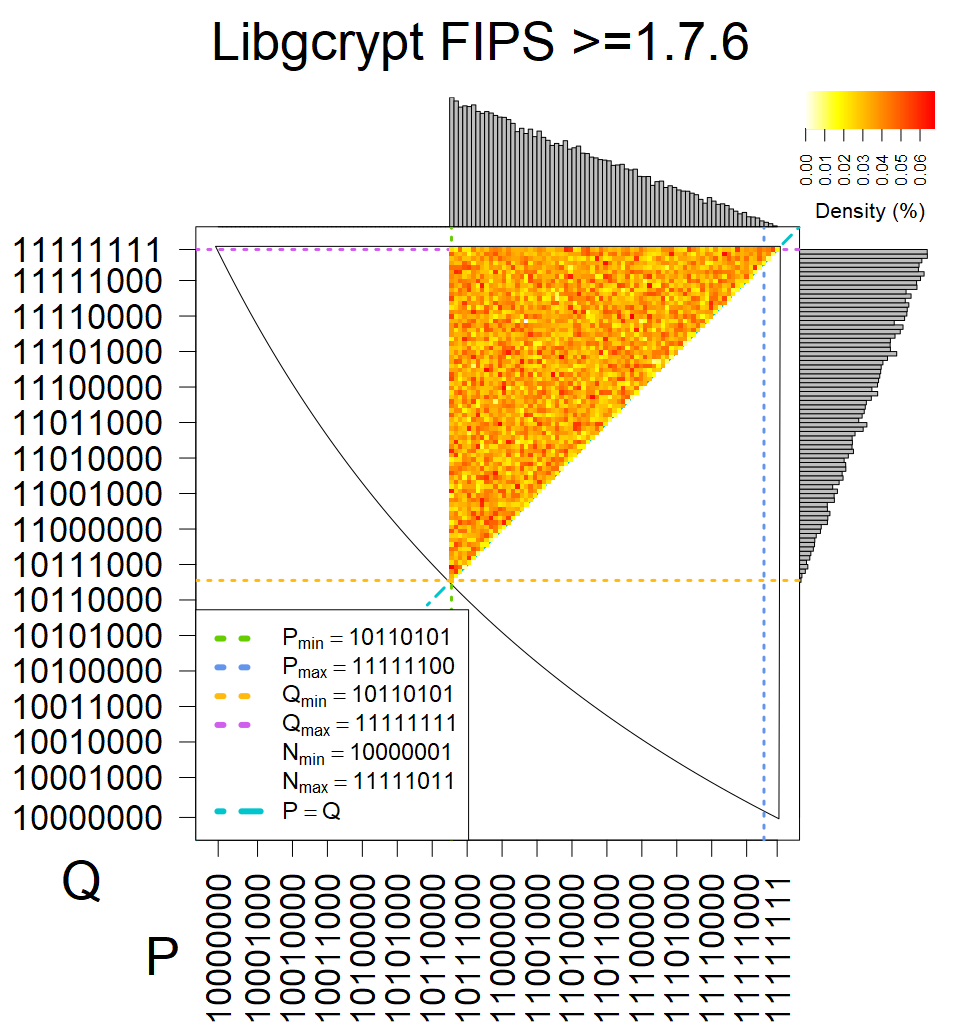
We present the list of all known sources of RSA keys we have gathered. We separate them into distinct groups with similar or the same properties with a short description of their bias. Each source contains heatmap of keys primes, type of the origin, number of gathered keys, and link to the dataset with raw keys. Besides software libraries, we also mention versions of the software, we used, because sometimes the maintainers decide to change the key generation algorithm (as you can see on Bouncy Castle or mbedTLS source).
Group I
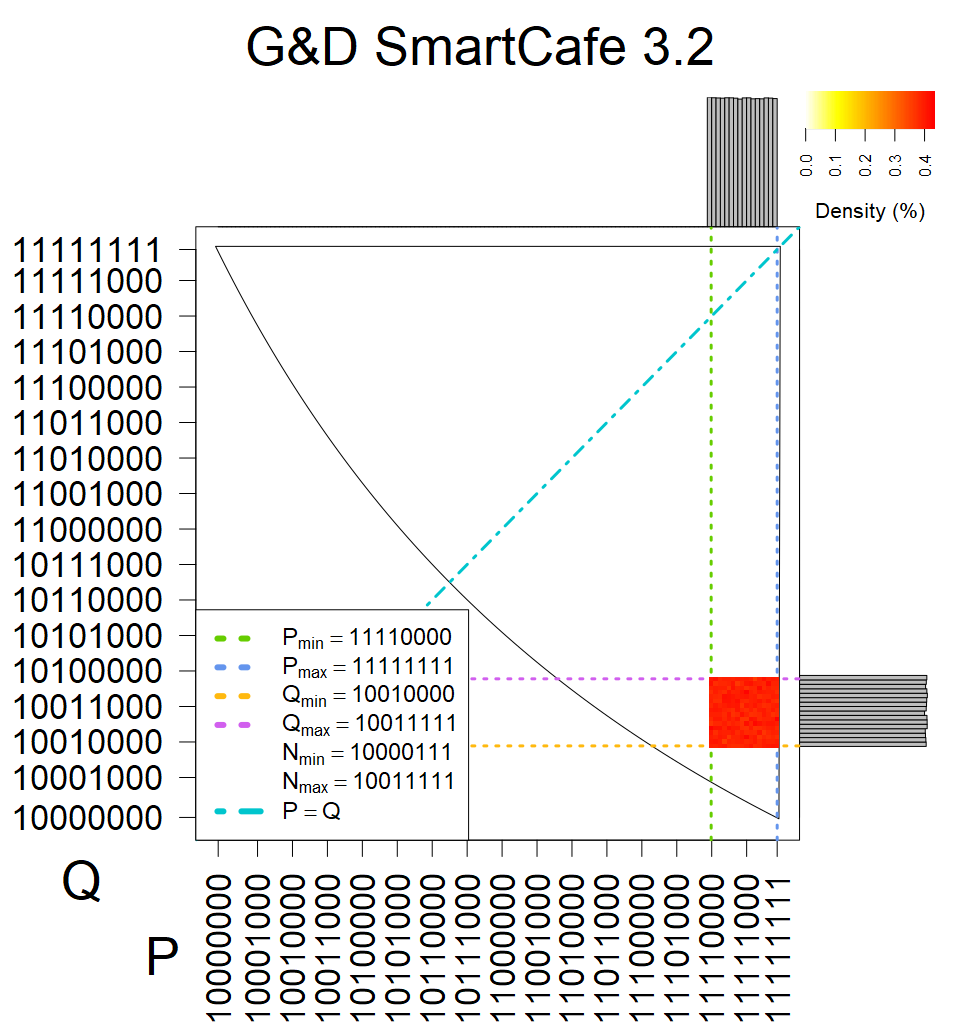
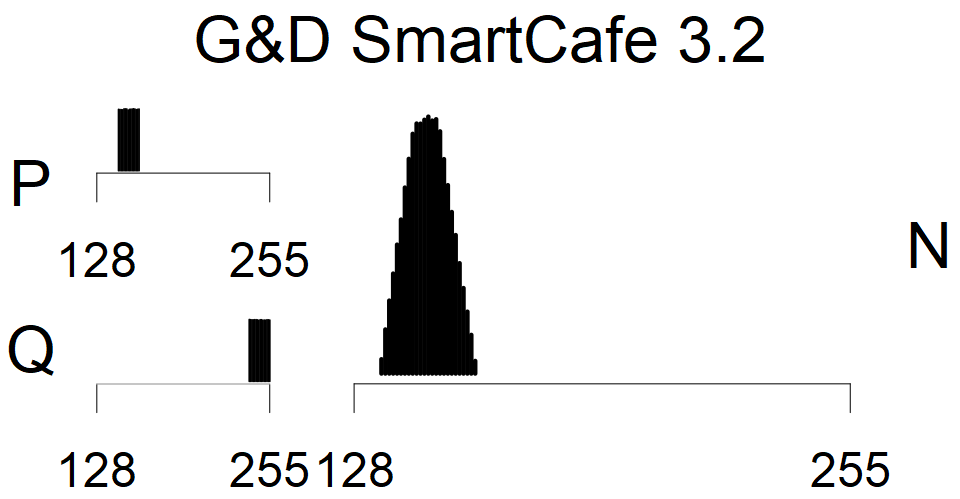
Smart card with fixed top four bits of primes. Bias also on the second least significant bit is present.
Group II
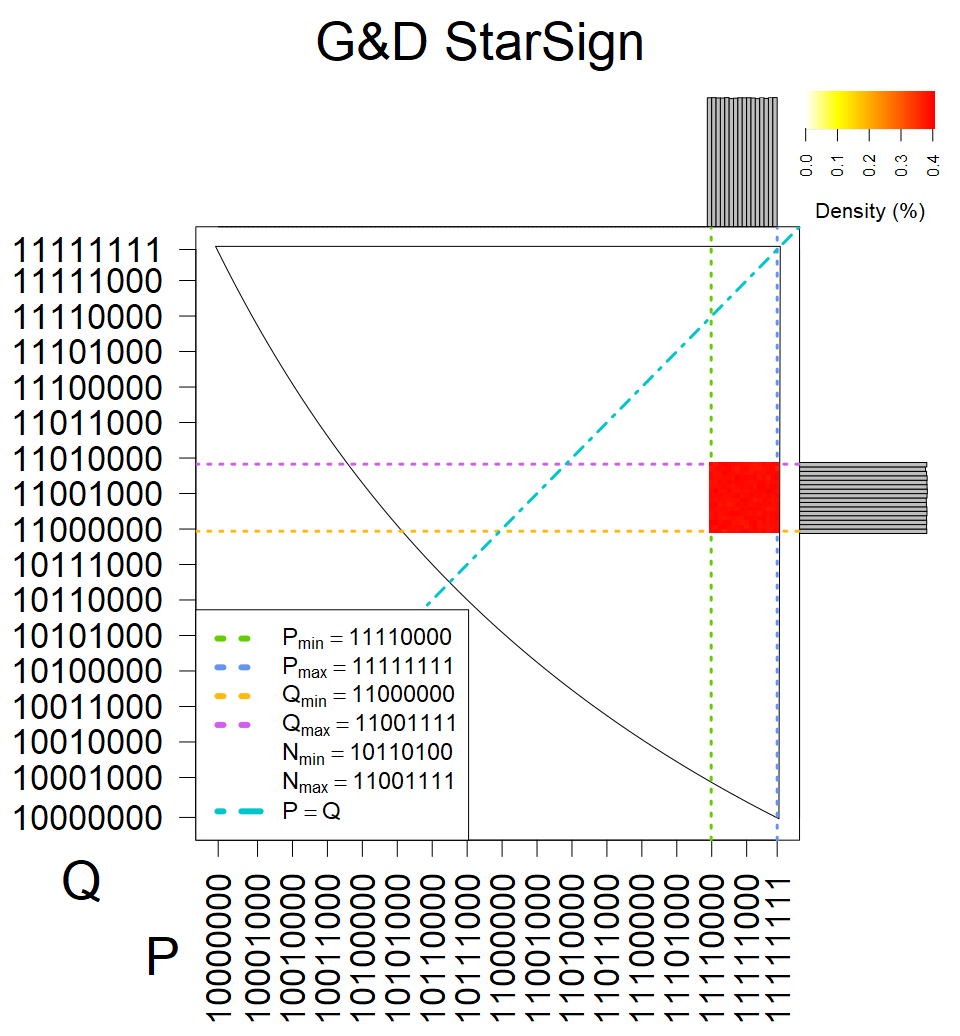
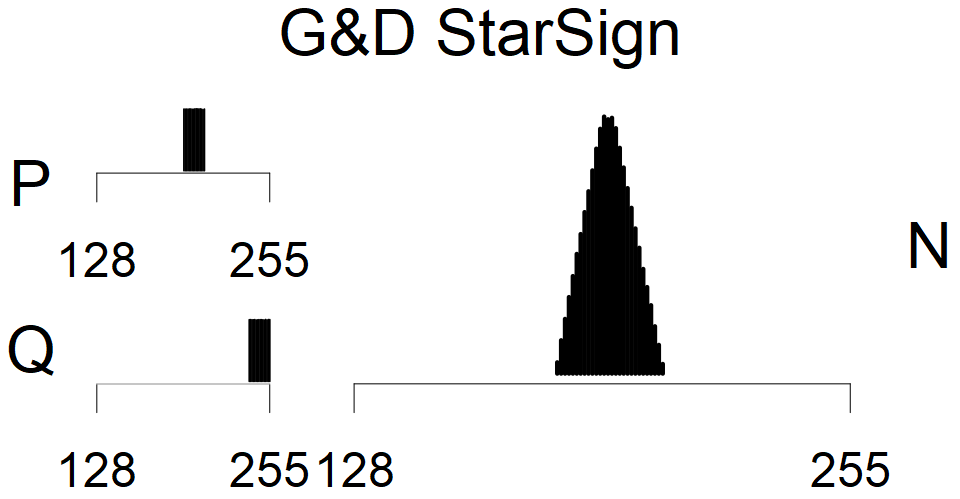
Smart card with fixed top four bits of primes (different fixed values against other G&D smart cards). Biased modulus mod 3 and 4.
Group III
Primes from whole possible range, but with non-uniform distribution of prime q. Biased modulus mod 4.
Group IV
Gaussian distribution of primes without bias on modulus mod 3 or 4.
Group VI
Primes have top two bits set to one. Biased also in modulus mod 4.
Group VII
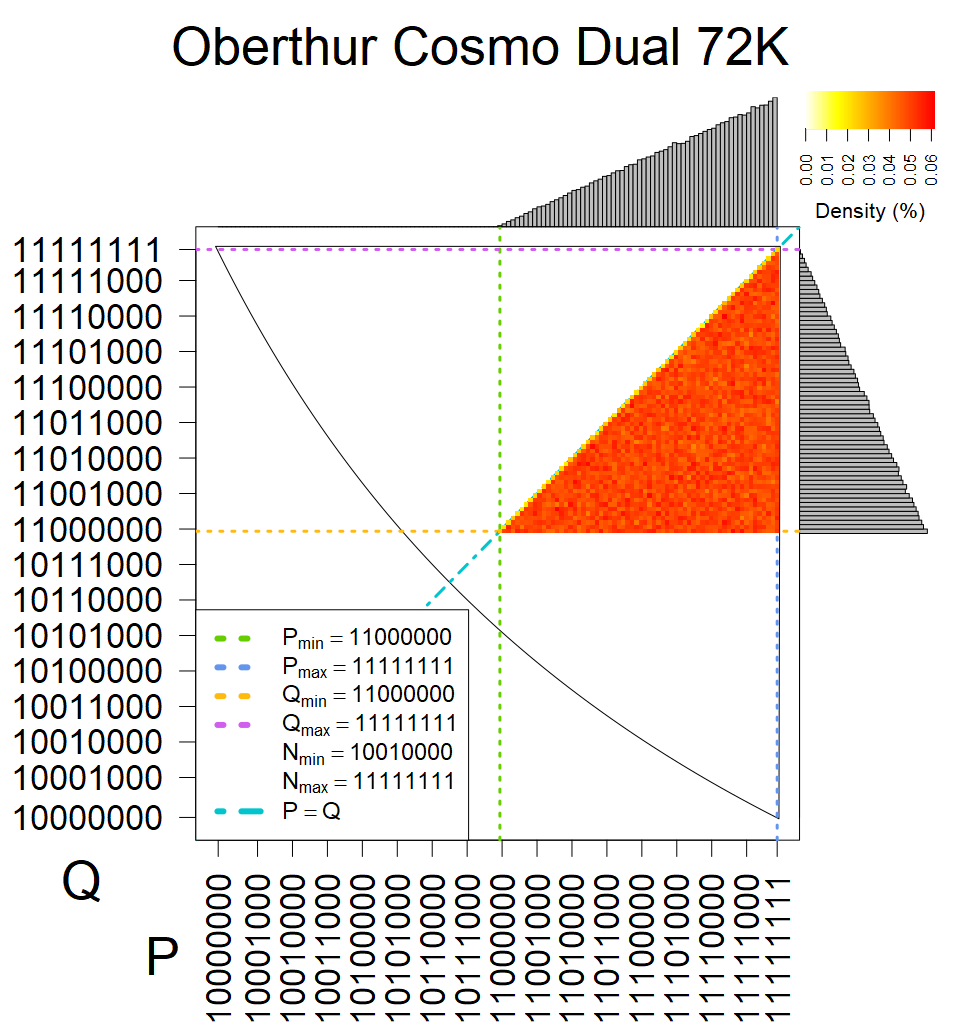
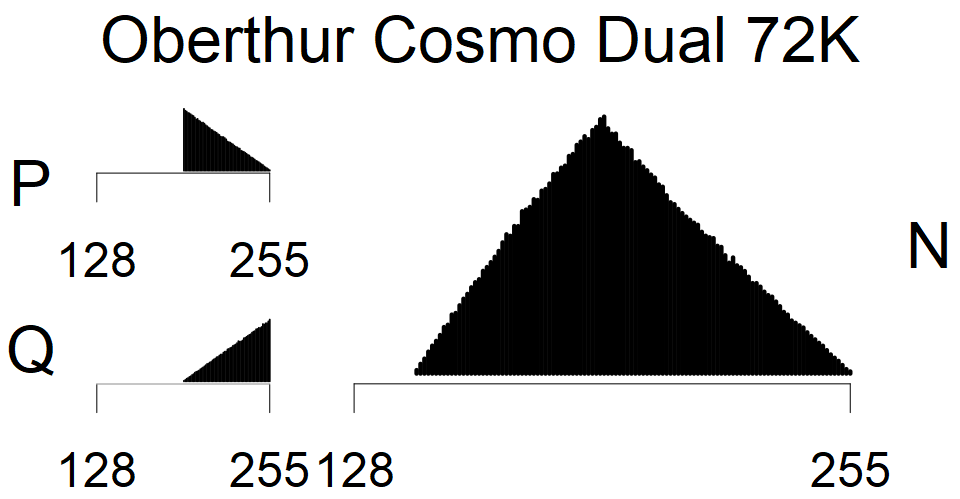
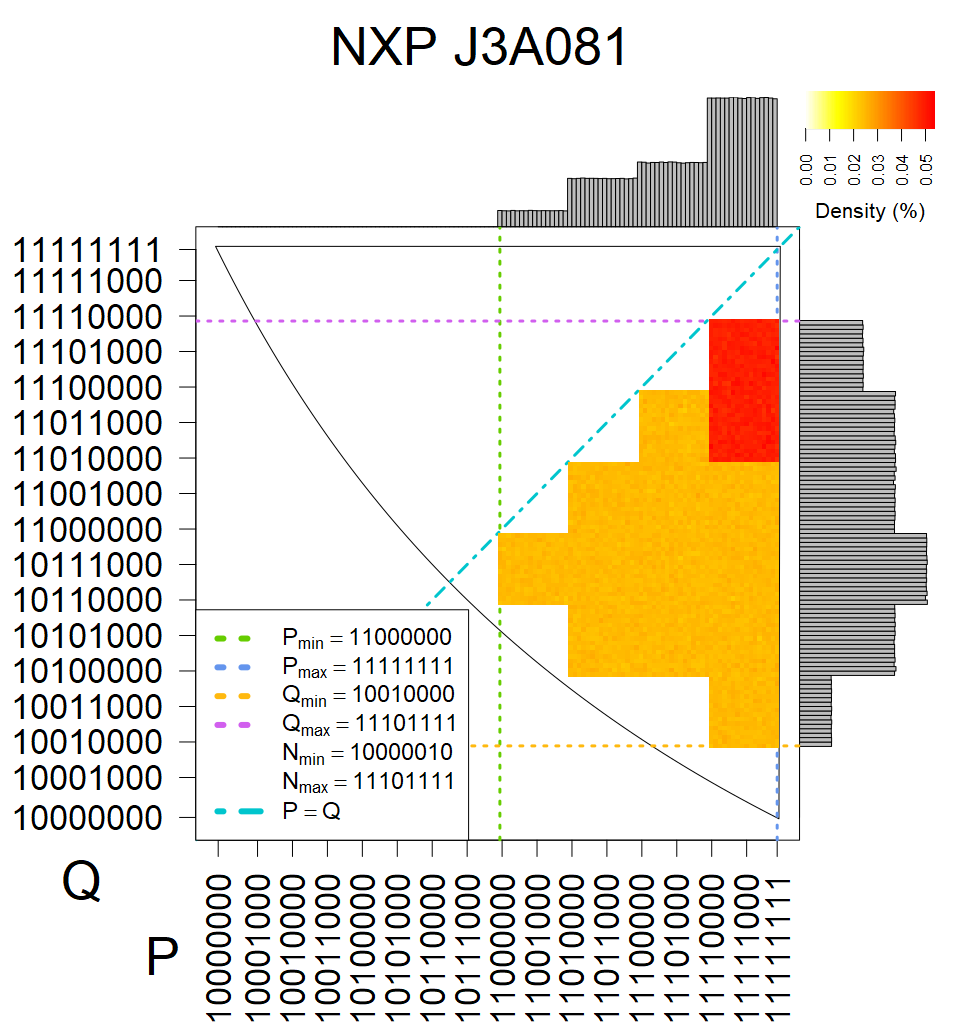
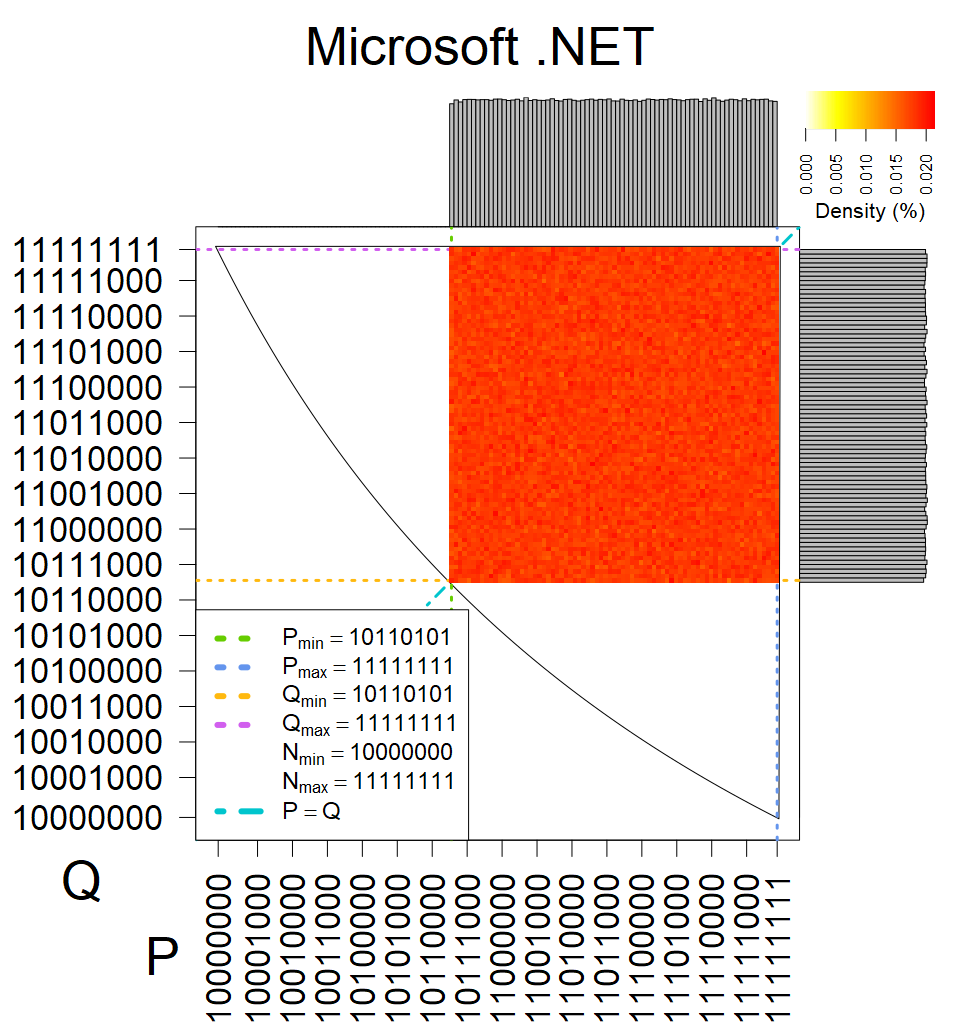
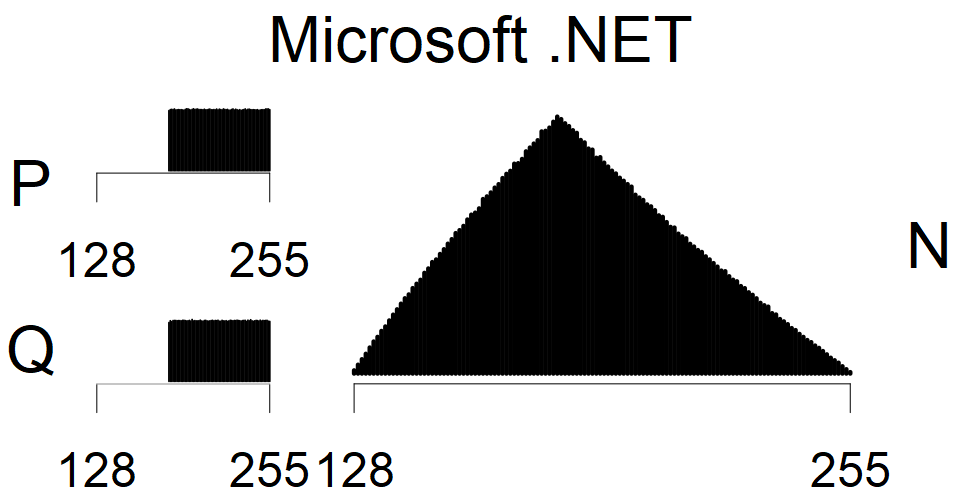
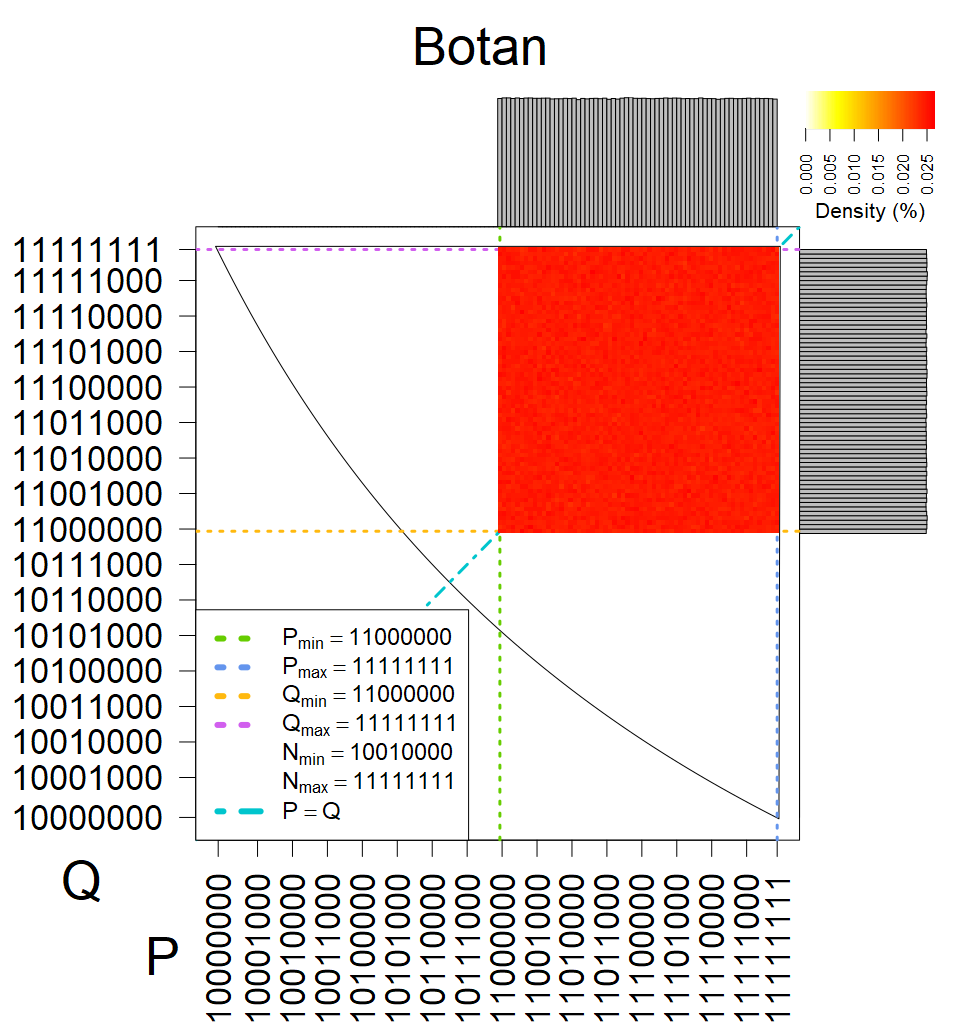
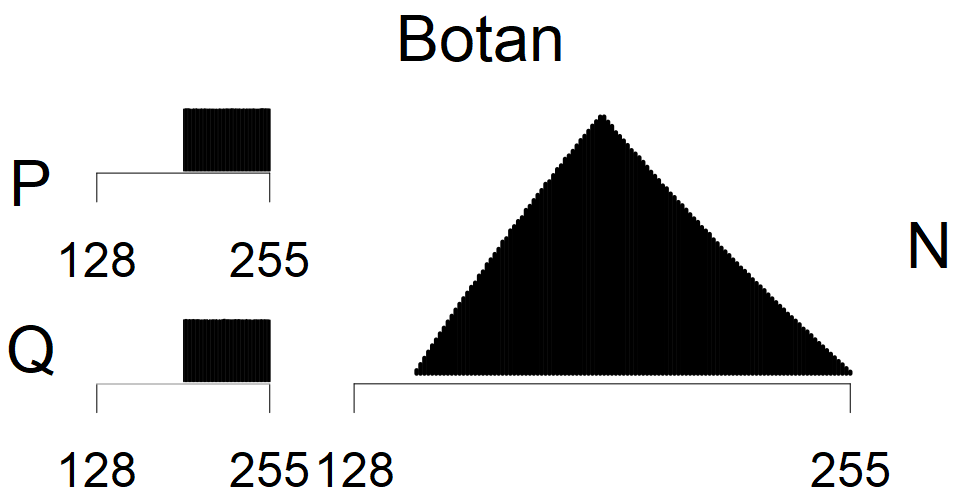
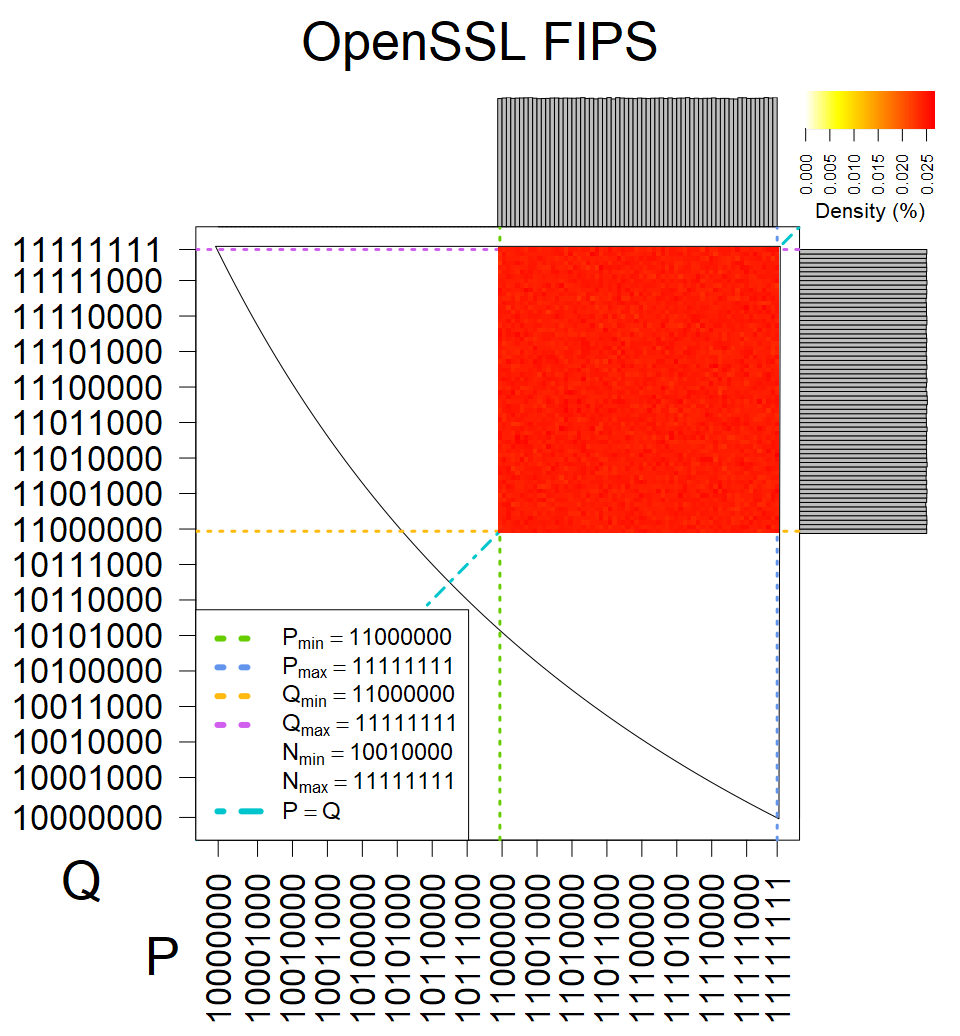
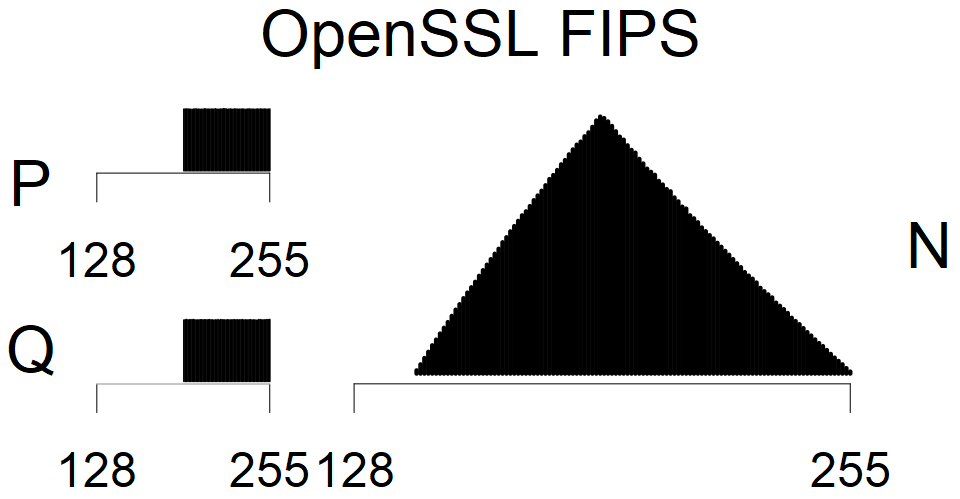
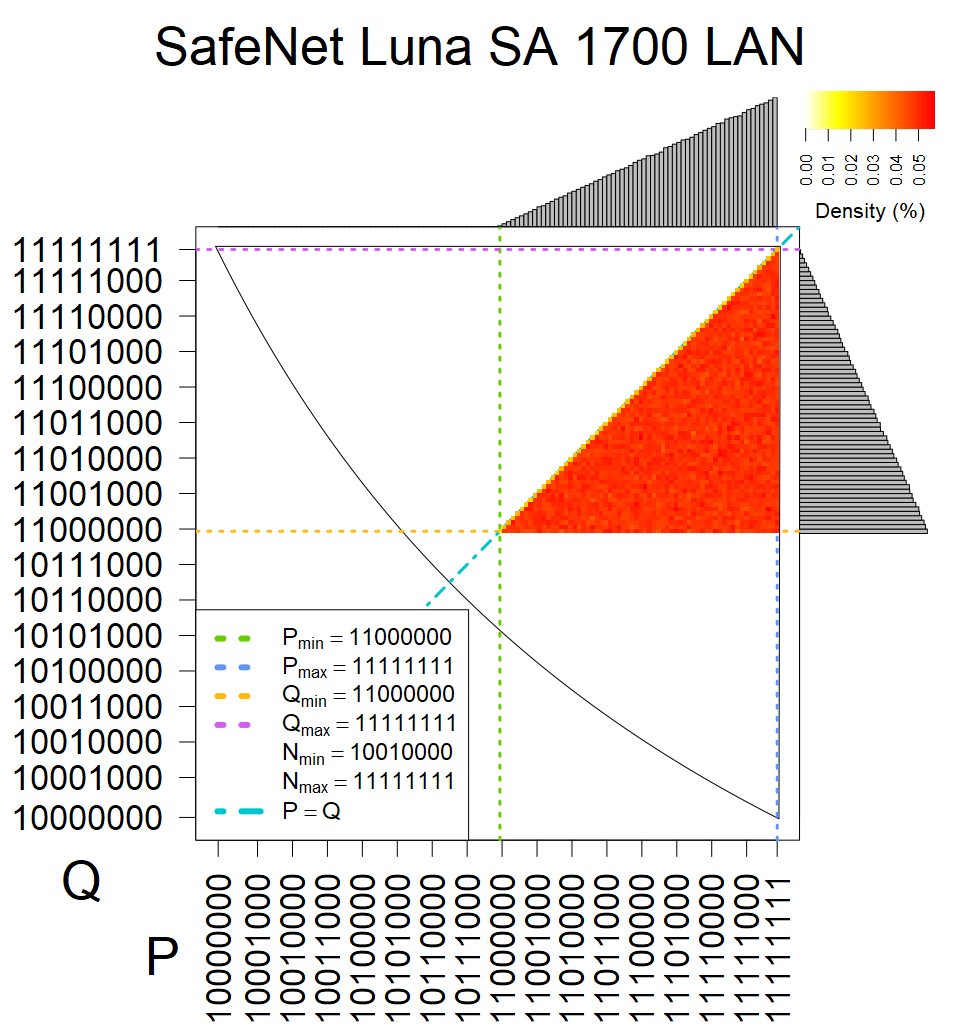
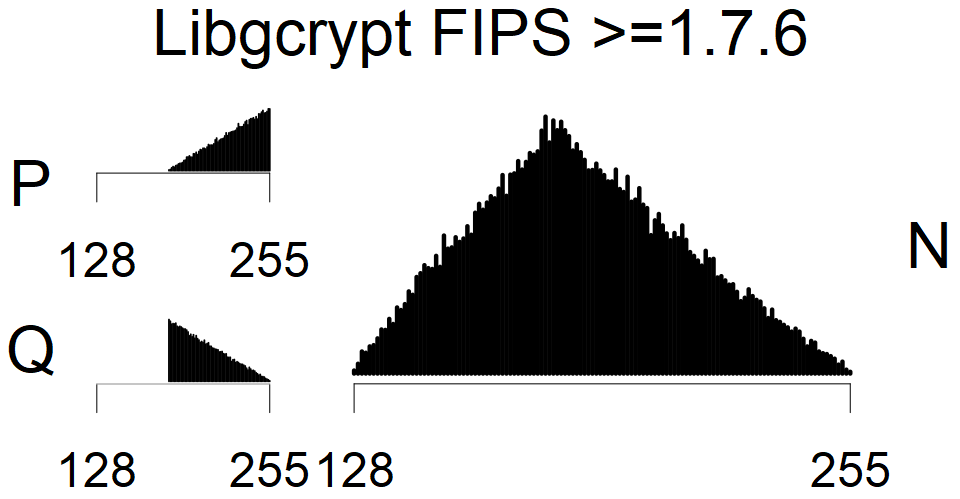
The most popular source in IPv4 TLS certificates scans. Special fingerprint on p-1 and q-1 values, but for classification we use only bias observed on modulus mod 3 and the second most significant bit.
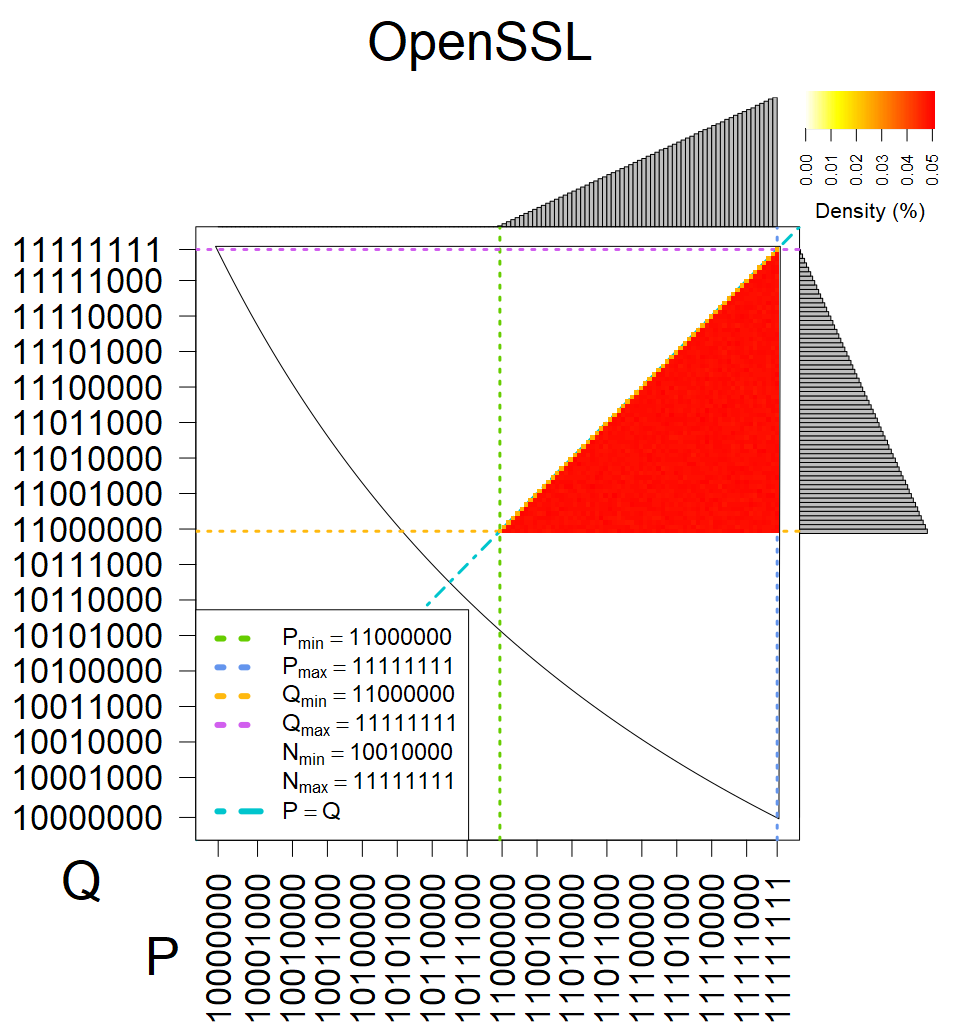
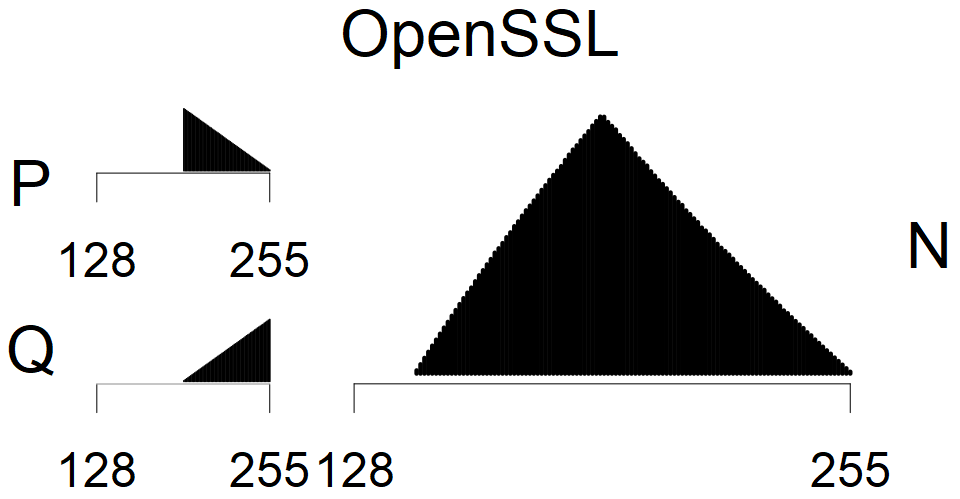
| Software library | |
|---|---|
| Tested versions: | 0.9.7, 1.0.2e, 1.0.2g, 1.0.2k, 1.1.0e |
| Number of keys: | 13,860,000 |
| Raw keys: | Link |
Group VIII
Only the one source that do not restrict modulus size and generates also smaller keys.
Group IX
Source similar to group XVII but with slightly biased modulus mod 3.
Group X
Randomly generated prime p, but biased prime q.
Group XIV
Special proprietary implementation with non-uniform and unique distribution of primes. Biased modulus mod 4.
Group XV
Sources without biased modulus mod 3 or 4, but with slightly limited range of primes.
Group XVI
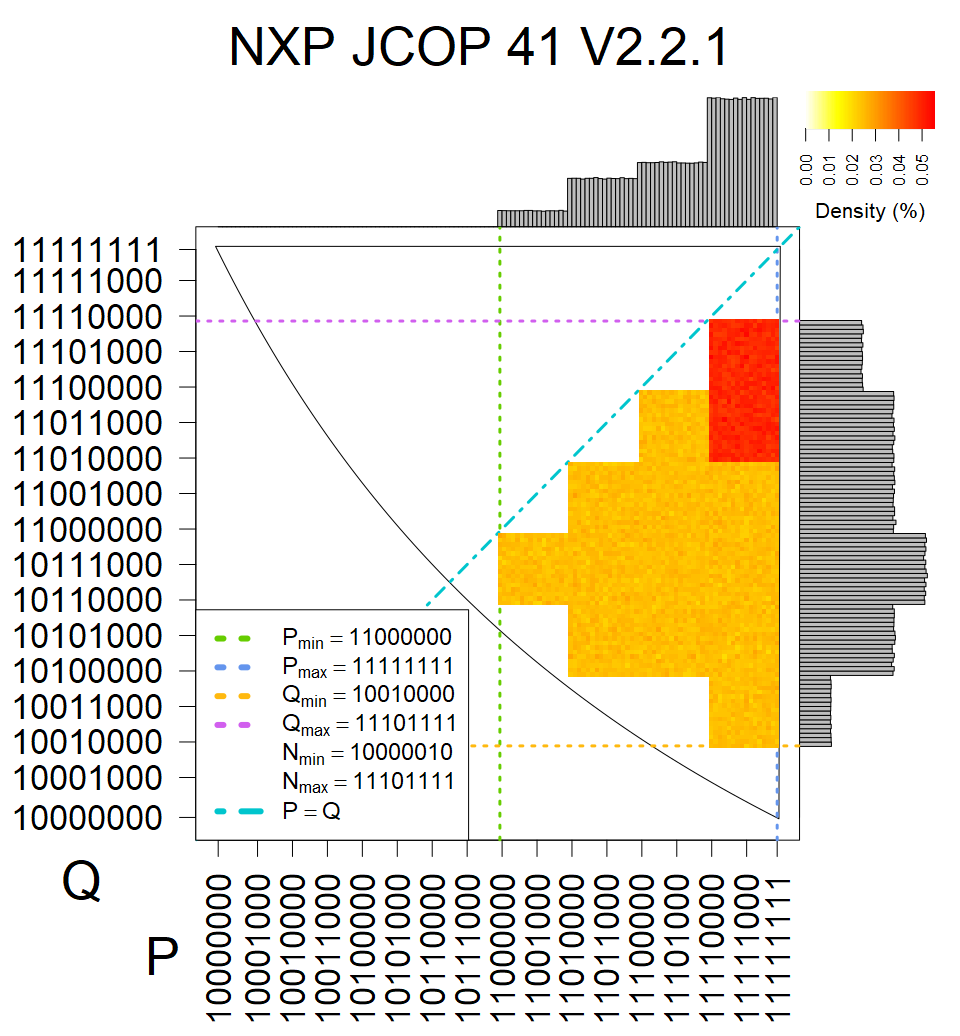
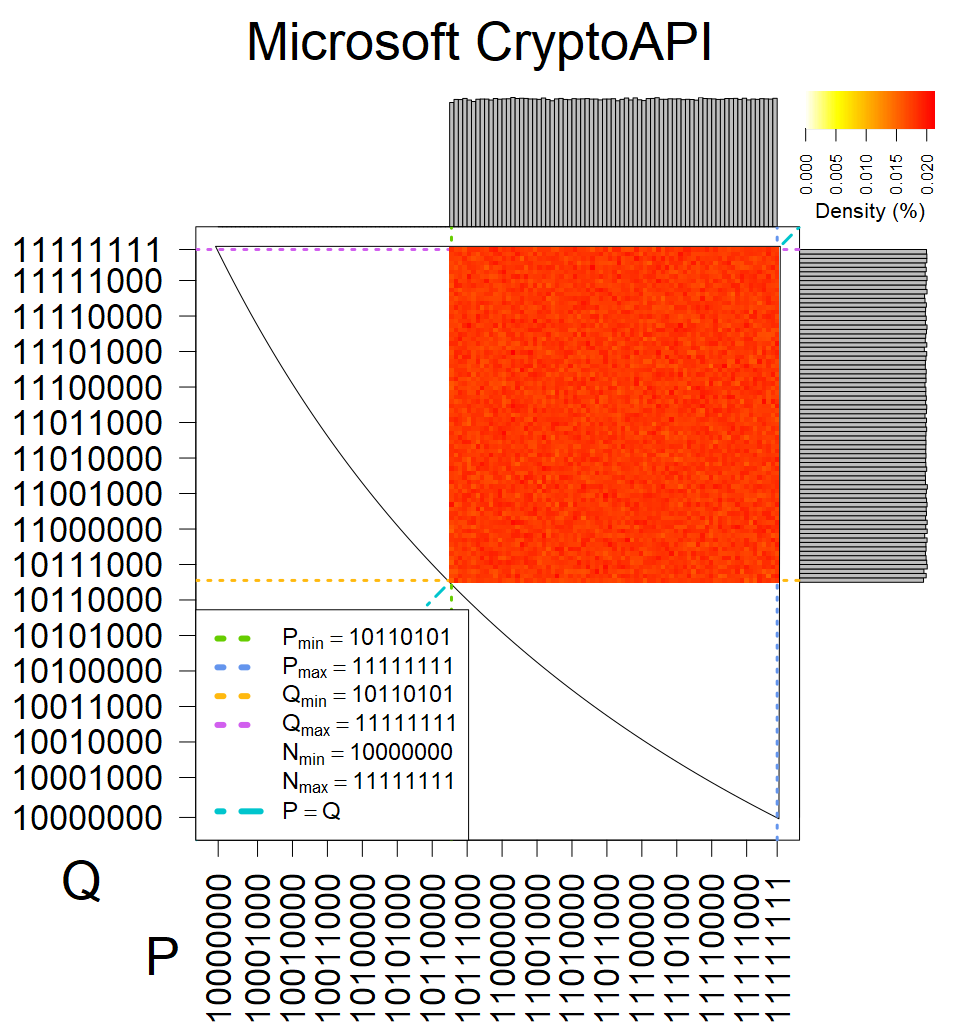
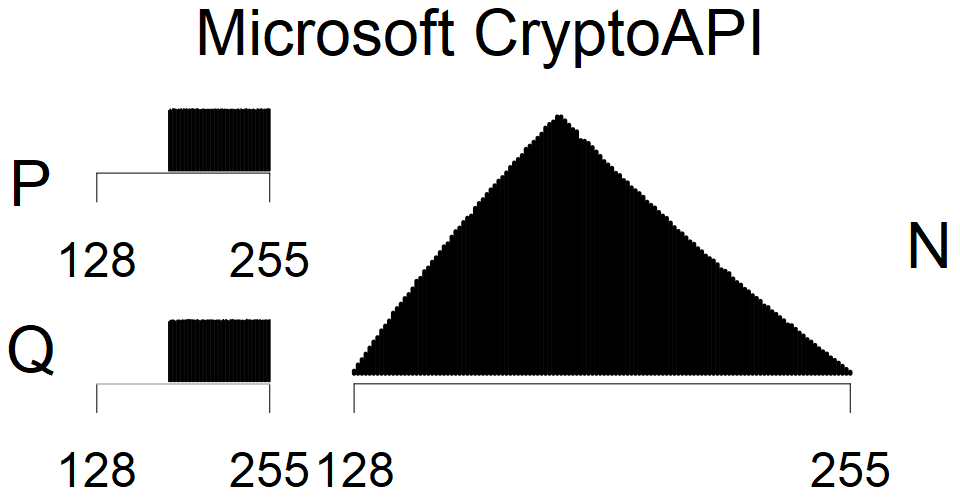
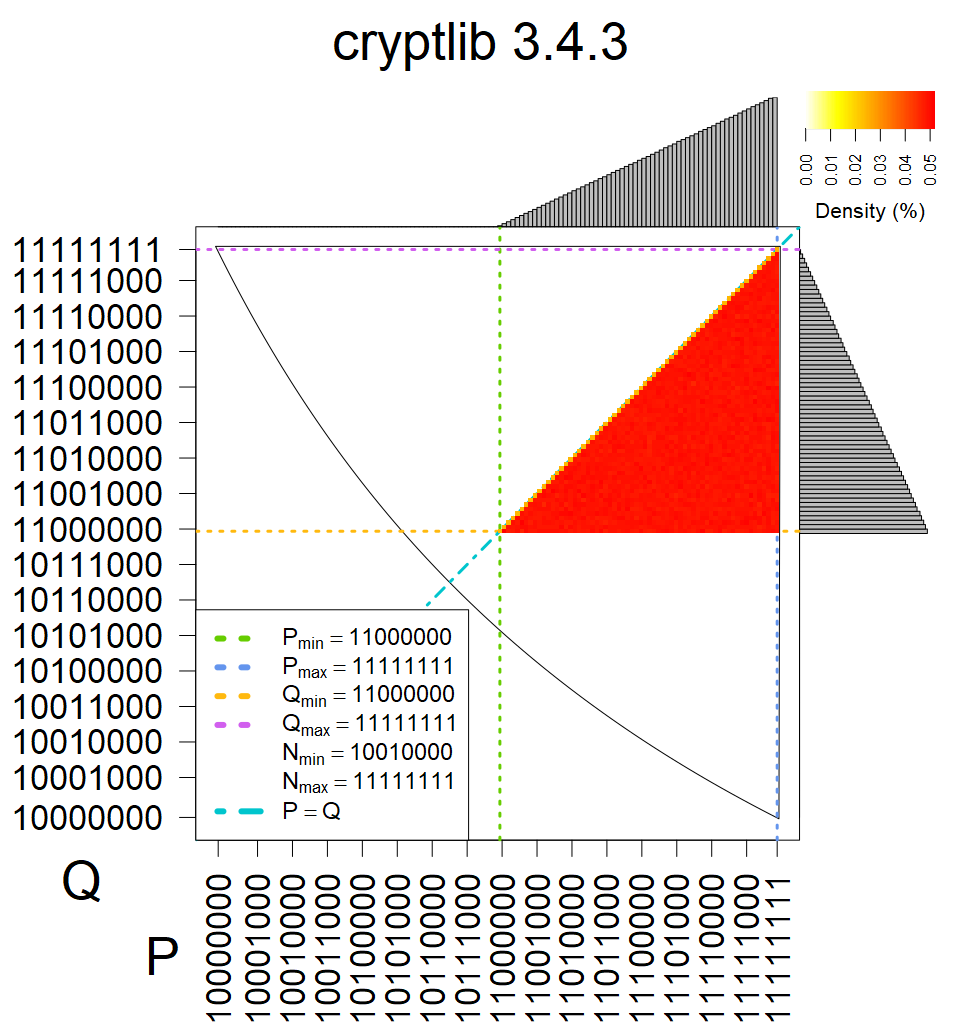
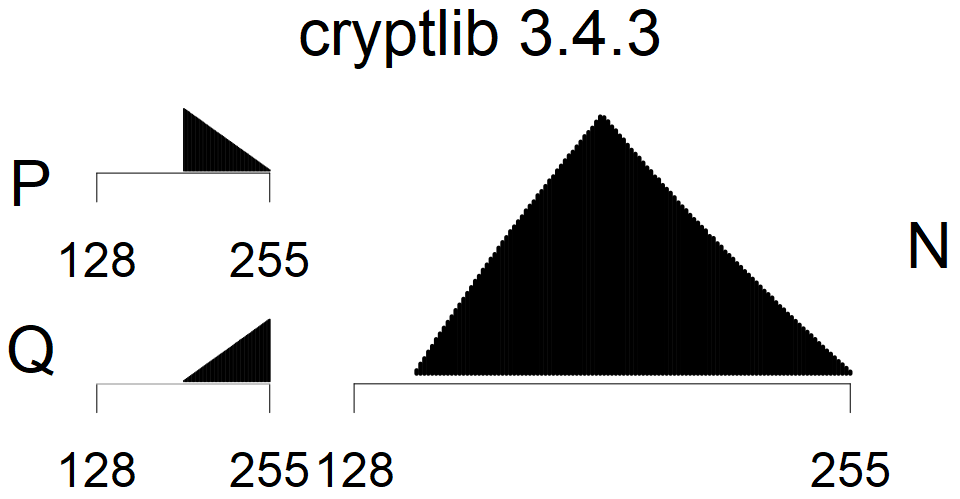
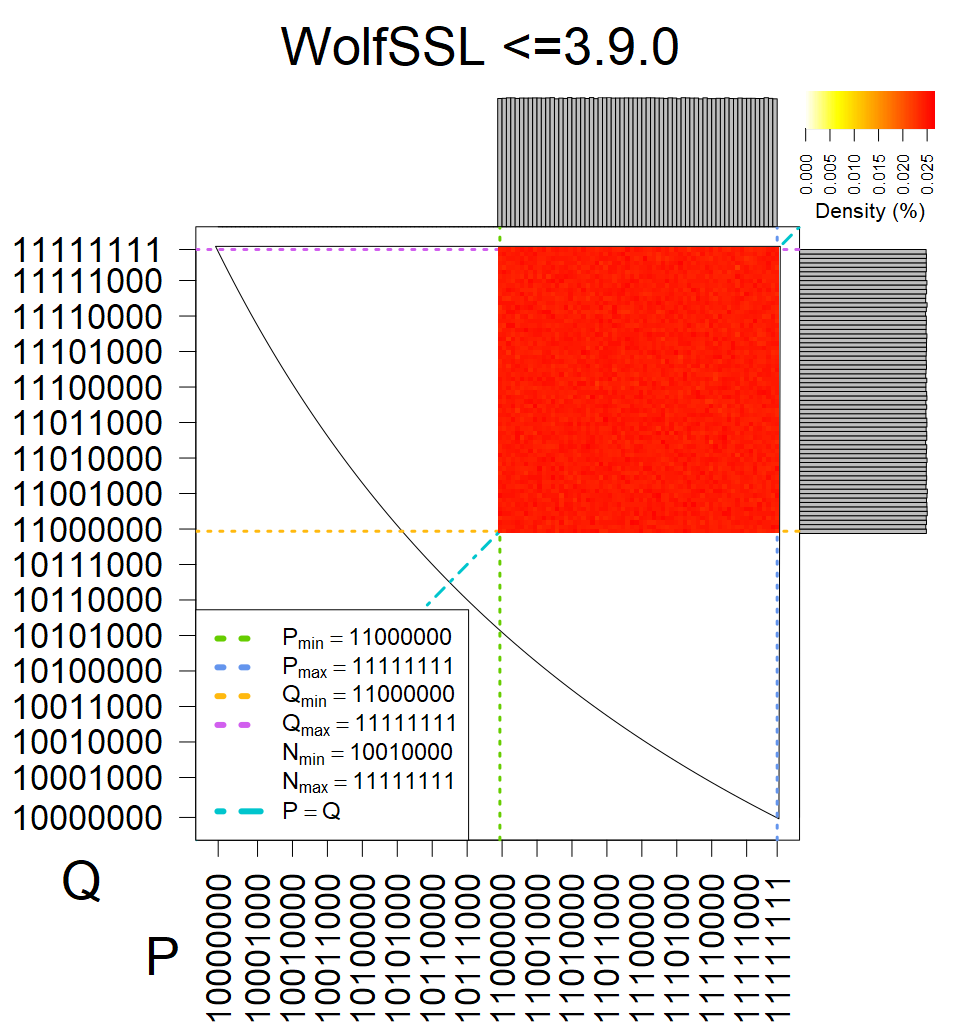
Full range of primes used, condition only on the length of product modulus. Without bias on modulus mod 3 or 4. Sources Bouncy Castle <=1.53 and SunRsaSign have different distribution of primes but not enough for web classification (it will cause misclassification and lower accuracy), but for continuous monitoring of large datasets, they form separated group.
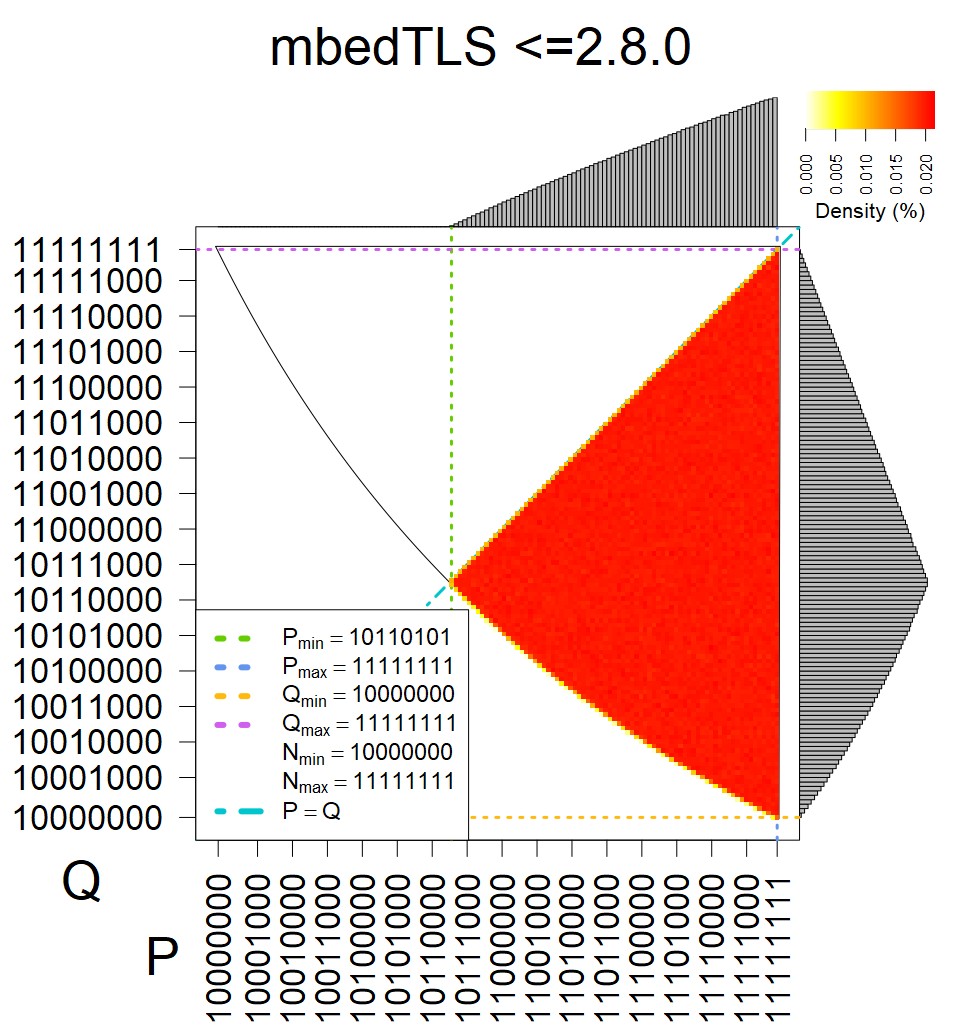
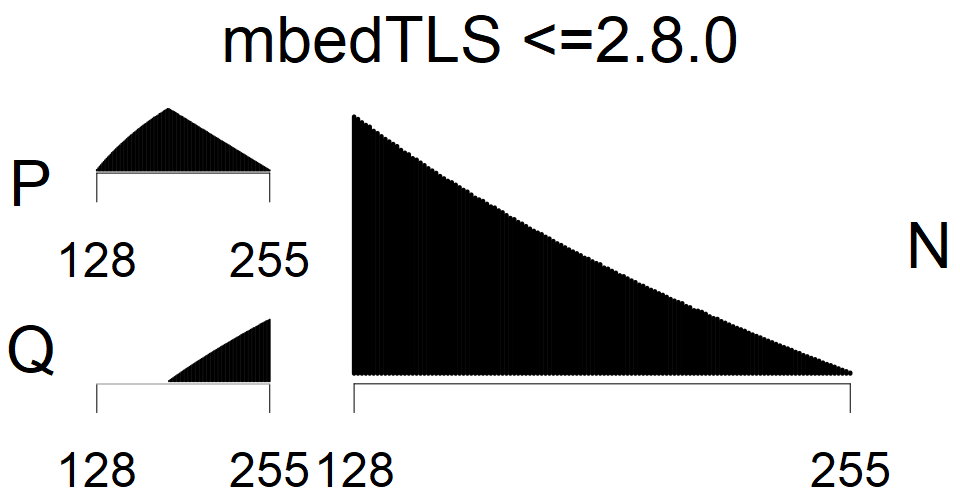
| Software library | |
|---|---|
| Tested versions: | 0.10., 1.3.19, 2.2.1, 2.4.2 |
| Number of keys: | 11,550,000 |
| Raw keys: | Link |
Group XVII
Top two bits of primes set to one. No bias in modulus mod 3 or 4.
Other sources
We have less then 100,000 keys from these sources, therefore they were not used in statistical model. We can assume, that YubiKey NEO shares the implementation with cards from group XII, Athena IDProtect is similar to sources from group XVII, and from some statistics, we assume that Libgcrypt FIPS 1.7.6 forms unique group.